Your birth date by itself is just a number - millions of people share January 15th. Your ZIP code alone tells nothing personal - thousands live in 10001. Your gender is basic demographic data. But combine all three, and suddenly you become uniquely identifiable among 87% of the American population. This is how modern identity theft works: harmless details become powerful identification tools when criminals connect the dots.
PII breaches drained $16.6 billion from Americans in 2024. Yet when 1.7 billion breach notifications landed in people's inboxes, most recipients had no idea what personal information was actually compromised - or how criminals could use seemingly harmless details against them.
This comprehensive personal information list reveals what businesses must protect and what individuals need to safeguard. Modern PII goes beyond obvious identifiers like Social Security numbers - today's digital world creates new categories that can identify people.
What are the examples of PII, and how do you spot it?
Examples of PII include traditional identifiers like Social Security numbers and addresses, but the definition has expanded. Modern personal information examples encompass everything from keystroke patterns that reveal health conditions to device fingerprints that track behavior across websites.
The traditional approach of protecting obvious identifiers misses the sophisticated tracking methods that make privacy protection more critical than ever. Understanding these categories, which are elements of PII, isn't academic - it's essential for both personal privacy and business compliance.
What are direct identifiers and high-risk personal information?

These examples of personal information uniquely identify individuals by themselves and require the highest protection priority. This list of PII represents the most sensitive data categories:
Government-issued numbers
Social Security Numbers (SSN) represent the classic example where name and Social Security number combinations create immediate identity theft risk. Additional government identifiers include:
- Passport numbers, visa numbers, alien registration numbers
- Driver's license numbers, state identification numbers
- Tax identification numbers, voter registration numbers
- Military service numbers, security clearance identifiers
Financial account identifiers
Banking and financial details that enable immediate fraud:
- Bank account numbers and routing numbers
- Credit card numbers (requiring specialized credit card number scanning software for secure processing)
- Investment account numbers, retirement account identifiers
- Insurance policy numbers and claim numbers
Biometric identifiers
Physical characteristics that permanently identify individuals form another category of examples of personally identifiable information:
- Fingerprints, iris scans, retina patterns
- Facial geometry measurements, voice signatures
- DNA profiles, genetic markers
- Palm prints, vein patterns, handwriting samples
These biometrics cannot be changed if compromised, making their protection critical.
What are the indirect identifiers?

These data points don’t identify someone alone but become powerful when combined. Research shows that even seemingly harmless demographic details can create unique identification patterns.
Think of it like a process of elimination. Start with 300+ million Americans. Your ZIP code narrows it to 40,000 people. Add your birth year - 800 remain. Add your gender - 400 left. Each detail eliminates more candidate records until you're uniquely identifiable from what seemed like meaningless information.
Demographic information
Name is an example of PII when combined with other data points, creating identification possibilities through:
- Age, birth date, gender identity
- Race, ethnicity, marital status
- Nationality, citizenship status
- Educational background, graduation years
Geographic data
Location-based personal information examples that narrow identification:
- ZIP codes, postal codes, area codes
- City, state, province, country
- Census tract, voting district boundaries
- GPS coordinates, geofencing data patterns
Read also: USPS FOIA redaction guide: Exemptions, processing, timelines
Professional information
Work-related examples of personal data that enable identification:
- Job titles, employer names, work locations
- Professional licenses, industry certifications
- Salary ranges, employment history records
- Union membership, professional organization affiliations
Traditional privacy advice fails because it only protects obvious identifiers and ignores the data combinations that identify you.
Sensitive PII categories that require special handling
These examples of PII include information types that require the highest security standards due to potential discrimination or harm:
Financial information
Economic data that creates vulnerability - key personal details example of protected information::
- Credit reports, credit scores, financial statements
- Tax returns, income documentation records
- Investment portfolios, trading histories
- Bankruptcy records, debt information, loan applications
Health information
Medical PII data examples protected under HIPAA and similar regulations:
- Medical records, treatment histories, diagnoses
- Prescription information, mental health records
- Genetic test results, family medical history
- Disability status, workers' compensation claims
HIPAA specifically defines 18 identifiers that make health information into protected PHI. For the complete list of these health-related identifiers and detailed protection requirements, see our comprehensive guide to HIPAA patient identifiers.
Legal information
Personal details examples that may be used, or produced by courts and law enforcement:
- Criminal history, arrest records, court documents
- Immigration status, visa applications
- Litigation involvement, legal settlements
- Background check results, security clearance data
Modern digital PII categories
Technology continuously produces new types of personally identifiable information (PII) that most organizations and regulatory standards fail to recognize or address. This gap exposes companies to compliance risks and data breaches because their policies and controls do not cover emerging examples of PII forms:
Device identifiers
Hardware-based personal information examples:
- IMEI numbers, MAC addresses, device serial numbers
- Advertising identifiers (Google GAID, Apple IDFA)
- Browser fingerprints, hardware configuration fingerprints
- SIM card identifiers, network signatures
Online identifiers
Digital identifiers that track across platforms - modern example of personal data:
- IP addresses when linked to individuals
- Email addresses, social media handles
- User account names, loyalty program identifiers
- Digital certificates, cryptographic keys
Behavioral biometrics
Pattern-based data that identify through behavior representing newer PII examples list entries:
- Keystroke dynamics (typing patterns that can reveal medical conditions like Parkinson's disease)
- Gait patterns, walking characteristics
- Mouse movement patterns, touch gesture signatures
- Voice stress patterns, speaking rhythm analysis
AI-inferred personal data: The invisible threat
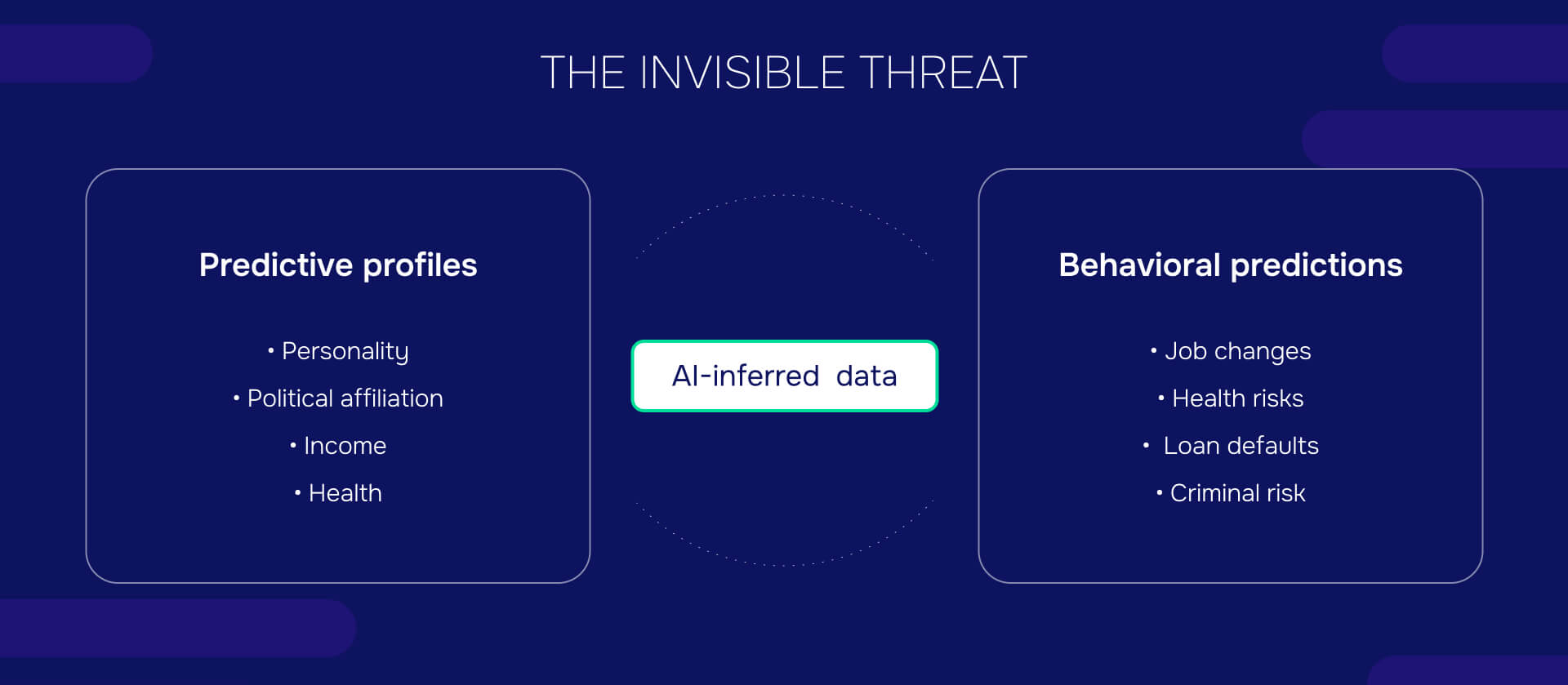
Modern algorithms create example of personal information that individuals never directly provided:
Predictive profiles
AI-generated personal profiles:
- Personality assessments based on social media activity
- Health risk predictions derived from browsing behavior
- Income estimates calculated from purchase patterns
- Political affiliation inferences from data correlation analysis
Behavioral predictions
Algorithmic forecasts that become personal data examples:
- Likelihood of job changes, relationship status changes
- Propensity for specific health conditions or treatments
- Risk assessments for loan defaults or insurance claims
- Probability calculations for criminal behavior or recidivism
These AI-inferred profiles extend PII beyond what people directly provide.
Regulatory definitions: What law considers PII
Understanding legal frameworks helps determine what is actually considered as PII. This list of personal information varies by regulation:
GDPR (European Union)
Personal Data includes "any information relating to an identified or identifiable natural person," encompassing online identifiers, location data, and behavioral patterns. The GDPR's broad interpretation means virtually any distinguishing information qualifies.
CCPA/CPRA (California)
Personal Information covers data that "identifies, relates to, describes, is reasonably capable of being associated with, or could reasonably be linked" to consumers or households. California uniquely includes household-level data and commercial information.
HIPAA (Healthcare)
Protected Health Information (PHI) encompasses health information tied to 18 specific identifiers including names, addresses, dates, phone numbers, Social Security numbers, medical record numbers, account numbers, and biometric identifiers.
FERPA (Education)
Educational Records include information directly related to students maintained by educational institutions, covering grades, disciplinary records, and any personally identifiable information in education files.
Industry-specific PII considerations
Different sectors face unique PII protection requirements for various examples of PII include:
Healthcare: HIPAA's 18 identifiers
Healthcare organizations must protect all PHI that could identify patients, including medical record numbers, health plan beneficiary numbers, biometric identifiers, and full-face photographs combined with health information.
Average healthcare breach cost reaches $9.77 million—the highest of all industries for 14 consecutive years.
Financial services: GLBA requirements
Financial institutions must protect nonpublic personal information including account numbers, Social Security numbers, credit reports, financial statements, transaction histories, and investment portfolios.
New 2024 requirement mandates FTC breach notification for incidents affecting 500+ individuals.
Education: FERPA protections
Schools must protect educational records including student grades, transcripts, disciplinary records, special education information, health records, and financial aid information.
Legal services: Attorney-client privilege
Law firms face unique challenges protecting attorney-client privileged communications, case-related information, client personal and financial data, and work product materials.
Recent trend shows courts increasingly reject privilege claims for post-breach forensic reports.
Real-world consequences: Case studies in PII exposure

Snowflake multi-client cascade (2024)
Impact: 165+ organizations, 500+ million individuals affected
Root cause: Stolen credentials lacking multi-factor authentication
Key lesson: Third-party cloud security failures cascade across industries
Affected companies included AT&T (nearly all wireless customers), Ticketmaster (560 million records), and Santander Bank (customer contact and transaction data).
PowerSchool education breach (2024)
Impact: 62.4 million students, 9.5 million educators
PII exposed: Social Security numbers, medical records, special education information
Industry impact: North Carolina discontinued PowerSchool services
Key lesson: Educational technology vendors handle extremely sensitive student data requiring enhanced protection
Read also: How Epstein files redactions were uncovered: Timeline 2025-26
How to protect PII: Actionable steps
For individuals
Enable multi-factor authentication everywhere - 1.24 billion records could have been saved with this single step. Monitor the "Big 4" identifiers: Social Security number, full name, birth date, and address combinations.
Understand modern tracking methods: keystroke patterns, device fingerprints, and location data now identify you as uniquely as traditional identifiers. Exercise privacy rights under CCPA, GDPR, and other regulations to see what companies know about you.
Sanitize all documents containing personal data before uploading them to AI chatbots, or sharing online. Use professional redaction software to achieve complete and permanent data removal.
For businesses
Implement comprehensive PII classification using the direct/indirect/sensitive framework outlined above. This PII examples list approach ensures all data categories receive appropriate protection. Address third-party risk immediately -30% of breaches now originate from vendors and partners.
Invest in detection capabilities: average US breach costs ($10.22 million) justify significant security investment. Train employees on modern PII categories including behavioral biometrics and AI-inferred data - understanding which are elements of PII prevents inadvertent exposure..
Cross-industry recommendations:
- Zero Trust Architecture: Assume breach and verify all access continuously
- Privacy by Design: Build PII protection into systems from development
- Regular risk assessments: Quarterly evaluations of PII handling practices
- Incident response planning: Prepare for when, not if, breaches occur
Read also: 10 ways to protect your personal data in 2025
How document security protects PII in files?
Many organizations overlook PII protection in documents shared internally or externally. Traditional methods like black markers or PDF boxes don't permanently remove sensitive information - they simply hide it visually while leaving data recoverable.
For organizations handling sensitive documents, professional tools like Redactable ensure permanent PII removal from files, including metadata and hidden layers, while maintaining document integrity for legal and business purposes.
Your next steps for PII protection

The definition of personal information that can identify you has fundamentally changed. Today's examples of personally identifiable information include behavioral patterns revealing health conditions, device fingerprints tracking across the internet, AI-generated profiles predicting personal characteristics, location patterns revealing life routines, keystroke dynamics diagnosing medical conditions, and digital exhaust from every online interaction.
Understanding the modern scope of PII isn't academic - it's essential for protection in a world where traditional privacy assumptions no longer apply. Names and Social Security numbers represent only the tip of the iceberg in today's AI-driven data landscape.
With 1.7 billion breach notifications delivered in 2024 alone and average breach costs exceeding $10 million, comprehensive PII protection has become a critical business and personal priority. Success requires understanding not just traditional identifiers, but the full spectrum of modern personal data that make us identifiable in an interconnected digital world. That means pairing awareness with action - whether by implementing advanced privacy practices, training teams, or taking simple steps like sanitizing electronic documents with professional redaction software before sharing them online.
Ultimately, protecting PII isn’t optional. It’s essential for organizations and a personal responsibility for individuals, in a world where our data is more powerful—and more vulnerable - than ever.







