A Tennessee-based retailer just paid $1.35 million for violating California privacy law. No California headquarters. No California stores mentioned in the violation. Just customers - which is all it takes. Over 500,000 U.S. businesses now fall under CCPA regulations, most with zero physical presence in California.
The geographic reach surprises most business owners. If you sell online to California residents, process job applications from California candidates, or maintain a website accessible to California consumers, California law applies to you. Revenue thresholds, data volume, or percentage of income from data sales determine compliance obligations - not whether you've ever set foot in the state.
Enforcement is now aggressive. The California Attorney General and California Privacy Protection Agency have hundreds of active investigations. Penalties reach $7,988 per violation for intentional breaches. Settlements have hit $1.55 million for a single company. The private right of action lets consumers sue for $107 to $799 per person when breaches involve inadequate security.
In some cases processing of CCPA compliance requests costs reach over $1,000 per request when accounting for staff time, system queries, legal review, and cross-departmental coordination. Organizations with large California customer bases spend hundreds of thousands annually just responding to access and deletion requests—before investing in the infrastructure to prevent violations.
This CCPA Compliance guide explains who must comply with CCPA, what is CCPA compliance, and how to comply with CCPA across legal, government, real estate, HR, healthcare, and insurance sectors meet their obligations while avoiding enforcement actions.
What is CCPA compliance
The California Consumer Privacy Act of 2018 (CCPA) took effect January 1, 2020, as the first comprehensive consumer privacy law in the United States. California residents gained control over their personal information that consumers in most states still lack: the right to know what data businesses collect, access and delete that data, and opt out of its sale or sharing.
The California Privacy Rights Act (CPRA), passed by voters in November 2020, expanded these protections. CPRA took effect January 1, 2023, with enforcement beginning July 1, 2023. The amendments created a dedicated enforcement agency (the California Privacy Protection Agency), added rights to correct inaccurate information and limit use of sensitive data, and raised data volume thresholds from 50,000 to 100,000 consumers.
CCPA compliance means implementing systems, policies, and procedures to meet statutory obligations for collecting, processing, sharing, and securing California residents' personal information. Businesses must respond to consumer requests within mandated timeframes, maintain required disclosures, honor opt-out signals, implement reasonable security measures, and provide audit trails.
The law reaches beyond California's borders. Any business serving California residents that meets applicability thresholds must comply, regardless of physical location. A New York company with no California offices but selling online to California consumers falls under CCPA when crossing revenue or data volume thresholds.
Who must comply with CCPA
CCPA regulations has extraterritorial application. No physical presence in California is required - the law reaches any business worldwide that meets the criteria.

A business must comply if it meets these four foundational requirements:
- Is organized or operated for profit
- Does business in California
- Collects consumers' personal information
- Determines purposes and means of processing
AND meets at least ONE of these thresholds:
Revenue threshold: $26,625,000 annually
As of January 1, 2025, businesses with annual gross revenues of $26,625,000 or more must comply. This figure, adjusted from the original $25 million threshold, increases every odd year based on the Consumer Price Index.
This is worldwide revenue, not California-specific revenue. A company with $30 million in total revenue but only $2 million from California customers still meets this threshold.
Data volume threshold: 100,000+ California residents or households
Businesses that annually buy, sell, OR share the personal information of 100,000 or more California residents or households must comply. This threshold increased from 50,000 under the original CCPA.
This count includes individuals, households, OR devices. A company that retargets ads to 75,000 California residents and shares behavioral data with advertising partners for 30,000 additional residents has crossed the 100,000 threshold. Interest-based advertising and behavioral targeting both count toward this total.
Revenue from data threshold: 50%+ from selling or sharing personal information
Businesses deriving 50 percent or more of annual revenues from selling OR sharing consumers' personal information must comply. CCPA regulations defines "sale" broadly to include transfers for "valuable consideration"—not just direct monetary payment. This includes revenue connected to behavioral advertising, data brokerage, and marketing cooperatives.
What "does business in California" means
The California Attorney General has clarified that businesses "do business" in California through:
- Operating a website accessible to California residents
- Selling products or services to California residents (online or offline)
- Having employees working in California
- Paying California state taxes
- Conducting any transactions for financial gain within California
A software company based in Texas that sells cloud services to California customers through its website is doing business in California. An e-commerce retailer in Florida that ships products to California addresses is doing business in California. A consulting firm in Illinois with a single remote employee working from their home in Sacramento is doing business in California.
Over 500,000 U.S. businesses could be subject to CCPA under these broad applicability standards—the majority with no physical California presence.
What is personal information under CCPA
CCPA defines personal information as "information that identifies, relates to, describes, is reasonably capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or household."
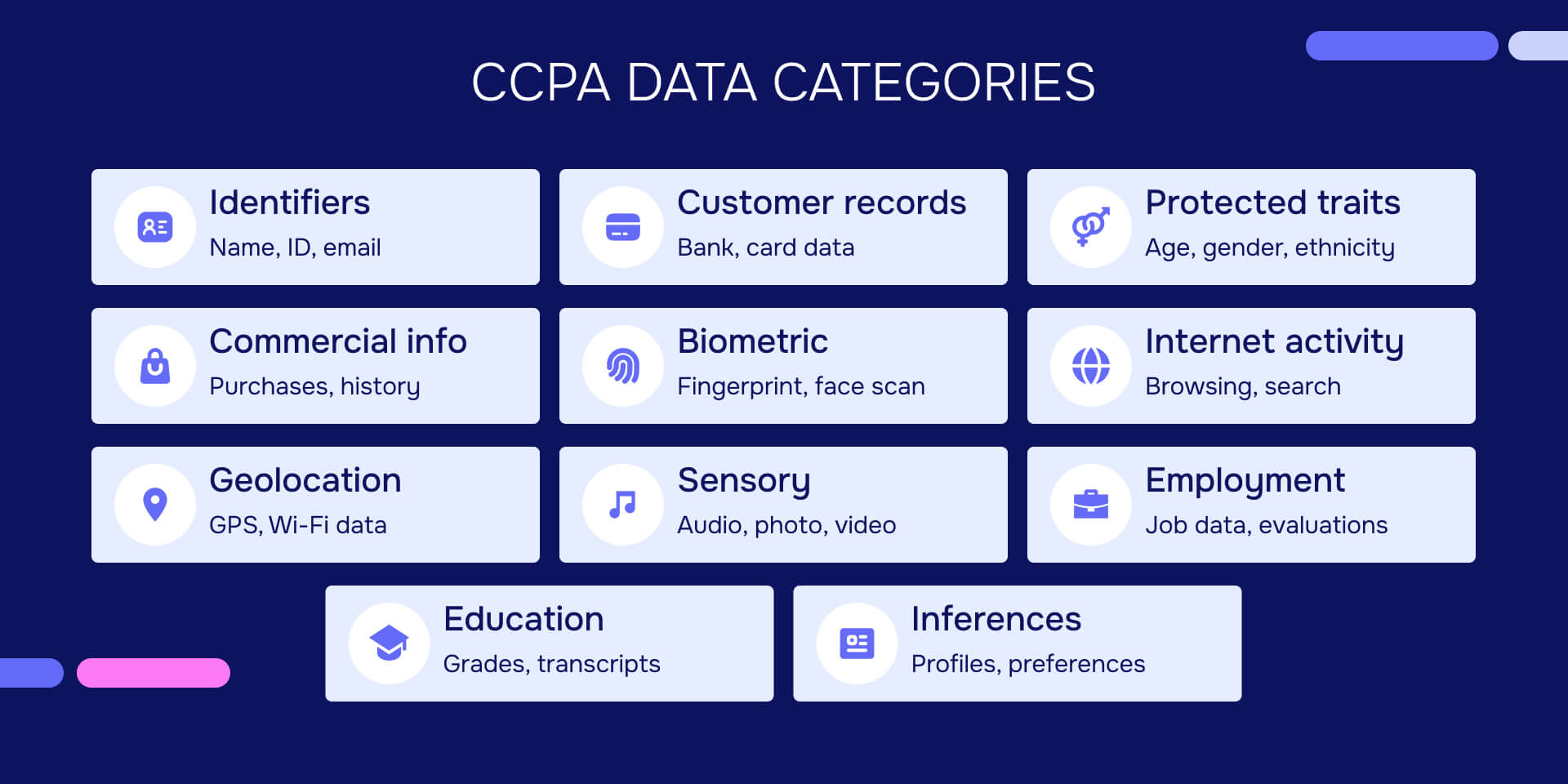
This definition is intentionally broad. The law enumerates 11 categories of personal information:
Category A - Identifiers: Real names, aliases, postal addresses, unique personal identifiers, online identifiers, IP addresses, email addresses, account names, Social Security numbers, driver's license numbers, passport numbers, and similar identifiers.
Category B - Customer records: Names, signatures, physical characteristics, addresses, telephone numbers, bank account numbers, credit card numbers, debit card numbers, medical information, and health insurance information.
Category C - Protected classification characteristics: Age, race, color, ancestry, national origin, citizenship, religion, marital status, sex, gender, gender identity, pregnancy status, sexual orientation, veteran status, medical conditions, disabilities, and genetic information.
Category D - Commercial information: Records of products or services purchased, obtained, or considered, and purchasing or consuming histories or tendencies.
Category E - Biometric information: Genetic, physiological, behavioral, or biological characteristics including fingerprints, faceprints, voiceprints, iris or retina scans, keystroke patterns, gait patterns, and sleep, health, or exercise data that can identify an individual.
Category F - Internet or network activity: Browsing history, search history, and information regarding interaction with websites, applications, or advertisements.
Category G - Geolocation data: Physical location or movements derived from GPS, Wi-Fi, or cell tower triangulation.
Category H - Sensory data: Audio, electronic, visual, thermal, or olfactory information, including call recordings, photographs, video surveillance, and thermal imaging.
Category I - Professional or employment information: Current or past job history, performance evaluations, and disciplinary records.
Category J - Non-public education information: Education records under the Family Educational Rights and Privacy Act (FERPA), including grades, transcripts, class lists, schedules, and financial information.
Category K - Inferences: Inferences drawn from any of the above categories to create profiles reflecting preferences, characteristics, psychological trends, predispositions, behavior, attitudes, intelligence, abilities, or aptitudes.
Sensitive personal information
CPRA created a subset of personal information subject to heightened protections. Sensitive personal information includes:
- Social Security, driver's license, state ID, and passport numbers
- Account login credentials combined with financial account numbers and security codes
- Precise geolocation (within 1,850 feet)
- Racial or ethnic origin, religious or philosophical beliefs, union membership
- Contents of mail, email, and text messages (unless the business is the intended recipient)
- Genetic data
- Biometric information processed for unique identification purposes
- Health information
- Sex life or sexual orientation information
Consumers have the right to limit businesses' use and disclosure of their sensitive personal information to specific permitted purposes: performing services, preventing fraud and security incidents, short-term transient use, and quality verification.
Industry examples
For legal professionals, personal information includes client names, case numbers, social security numbers in discovery documents, addresses on court filings, financial information in litigation materials, and privileged communications in attorney-client correspondence.
For healthcare organizations, this encompasses patient names, medical record numbers, diagnoses, treatment histories, prescription information, health insurance details, biometric data from medical devices, and even article titles that reveal medical conditions a consumer was researching.
For HR departments, employee personal information includes names, addresses, social security numbers, performance reviews, disciplinary records, compensation information, benefits data, background check results, and job application materials. The temporary exemption for employee and business-to-business data expired December 31, 2022—all employment-related data is now fully covered under CCPA.
For real estate professionals, personal information includes client financial records, credit reports, property transaction histories, mortgage application data, income verification documents, and personal references.
For insurance companies, this covers policyholder information, claims histories, medical underwriting data, financial information, beneficiary details, and third-party liability information.
CCPA compliance requirements
CCPA regulations grants California consumers seven core rights and imposes corresponding obligations on businesses.
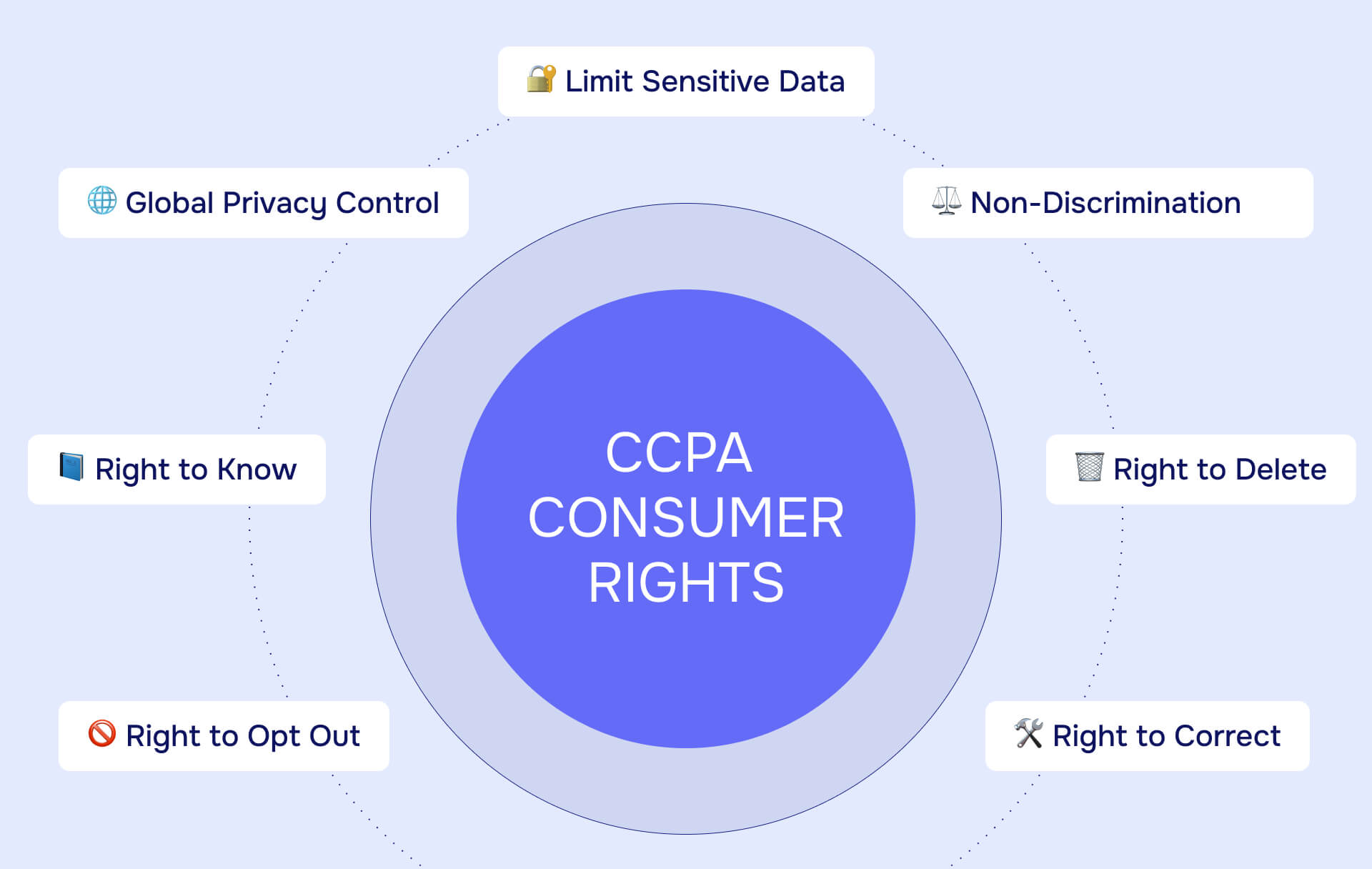
Right to know (access)
Consumers can request disclosure of:
- Categories and specific pieces of personal information the business collected about them
- Categories of sources from which the information was collected
- Business or commercial purposes for collecting, selling, or sharing that information
- Categories of third parties with whom the business shares personal information
This right covers the 12-month period preceding the request. Consumers may make these requests up to twice in any 12-month period, free of charge.
Businesses must confirm receipt within 10 business days and provide a substantive response within 45 calendar days. If additional time is needed, businesses may extend the deadline once for an additional 45 days (90 days total maximum), but must notify the consumer within the initial 45-day period with an explanation for the extension.
Right to delete
Consumers may request deletion of personal information the business collected from them, with certain exceptions. Businesses may deny deletion requests when retaining the information is necessary for:
- Completing the transaction for which the information was collected
- Detecting security incidents and protecting against malicious, deceptive, fraudulent, or illegal activity
- Debugging products to identify and repair errors
- Exercising free speech rights or ensuring others can exercise free speech
- Complying with legal obligations under California or federal law
- Using the information internally in ways reasonably aligned with consumer expectations
- Otherwise using the information internally in a lawful manner compatible with the context in which the consumer provided it
The same 10-business-day confirmation and 45-calendar-day response timeline applies.
Right to opt-out of sale or sharing
CCPA distinguishes between "sale" (transferring personal information for monetary or other valuable consideration) and "sharing" (disclosing personal information for cross-context behavioral advertising).
Consumers have the right to opt out of both. Businesses must provide a clear and conspicuous "Do Not Sell or Share My Personal Information" link on their homepage and in their privacy policy. When consumers exercise this right, businesses have 15 business days to process the request—no extension is available.
Special rules apply to minors. For consumers under 13, businesses must obtain opt-in consent from a parent or guardian before selling or sharing personal information. For consumers aged 13 to 15, businesses must obtain opt-in consent from the minor themselves. For consumers 16 and older, the standard opt-out model applies.
Right to correct inaccurate information
Under CPRA, consumers may request correction of inaccurate personal information a business maintains about them. Businesses must use commercially reasonable efforts to correct the information, considering the nature of the personal information and the purposes of processing it.
The standard 45-calendar-day response timeline applies.
Right to limit use of sensitive personal information
Consumers may direct businesses to limit use and disclosure of their sensitive personal information to only:
- Performing services or providing goods reasonably expected by an average consumer who requests those goods or services
- Preventing, detecting, and investigating security incidents
- Resisting malicious, deceptive, fraudulent, or illegal actions and prosecuting those responsible
- Ensuring physical safety of natural persons
- Short-term, transient use including non-personalized advertising shown as part of a consumer's current interaction
- Performing services on behalf of the business including maintaining accounts, customer service, processing transactions, verifying customer information, processing payments, and similar services
- Verifying or maintaining the quality or safety of a service or device
Businesses must process these requests within 15 business days.
Right to non-discrimination
Businesses cannot discriminate against consumers who exercise their CCPA rights by:
- Denying goods or services
- Charging different prices or rates for goods or services
- Providing a different level or quality of goods or services
- Suggesting the consumer will receive a different price, rate, level, or quality of goods or services
However, businesses may offer financial incentives for the collection, sale, or retention of personal information, provided the incentive is reasonably related to the value of the consumer's personal information.
Global Privacy Control recognition
Businesses must honor user-enabled opt-out preference signals—such as Global Privacy Control (GPC)—as valid requests to opt out of the sale or sharing of personal information. When a consumer enables GPC in their browser, businesses must recognize and honor that signal without requiring the consumer to take additional steps.
Despite this requirement, DataGrail analysis of 5,000+ websites found approximately 75 percent of businesses are not honoring GPC signals, firing three or more cookies despite GPC activation.
Privacy policy requirements
Businesses must maintain a privacy policy that includes:
Description of consumer rights: Instructions for exercising each of the seven core rights, with sufficient detail for consumers to understand how to submit requests.
Categories of personal information: A description of the categories collected in the preceding 12 months, categories of sources from which information was collected, business purposes for collection, sale, or sharing, and categories of third parties with whom the business shares personal information.
Sale and sharing disclosures: Categories of personal information sold or shared in the preceding 12 months, and categories disclosed for business purposes.
Retention information: How long the business retains each category of personal information, or the criteria used to determine retention periods.
Contact information: Methods consumers can use to submit requests, including at minimum a toll-free telephone number and, if the business maintains a website, a website address.
Metrics (if applicable): If processing personal information of 10 million or more California residents annually, businesses must include metrics about requests received and responses provided.
Privacy policies must be updated at least once every 12 months.
Notice at collection
Businesses must provide notice at or before the point of collecting personal information. This notice must include:
- Categories of personal information to be collected
- Purposes for which each category will be used
- Link to the privacy policy
- If the business sells or shares personal information, a link to "Do Not Sell or Share My Personal Information"
- For sensitive personal information, whether the business uses or discloses it for purposes beyond those permitted under CCPA
Record-keeping requirements
Businesses must maintain records of consumer requests and their responses for at least 24 months. These records must document:
- Date the request was received
- Nature of the request (type: know, delete, correct, opt-out, limit sensitive PI use)
- Manner in which the request was made
- Date of the business's response
- Nature of the response (complied in whole or in part, denied, etc.)
- Basis for denial if the request was denied
For businesses processing personal information of 10 million or more California residents annually, additional metrics reporting is required by July 1 each year covering the previous calendar year. These metrics include number of requests received, number complied with, number denied, and median and mean response times for each request type.
CCPA data security requirements
CCPA requires businesses to implement and maintain "reasonable security procedures and practices appropriate to the nature of the personal information" they handle. This requirement carries significant weight - consumers can sue businesses directly if their nonencrypted and nonredacted personal information is breached due to failure to maintain reasonable security.
Statutory damages for security failures range from $107 to $799 per consumer per incident (adjusted for inflation as of 2025). A data breach affecting 10,000 California residents could trigger $1 million to $8 million in statutory damages before accounting for attorney fees, litigation costs, or reputational harm.
What counts as reasonable security
The California Attorney General endorsed the CIS Controls (Center for Internet Security) as the baseline for reasonable security in data breach reports. These controls provide a prioritized set of actions for cybersecurity defense.
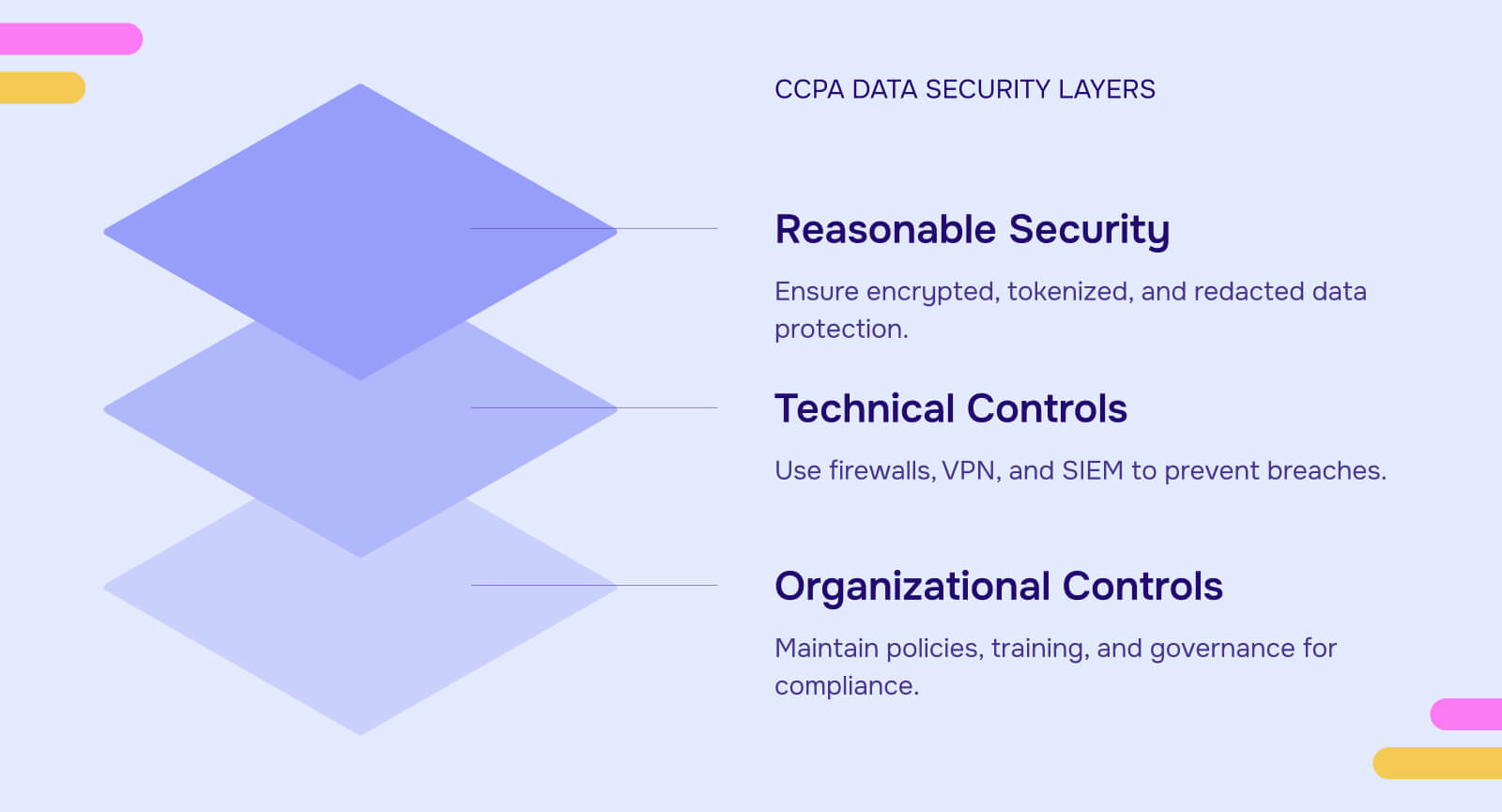
Basic CIS Controls that every organization should implement include:
Inventory and control of hardware and software assets to know what's on the network. You can't protect what you don't know exists. Organizations discovered this during the Log4j vulnerability crisis when companies struggled to identify which systems were exposed.
Continuous vulnerability management through regular scanning, assessment, and remediation. Automated scanning tools identify security gaps before attackers exploit them.
Controlled use of administrative privileges, restricting elevated access to only those who need it and monitoring privileged account activity. The Tractor Supply CCPA enforcement action specifically cited inadequate access controls as a compliance failure.
Maintenance, monitoring, and analysis of audit logs to detect security incidents and establish accountability. Many breaches go undetected for months because organizations aren't actively reviewing their logs.
Foundational CIS Controls add layers of defense:
Email and web browser protections against phishing attacks and malicious downloads. Over 90 percent of successful breaches start with phishing emails.
Malware defenses including anti-virus software, application whitelisting, and behavioral analysis.
Data recovery capabilities through regular backups stored securely and tested periodically. Ransomware attacks have rendered backups useless when organizations discovered their backup systems were compromised along with production systems.
Controlled access based on need-to-know principles, implementing role-based access control (RBAC) to limit data exposure.
Organizational CIS Controls establish enterprise-wide security practices:
Incident response and management plans documenting how the organization will detect, respond to, and recover from security incidents. CCPA requires breach notifications within specific timeframes—having a plan prevents chaotic scrambling when breaches occur.
Penetration tests and red team exercises to identify weaknesses before attackers do.
Data protection measures including encryption, tokenization, and redaction to render data useless if intercepted or stolen.
Security awareness and training programs ensuring employees understand their role in protecting information. The human element remains the weakest link—employees need regular training on identifying phishing attempts, handling sensitive data, and reporting suspicious activity.
Technical controls
Organizations implement reasonable security through multiple technical layers:
Identity and access management: Multi-factor authentication (MFA) for all accounts with access to personal information, role-based access control limiting permissions to job functions, privileged access management for administrative accounts, and regular access reviews removing unnecessary permissions.
Data protection: Encryption at rest using AES-256 or equivalent standards for stored data, encryption in transit using TLS 1.2 or higher for data transmission, data loss prevention (DLP) tools monitoring and blocking unauthorized data transfers, tokenization replacing sensitive data with non-sensitive substitutes, and redaction permanently removing sensitive information from documents.
Network security: Firewalls segmenting networks and controlling traffic flow, intrusion detection and prevention systems (IDS/IPS) identifying and blocking attacks, network segmentation isolating sensitive systems from general corporate networks, and virtual private networks (VPNs) securing remote access.
Monitoring and logging: Security information and event management (SIEM) systems aggregating logs for analysis, real-time alerting on suspicious activities, anomaly detection identifying unusual patterns, and log retention meeting compliance requirements (minimum 24 months for CCPA).
Organizational controls
Technical controls must be supported by organizational structures and policies:
Governance: Designate a privacy officer with authority and resources to implement the compliance program. Establish a privacy committee with representatives from legal, IT, security, HR, and marketing. Implement board oversight with regular privacy and security reporting to executives and directors.
Policies and procedures: Written Information Security Program (WISP) documenting security controls and responsibilities, data classification policy categorizing information by sensitivity, data retention policy specifying how long different categories are kept, incident response plan with clear procedures for breach detection and notification, and breach notification procedures meeting CCPA's timeline requirements.
Training and awareness: Annual mandatory privacy and security training for all employees, role-specific training for teams handling sensitive data (HR, customer service, legal), security awareness training covering phishing, social engineering, and secure data handling, and documentation of training completion for compliance evidence.
The intersection of CCPA security requirements and redaction creates a critical compliance strategy. While encryption protects data in transit and at rest, redaction permanently removes it - eliminating risk entirely for information that doesn't need to be retained.
CCPA enforcement and penalties
CCPA regulations enforcement has evolved from rare and tentative to aggressive and systematic. Two agencies now have concurrent jurisdiction to bring enforcement actions.
Dual enforcement authority
California Attorney General: Rob Bonta's office has maintained primary enforcement authority since CCPA took effect in July 2020. The Attorney General brings civil penalty actions through California courts, focusing on violations involving targeted advertising, sale of personal information, and failures to honor opt-out requests.
The mandatory 30-day cure period that originally gave businesses time to fix violations after notification was eliminated on January 1, 2023. The Attorney General now has discretion to provide cure periods but is not required to do so.
California Privacy Protection Agency (CPPA): Established by CPRA in 2020 and gaining full enforcement authority July 1, 2023, the CPPA can impose administrative fines directly without going through courts. Executive Director Tom Kemp and Head of Enforcement Michael Macko have targeted connected vehicles, data brokers, cookie management failures, employee data, and dark patterns in user interfaces.
The CPPA's approach differs from traditional enforcement. As Macko stated, "Most of these investigations, the businesses do not know about us. We haven't surfaced yet in most of them." The agency had nearly 3,000 complaints and hundreds of open investigations as of their 2024 annual report.
Current penalty amounts
As of January 1, 2025, CCPA fines increased due to Consumer Price Index adjustments:
- $2,663 per unintentional violation (up from $2,500)
- $7,988 per intentional violation (up from $7,500)
- $7,988 per violation involving minors
These penalties apply per violation, not per affected consumer. A business that fails to provide required privacy policy disclosures commits one violation. A business that fails to honor 500 opt-out requests commits 500 violations at $2,663 to $7,988 each—potentially $1.3 million to $4 million in penalties.
Private right of action
Consumers have limited ability to sue businesses directly under CCPA. Private lawsuits are only permitted for data breaches involving unauthorized access, exfiltration, theft, or disclosure of nonencrypted and nonredacted personal information due to the business's failure to maintain reasonable security.
This private right of action does not apply to general CCPA complience violations like disclosure failures, denied deletion requests, or other consumer rights violations. Only the Attorney General and CPPA can enforce those provisions.
For covered breaches, consumers can recover statutory damages of $107 to $799 per consumer per incident (adjusted from the original $100 to $750). Consumers must provide 30 days' written notice giving the business an opportunity to cure the violation before filing suit.
The "nonencrypted or nonredacted" language creates the clearest path to protection: properly encrypting data in transit and at rest, and permanently redacting sensitive information that doesn't need to be retained, shields businesses from private lawsuits even if breaches occur.
Major enforcement cases
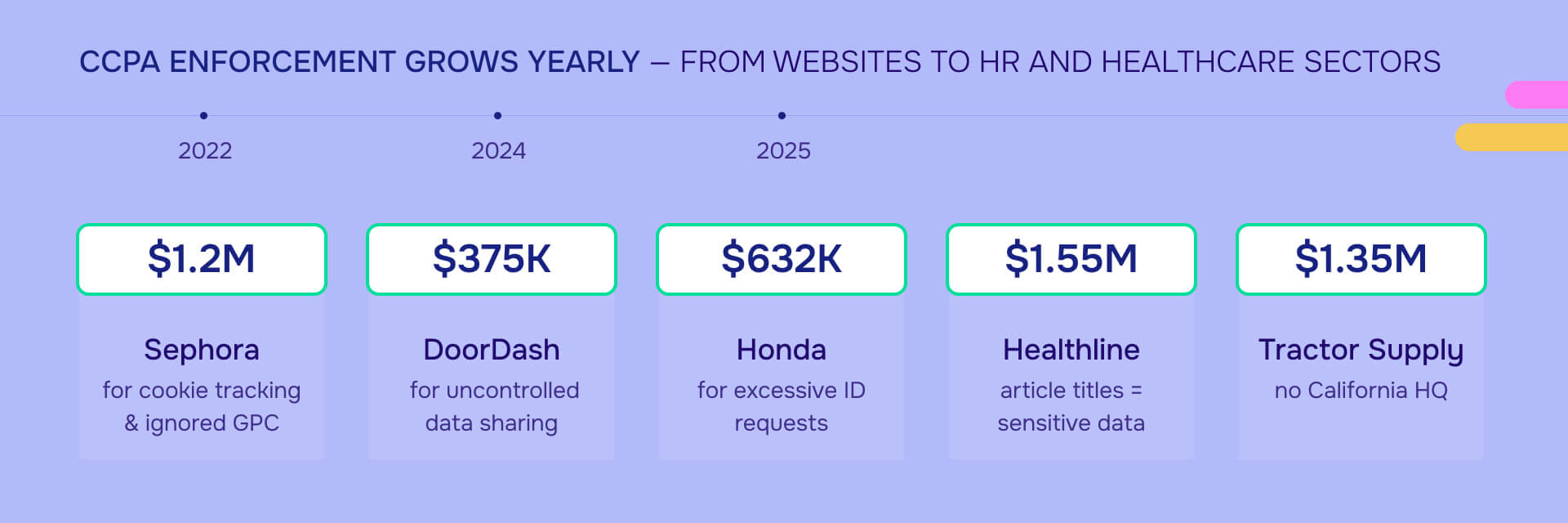
Healthline Media - $1.55 million (July 2025): Article titles cost Healthline the largest CCPA settlement to date. Reading "Crohn's disease symptoms" revealed a reader's health condition—turning search behavior into sensitive personal information. The settlement established that seemingly innocuous data like article titles can constitute protected health information. First enforcement action invoking CCPA's purpose limitation principle.
Tractor Supply Company - $1.35 million (September 2025): A Tennessee retailer with no California headquarters paid $1.35 million for ignoring opt-out requests from customers and job applicants. First CPPA decision addressing employment data. The settlement mandated quarterly compliance reviews for four years—proving enforcement extends beyond fines to ongoing surveillance. Most businesses still haven't updated practices since the employee data exemption expired December 31, 2022.
Sephora Inc. - $1.2 million (August 2022): The first public CCPA settlement targeted website tracking. Sephora used pixels and cookies to share browsing and purchasing behavior with advertisers without disclosure or opt-out mechanisms. The company also ignored Global Privacy Control signals. Attorney General Bonta: "These rights are meaningless if businesses hide how they are using customer data and ignore opt-out requests."
American Honda Motor Co. - $632,500 (March 2025): Honda demanded government ID photos to opt out of data sales—exceeding CCPA's verification standards. The company also implemented asymmetric cookie tools (easy opt-in, difficult opt-out) and lacked required CCPA provisions in ad tech contracts. Verification procedures must be proportionate to risk. Requiring ID photos for simple opt-outs fails that standard.
DoorDash Inc. - $375,000 (February 2024): DoorDash shared customer data with marketing cooperatives that resold it "many times over" to data brokers. The Attorney General ruled this violation incurable—once data propagates beyond your control through multiple third parties, compliance becomes impossible. The lesson: implement proper disclosures and contractual controls before sharing data. After it leaves your ecosystem, it's too late.
Common CCPA compliance mistakes
Missing or inadequate "Do Not Sell or Share" link
Businesses omit the required link entirely, use incorrect wording that doesn't match CCPA regulations's language, bury the link in places consumers can't find it, or implement links that don't actually function. Sephora's $1.2 million settlement partially stemmed from this failure.
The link must appear clearly and conspicuously on the business's homepage and in the privacy policy. The exact wording should be "Do Not Sell or Share My Personal Information," "Your Privacy Choices," or "Your California Privacy Choices." The link must remain functional and actually process opt-out requests when clicked.
Inadequate privacy policies
Privacy policies missing the 12 required CCPA elements, failing to update annually, lacking required disclosures about data sales or sharing, or providing vague descriptions that don't meaningfully inform consumers expose businesses to enforcement.
Tractor Supply's $1.35 million settlement cited inadequate privacy policies and notices as key violations. The CPPA found the policies didn't provide sufficient information for consumers to understand their rights or how to how to comply with Consumer Privacy Act obligations.
Failure to respond timely
Organizations that miss the 10-business-day acknowledgment requirement, exceed the 45-calendar-day response deadline, or fail to notify consumers when invoking the 45-day extension create liability. Each missed deadline constitutes a separate violation at $2,663 to $7,988 per occurrence.
Beyond regulatory penalties, slow responses impose operational costs. Industry reports indicate manually processing consumer requests often costs over $1,000 per request for complex organizations when accounting for staff time, system access, legal review, and cross-departmental coordination.
Automated consumer request management platforms reduce both compliance risk and operational cost, handling requests systematically within mandated timeframes while maintaining required documentation.
Inadequate vendor management
Businesses fail to review contracts with service providers, data processors, and third-party vendors for required CCPA provisions. The law mandates specific contractual language prohibiting service providers from selling or sharing personal information, identifying business purposes for processing, and requiring CCPA compliance.
Honda's $632,500 settlement partially resulted from missing CCPA contract provisions with advertising technology vendors. When the California Privacy Protection Agency investigated, they found Honda's agreements with ad tech partners lacked required protections and audit rights.
Organizations should conduct a comprehensive vendor inventory, assess which vendors access or process California residents' personal information, implement data processing agreements with all required CCPA clauses, and conduct regular vendor risk assessments to ensure ongoing compliance.
Poor data minimization
Businesses collect unnecessary personal information on intake forms, request excessive verification information when consumers exercise rights, or retain data longer than necessary for the stated purpose. Each practice violates CPRA's data minimization principle.
Honda and fashion retailer Todd Snyder both paid penalties partially for requiring excessive information. Honda required government-issued ID photos for all consumer requests, including opt-outs which don't require verification under CCPA. Todd Snyder similarly requested more information than necessary.
The California Privacy Protection Agency's Enforcement Advisory 2024-01 made clear that data minimization applies to every purpose for collecting, using, retaining, and sharing personal information. Businesses should audit all data collection points and retention schedules, implementing progressive disclosure that requests only information necessary at each stage.
Ignoring Global Privacy Control signals
DataGrail analysis of 5,000+ websites found approximately 75 percent of businesses aren't honoring GPC signals. These businesses fire three or more tracking cookies despite GPC activation, violating CCPA's requirement to recognize and honor opt-out preference signals.
Many businesses implement cookie consent management platforms without properly configuring them to recognize GPC. Others are simply unaware of the requirement. As CPPA Head of Enforcement Michael Macko stated after the Todd Snyder settlement: "Using a consent management platform doesn't get you off the hook for compliance. The buck stops with the businesses that use them."
Organizations must test their websites with GPC enabled to verify tracking actually stops, regularly audit cookie behavior across different browser configurations, and monitor third-party privacy tools to ensure they function correctly.
Inadequate security measures
Failing to implement CIS Controls, storing personal information without encryption, missing access controls and audit logs, or lacking incident response plans creates both regulatory and litigation risk.
The private right of action allows consumers to sue for breaches involving nonencrypted and nonredacted personal information due to inadequate security. With statutory damages of $107 to $799 per consumer, breaches can generate millions in liability before accounting for remediation costs, legal fees, and reputational damage.
Beyond consumer lawsuits, the California Attorney General can bring enforcement actions for security failures, adding regulatory penalties to the private litigation exposure.
The critical role of redaction in CCPA compliance
Redaction serves as both a shield against legal liability and a method for operationalizing CCPA's data minimization principle. CCPA's private right of action explicitly exempts "non-encrypted or non-redacted" personal information—properly redacted data protects businesses from consumer lawsuits in the event of a breach.
Three key functions of redaction for CCPA
Breach liability shield: CCPA allows consumers to sue if their "non-encrypted or non-redacted personal information" is breached due to inadequate security. With statutory damages of $107 to $799 per consumer per incident, a breach affecting 10,000 California residents could cost $1 million to $8 million before legal fees. Redacting sensitive information in non-production environments, shared documents, and archived records substantially reduces this exposure.
Data minimization support: CPRA established data minimization as a foundational principle—businesses must collect, use, and retain only what's "reasonably necessary and proportionate." Redaction enables retaining documents for legitimate purposes (audit trails, legal holds) while removing personal information that's no longer necessary.
Operational efficiency: Organizations share documents with vendors, auditors, and partners regularly. Redacting unnecessary personal information before sharing reduces risk without disrupting operations. A law firm can share case files with expert witnesses after redacting client Social Security numbers. A hospital can provide research data after redacting patient identifiers. An insurance company can share claims information after redacting policyholder financial details.
When redaction is required for CCPA
Responding to consumer requests: Before disclosing documents to requesting consumers, businesses must redact personal information belonging to other individuals. An employment file contains performance reviews mentioning other employees—those names and details must be redacted.
Audit and investigation responses: Permanently remove sensitive identifiers unless legally required for the specific purpose. A discrimination investigation needs demographic data but not employee names, Social Security numbers, or home addresses.
Sharing data for business purposes: CCPA mandates disclosing only the minimum necessary information. A retail analytics firm needs purchase patterns and demographics, not customer names or credit card numbers.
Non-production environments: Redact or mask real consumer data in testing, analytics, and development to reduce unauthorized access risk while maintaining realistic data for systems testing.
Public record releases: Redact victim names, witness addresses, Social Security numbers, and medical information from police reports before release, balancing transparency with privacy rights.
Common data requiring redaction
Personal identifiers: Social Security numbers, driver's license numbers, passport numbers—exposure enables identity theft and creates substantial liability.
Financial information: Bank account numbers, credit card numbers with security codes, transaction histories—redact when recipients lack business need.
Health information: Medical diagnoses, prescriptions, medical record numbers, even article titles revealing health conditions (per Healthline enforcement).
Biometric identifiers: Fingerprints, facial recognition data, iris scans, voiceprints—all constitute sensitive personal information under CPRA.
Authentication credentials: Usernames with passwords, security questions, MFA codes—many breaches occur from credentials exposed in logs or backups.
Industry-specific use cases
HR: Redact Social Security numbers and salary information on employee documents before sharing with managers. Redact other employees' performance data when responding to individual requests.
Customer service: Auto-redact credit card numbers in support tickets after payment processing. Redact financial information when escalating to third-party vendors.
Healthcare: Redact patient identifiers when creating research datasets. Redact insurance details when sharing treatment information with specialists.
Real estate: Redact Social Security numbers and bank accounts from transaction histories. Redact previous owners' contact information from comparable sales data.
Insurance: Redact health data when sharing claims with investigators. Redact beneficiary Social Security numbers from policy documentation.
Legal: Redact privileged communications before discovery production. Redact client financial information when sharing case files with expert witnesses.
Redaction methods and best practices
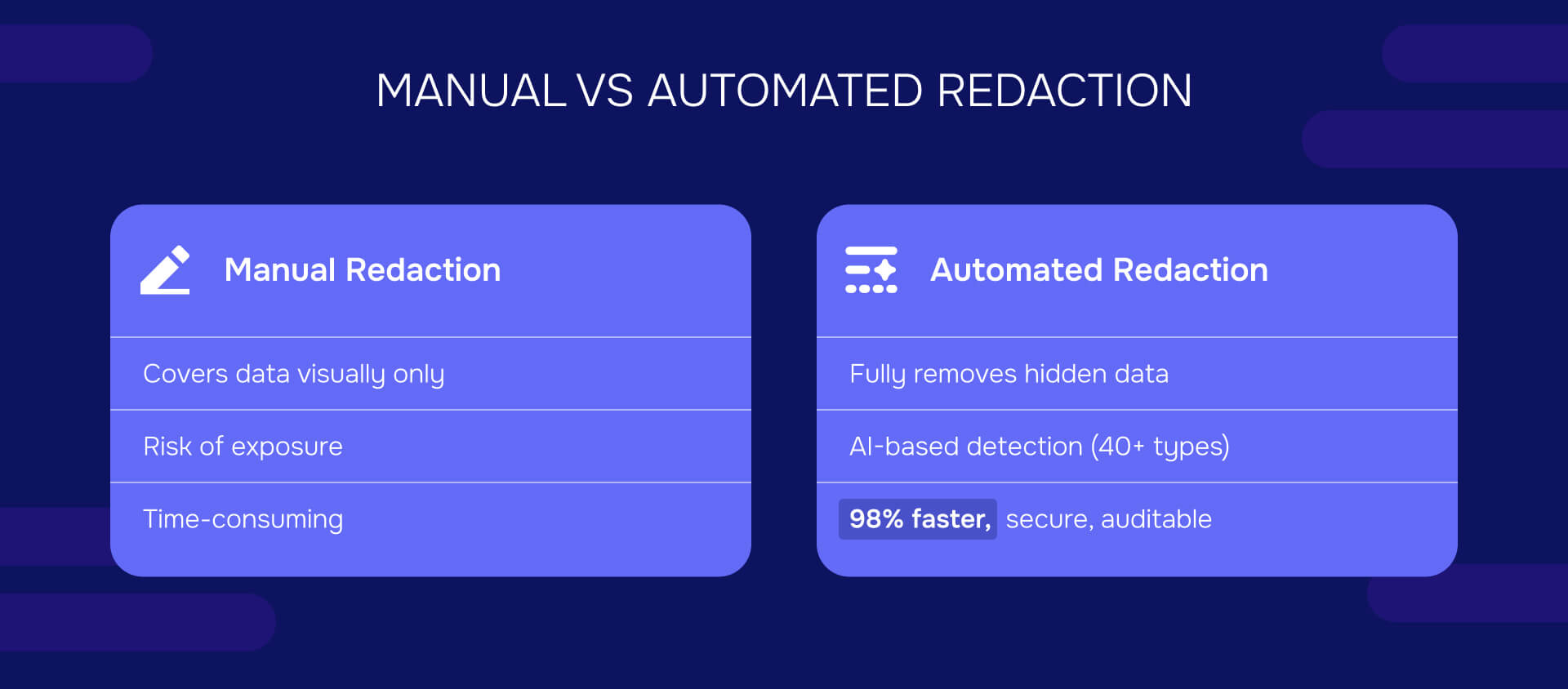
Manual redaction with PDF editors fails CCPA's standard. Drawing black boxes over text masks it visually but doesn't remove the underlying data. Anyone with basic technical knowledge can remove the boxes and reveal the information.
Effective redaction permanently removes sensitive data from the document file structure, including visible text, hidden layers, metadata, and embedded objects. Automated redaction tools use AI to identify sensitive information across 40+ categories and provide audit trails documenting what was redacted, when, by whom, and under what authority.
Automated redaction platforms like Redactable deliver 98 percent time savings compared to manual methods while ensuring permanent removal, metadata cleaning, and documented compliance.
Read also: Manual redaction vs. automated redaction: Which is better?
How to achieve CCPA compliance
CCPA compliance requires cross-functional coordination across legal, IT, security, HR, and marketing. Most organizations need four to five months for initial implementation.
- Establish team and assess gaps: Designate a privacy officer and assemble representatives from each department handling personal information. Review current privacy policies against CCPA's requirements and evaluate security measures against CIS Controls.
- Complete data mapping: Deploy data discovery tools to document what personal information you collect, where it resides, and which third parties access it. You cannot respond to consumer requests or implement data minimization without understanding your data landscape.
- Implement security controls: Deploy encryption, access controls, and multi-factor authentication. Establish automated redaction tools for documents and databases. Document your Written Information Security Program and create incident response plans.
- Build consumer rights infrastructure: Deploy a portal for California residents to submit requests. Integrate with existing systems to retrieve data. Configure systems to recognize Global Privacy Control signals automatically.
- Update legal documentation and vendors: Draft updated privacy policies with all required CCPA elements. Create notices at collection for each data collection point. Negotiate updated vendor agreements with required CCPA provisions and conduct vendor risk assessments.
- Train staff and launch: Deploy mandatory privacy training covering CCPA requirements and data handling procedures. Launch the updated privacy policy and consumer request portal. Implement quarterly compliance reviews, annual policy updates, and ongoing vendor monitoring.
CCPA compliance requires an ongoing program that adapts to regulatory changes, not a one-time project.
Technology considerations
Organizations processing personal information at scale benefit from compliance automation platforms. These tools provide data discovery and mapping, automated consumer request processing, consent and preference management, vendor risk management, policy and notice generation, and audit trail documentation.
Budget considerations vary significantly based on company size. Small businesses typically invest $1,000 to $10,000 annually in compliance tools. Mid-size businesses spend $10,000 to $50,000 annually. Enterprises often invest $50,000 to $250,000 or more annually in comprehensive platforms.
However, these costs must be weighed against the alternatives. Manually processing consumer requests at $1,524 per request quickly exceeds automation costs for any organization receiving significant request volume. Enforcement penalties of $2,663 to $7,988 per violation and private right of action exposure of $107 to $799 per affected consumer make the investment in proper tools and processes essential.
Why CCPA matters beyond California
CCPA compliance requirements keep expanding. New regulations take effect January 1, 2026 (enhanced cookie consent), January 1, 2027 (automated decision-making technology rules), and cybersecurity audit requirements phase in from 2028 to 2030 based on company revenue. These regulations add $4.2 billion in first-year compliance costs for California businesses.Enforcement has shifted from occasional to systematic. Two aggressive regulators pursue hundreds of investigations. Multi-million dollar settlements are routine. The era of regulatory patience has ended.
Organizations face a clear choice: reactive or proactive compliance.
- Reactive compliance accepts risk, implementing minimal controls while hoping to avoid enforcement. This invites fines up to $7,988 per violation, reputational damage from public settlements, customer loss, and competitive disadvantage as privacy-conscious consumers choose better-protected alternatives.
- Proactive compliance treats privacy as strategic investment. Organizations implementing comprehensive programs realize 1.6x return on investment through reduced legal costs, improved customer trust, and operational efficiencies. They save an average of $2.3 million annually in avoided fines and reduced breach costs. Beyond financial returns, 94 percent of customers won't buy from businesses that don't protect their data.
Effective CCPA compliance rests on three pillars: understanding what personal information you collect through comprehensive data mapping, implementing reasonable security measures including encryption, access controls, and redaction, and establishing efficient processes for responding to consumer requests within mandated timeframes.
Redaction plays a crucial role—permanently removing sensitive information eliminates risk entirely rather than simply securing it. Automated redaction platforms like Redactable deliver 98 percent time savings while providing protection against both regulatory penalties and private lawsuits.
With 500,000+ U.S. businesses under CCPA jurisdiction and enforcement now systematic, the question isn't whether to comply—it's whether you'll invest proactively or pay penalties reactively.







