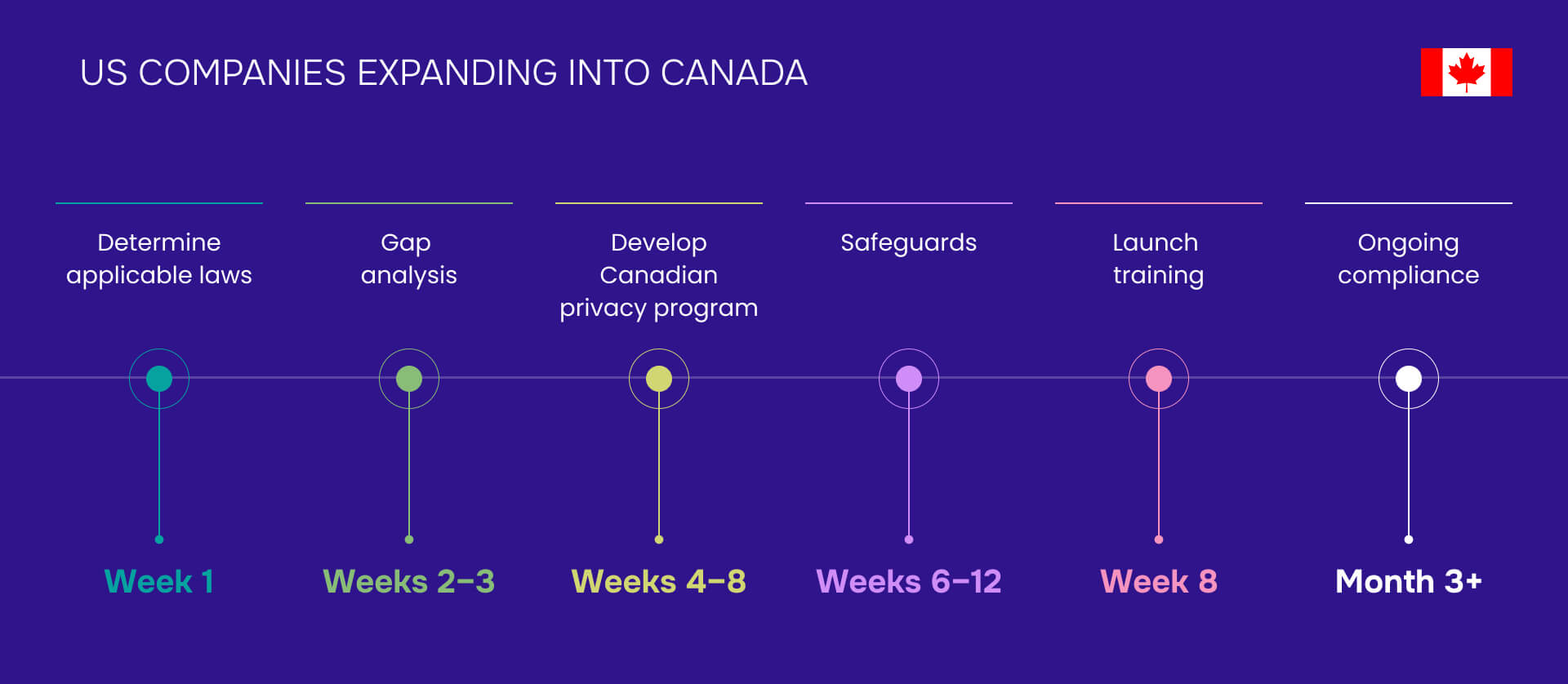
HIPAA in Canada doesn't apply - except when it absolutely does. If you're a U.S. company expanding north or a Canadian business serving American patients, you're navigating one of healthcare privacy's most misunderstood compliance challenges.
A single HIPAA violation cost Anthem Inc. $16 million. Meanwhile, Canada's LifeLabs breach affected 15 million people and resulted in $0 in regulatory fines—though class action settlements in Canadian courts reached nearly $10 million. This enforcement gap creates a dangerous illusion that privacy compliance matters less in Canada. With major breach costs reaching $10+ million, class action lawsuits mounting, and new enforcement powers taking effect, Canadian healthcare privacy demands urgent attention - just for entirely different reasons than HIPAA law.
This guide reveals the surprising truths about HIPAA regulations in Canada, the costly mistakes companies make at the US-Canada border, and exactly what you need to achieve HIPAA compliance in 2025.
Does HIPAA apply in Canada? The jurisdictional paradox
The fundamental question isn't "where is the data?" It's "whose data is it?"

HHS is clear on this: HIPAA law is U.S. federal law with U.S. territorial jurisdiction. It does not apply within Canada's borders to Canadian patients receiving care from Canadian providers.
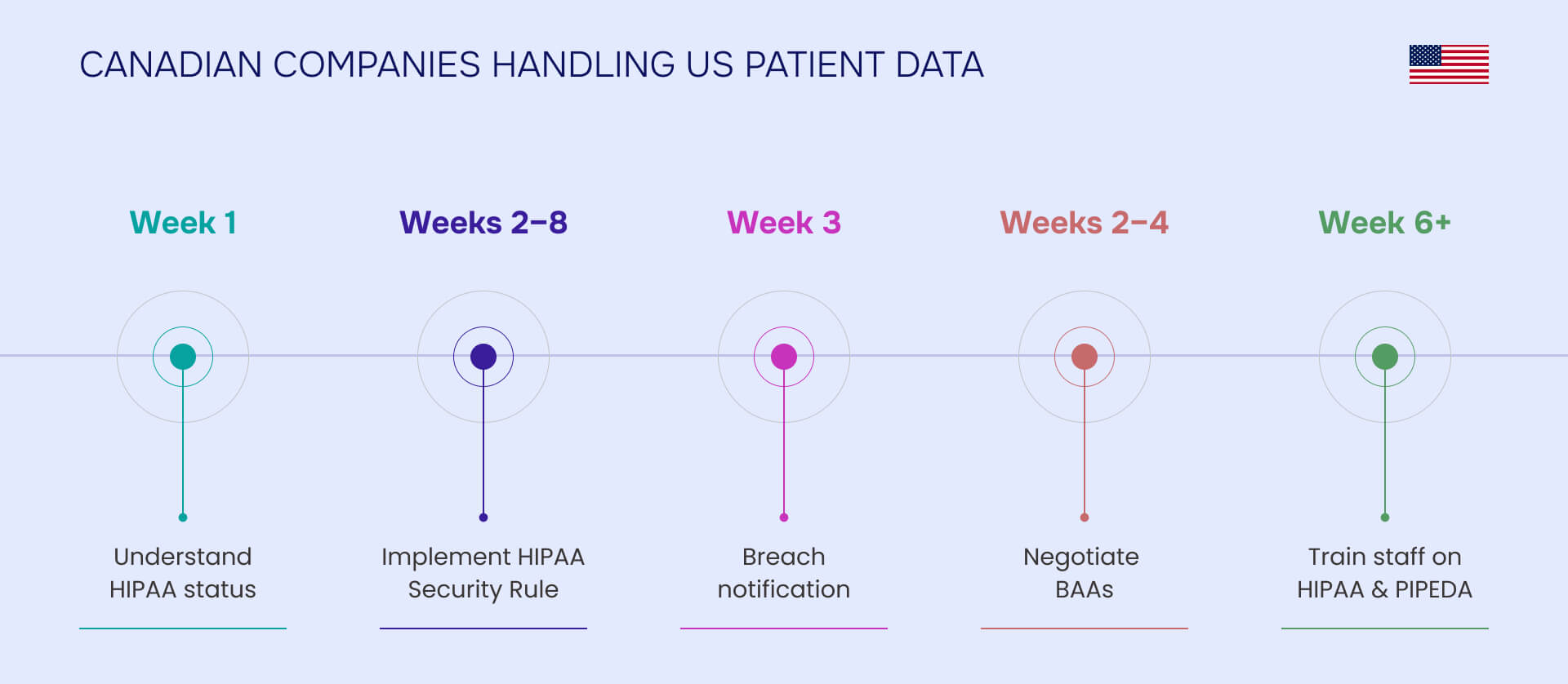
The critical exception: HIPAA Canada compliance absolutely applies to any entity - regardless of location - that handles U.S. patient protected health information (PHI).
A Canadian telemedicine provider treating U.S. patients via virtual care must comply with HIPAA. A Canadian healthcare technology vendor providing services to U.S. hospitals becomes a HIPAA business associate. Canadian research organizations participating in U.S. clinical trials, medical device manufacturers processing data from U.S. patients, or any Canadian company acting as a business associate to a U.S. covered entity - all subject to HIPAA compliance Canada requirements.
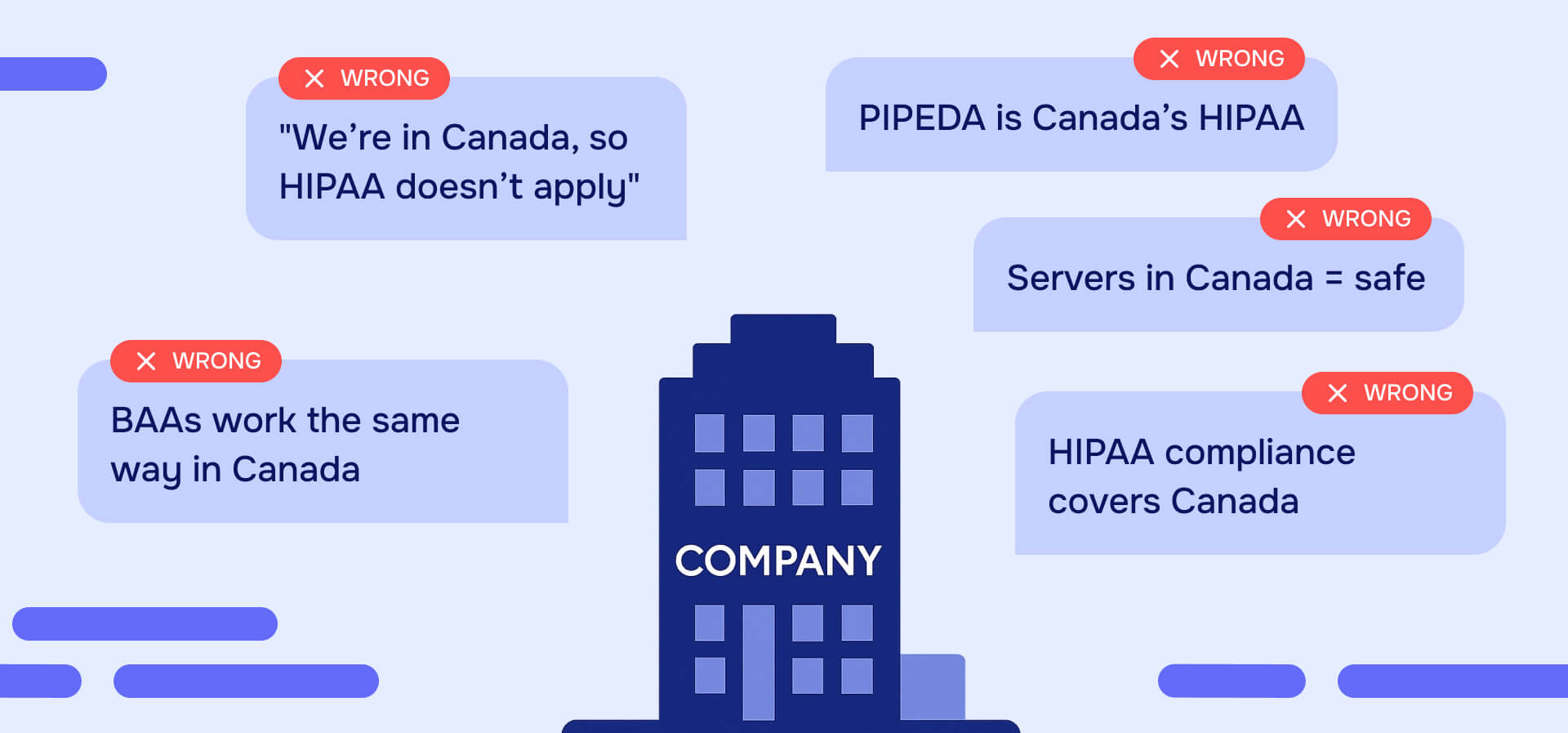
The location trap reveals the core misconception: U.S. patient data stored on Canadian servers by a Canadian company using Canadian employees is still subject to HIPAA. The patient's nationality and the data's origin matter more than the server's physical location or your company's headquarters.
The reverse scenario works the same way: Canadian patient data stored in U.S. data centers remains subject to Canadian privacy laws (PIPEDA, provincial health acts). Location of infrastructure doesn't change jurisdictional requirements.
Cross-border healthcare businesses face simultaneous compliance with HIPAA for U.S. patients AND Canadian privacy laws for Canadian patients, with completely different consent models, breach notification requirements, and enforcement mechanisms.
Canada's HIPAA equivalents: The patchwork system
Canada doesn't have a single "HIPAA equivalent." Instead, a complex network of federal and provincial laws together regulates healthcare privacy.
PIPEDA: Canada's federal privacy foundation
The Personal Information Protection and Electronic Documents Act (PIPEDA) is often compared to HIPAA, but this comparison misleads. PIPEDA is actually more similar to Europe's GDPR than to HIPAA law.
While HIPAA is sector-specific healthcare legislation, PIPEDA applies to ALL personal information (not just health data) across ALL commercial activities in Canada. It covers private sector organizations collecting, using, or disclosing personal information in commercial activities, extends to federally-regulated businesses (banks, airlines, telecommunications) including their employee data, and applies to cross-border and interprovincial data transfers. PIPEDA does not apply to employee information in provincially regulated organizations—provincial employment privacy laws govern those relationships instead.
PIPEDA's 10 Fair Information Principles establish requirements for accountability, identifying purposes, consent, limiting collection/use/disclosure/retention, accuracy, safeguards, openness, individual access, and challenging compliance.
Since November 2018, organizations must report breaches creating "real risk of significant harm" to the Privacy Commissioner of Canada, affected individuals, and other organizations that can reduce risk—all "as soon as feasible." ALL breaches must be documented and retained for 24 months minimum, regardless of reporting thresholds.
The enforcement reality: The Office of the Privacy Commissioner of Canada (OPC) cannot impose fines for most violations. Maximum penalties of $100,000 apply only to three specific criminal offenses (destroying information, retaliation, obstruction). The OPC issues findings, recommendations, and compliance orders instead.
Which provincial laws apply to your organization?
Ten provinces and three territories have enacted their own health privacy legislation. When provincial law is deemed "substantially similar," it applies INSTEAD of PIPEDA for within-province activities. PIPEDA still applies to cross-border and interprovincial transfers.
"Substantially similar" provinces include Ontario (PHIPA), British Columbia (PIPA), Alberta (PIPA), New Brunswick (PHIPAA), Newfoundland and Labrador (PHIA), Nova Scotia (PHIA), and Quebec (Law 25). Manitoba, Saskatchewan, and Prince Edward Island require dual compliance with both provincial and federal law.
Provincial differences create operational challenges. Ontario requires express consent for disclosure to non-custodians but accepts implied consent for care, mandates 30-day access request response, with organizational penalties up to $1 million. Quebec enforces the strictest privacy regime in North America—now exceeding even HIPAA's burdens. As of 2025, Quebec Law 25 is fully in force with mandatory privacy officers, mandatory Privacy Impact Assessments for high-risk activities, breach reporting within 72 hours when risk of serious injury exists, Transfer Risk Assessments required for all data leaving Quebec (even to other Canadian provinces), and penalties up to $25 million or 4% of global revenue, whichever is higher. Manitoba permits express or implied consent, requires 24-hour response for in-patients or 72 hours for current care, with penalties of $50,000 per violation.
A national Canadian healthcare company must comply with multiple different provincial laws simultaneously, each with distinct requirements.
HIPAA vs Canadian privacy laws: Critical differences
Frequently asked questions
HIPAA applies to any organization that handles U.S. patient PHI, regardless of location. Canadian companies providing services to U.S. covered entities, treating U.S. patients, or participating in U.S. clinical trials become HIPAA business associates and must comply with full HIPAA Security and Privacy Rules, subject to OCR enforcement and penalties.
No. HIPAA compliance does not satisfy Canadian privacy requirements. The consent models are fundamentally different - HIPAA's notice-based approach won't meet Canada's consent-first framework. Breach notification thresholds differ. PIPEDA applies to all personal information including employee data for federally-regulated businesses, while HIPAA doesn't generally cover employee PHI. You need separate compliance programs.
It depends on your jurisdiction and sector. Federally-regulated businesses (banks, airlines, telecommunications) face PIPEDA nationwide. Organizations operating entirely within a province with "substantially similar" law comply with provincial law (Ontario PHIPA, BC PIPA, Alberta PIPA, Quebec Law 25, etc.). Manitoba, Saskatchewan, and Prince Edward Island require dual compliance with both provincial and federal law. Cross-border and interprovincial data transfers trigger PIPEDA regardless of provincial law.
Assuming server location determines jurisdiction. U.S. patient data stored on Canadian servers by a Canadian company is still subject to HIPAA. Canadian patient data stored in U.S. data centers remains subject to Canadian privacy laws. The patient's nationality and data's origin matter more than infrastructure location. Companies also frequently roll out U.S. privacy programs unchanged in Canada, creating immediate violations.
The Office of the Privacy Commissioner of Canada cannot impose fines for most violations—maximum penalties of $100,000 apply only to three specific criminal offenses. Provincial commissioners in most provinces (except Quebec and Ontario) lack direct fine authority. Canadian courts and class action lawsuits have become the de facto enforcement mechanism. The LifeLabs breach affected 15 million people with $0 in regulatory fines but nearly $10 million in class action settlements.
Quebec Law 25 creates the strictest privacy regime in North America with mandatory privacy officers, mandatory Privacy Impact Assessments for high-risk activities, breach reporting within 72 hours when risk of serious injury exists, Transfer Risk Assessments required for all data leaving Quebec (even to other Canadian provinces), and penalties up to $25 million or 4% of global revenue, whichever is higher. These requirements often exceed HIPAA's burdens and mirror GDPR's enforcement model.
Maintain separate consent workflows. For U.S. patients under HIPAA, Notice of Privacy Practices with permitted uses for treatment, payment, and healthcare operations. For Canadian patients, obtain express consent before collecting sensitive health data, identify purposes before or during collection, and allow consent withdrawal at any time. Best practice: segregate data and processes to maintain clear compliance boundaries.
Breach response, recovery, legal fees, and notification costs average $10+ million per incident. Class action settlements can reach millions (LifeLabs: nearly $10M). Reputational damage affects patient acquisition and retention. Professional regulatory consequences impact licensing. U.S. operations face OCR enforcement with penalties reaching millions per violation. The regulatory enforcement gap doesn't eliminate financial exposure - it just shifts it to civil liability.
The redaction requirements are similar, but documentation differs. Both require permanent removal of identifiers, not just visual masking. HIPAA has a de-identification safe harbor; Canada doesn't—even anonymized health data may remain protected. Health Canada's PRCI guidelines require documented risk assessments and audit trails for regulatory submissions. Professional redaction software with guaranteed metadata removal, comprehensive audit trails, and compliance-ready certificates satisfies both U.S. and Canadian requirements.
Yes, but with important caveats. The U.S. CLOUD Act allows American authorities to access data stored by U.S. companies anywhere in the world, even on Canadian servers. This may violate Canadian privacy laws requiring protection against foreign access, particularly concerning for provinces with data residency restrictions (BC, Nova Scotia public sector; Quebec's heightened requirements). Mitigation strategies include encryption with customer-controlled keys, contractual provisions requiring notification of government access requests, and conducting Transfer Risk Assessments (required in Quebec).
More About
Data Privacy
Start Redacting in Seconds
No credit card required
Start redacting for free
Cancel any time