The August 2025 federal court breach demonstrates how outdated systems amplify security vulnerabilities in criminal justice cyber security. The PACER hack exposed confidential informant identities and sealed documents because aging infrastructure cannot implement proper data minimization principles or modern security controls.
This cyberattack on federal court systems represents one of the most serious breaches of judicial infrastructure in U.S. history, potentially exposing confidential informant identities and sealed court documents across multiple states. This sophisticated breach of both the Case Management/Electronic Case Files (CM/ECF) and Public Access to Court Electronic Records (PACER) systems threatens the fundamental integrity of federal law enforcement operations and judicial confidentiality.
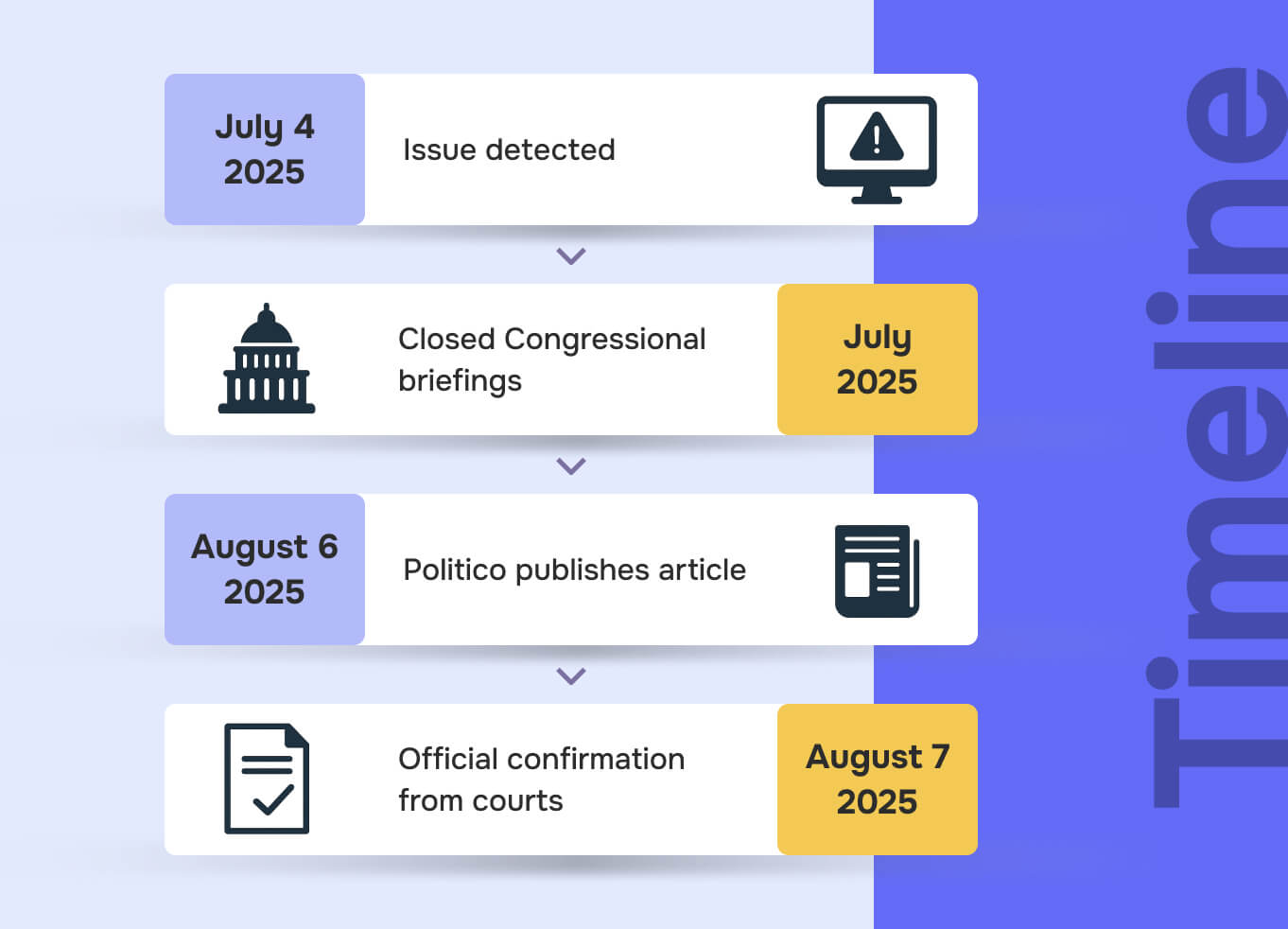
PACER hack timeline exposes gaps in data minimization and response
The PACER hack timeline suggests prolonged unauthorized access before discovery, demonstrating how outdated systems compound every security vulnerability. The Administrative Office of the U.S. Courts determined the severity of the security issue around July 4, 2025, but the full scope was still under assessment when Politico broke the story on August 6, 2025. Congressional lawmakers were quietly briefed in July, indicating the severity was immediately recognized at the highest levels of government.
The court hack potentially compromised sealed indictments, arrest warrants, search warrants, confidential informant identities, witness statements, cooperation agreements, and national security-related court filings across multiple federal district courts—exposing how legacy systems create cascading security failures.
The Administrative Office finally acknowledged the breach publicly on August 7, 2025, confirming "recent escalated cyberattacks of a sophisticated and persistent nature" while emphasizing collaboration with the Department of Justice, Department of Homeland Security, and congressional committees. Notably, the FBI, Justice Department, and Cybersecurity and Infrastructure Security Agency initially declined to comment or referred inquiries elsewhere, suggesting the sensitivity of ongoing investigations.
Poor data minimization principles enabled massive exposure
Critical design flaws enabled this breach that proper data minimization principles could have prevented or significantly mitigated. Current systems store unnecessary amounts of sensitive data in interconnected systems accessible through public-facing portals, creating extensive attack surfaces that violate fundamental data minimization principles.
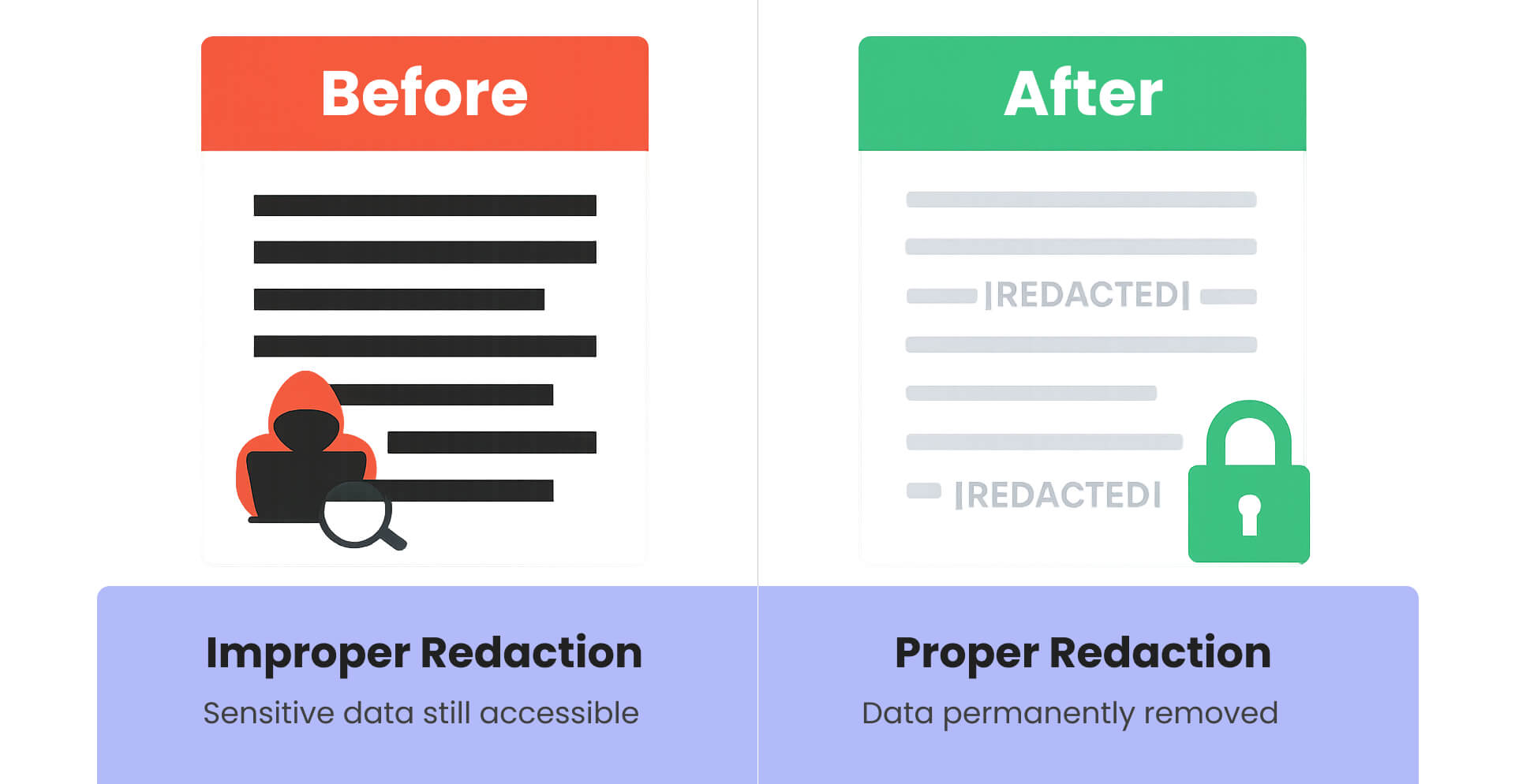
Effective data minimization principles require limiting collection to necessary information only, implementing purpose limitations for data use, establishing retention schedules for different document types, and regular data purging protocols. Proper redaction serves as a critical component of data minimization, permanently removing sensitive information rather than simply masking it. Instead, current court systems retain comprehensive historical records without clear retention limits or access controls proportionate to sensitivity levels.
With court systems processing thousands of documents daily containing sensitive personal information, automated redaction solutions become essential for effective data minimization at scale. Manual redaction methods - whether physical markers or basic PDF tools - cannot handle the volume while ensuring complete removal of sensitive data and metadata. The PACER hack demonstrates how inadequate redaction practices compound security vulnerabilities, as partially redacted or improperly protected documents create additional attack vectors for sophisticated adversaries.
Outdated systems spark major criminal justice cyber security failures
Technical analysis reveals this breach represents the culmination of persistent targeting by sophisticated threat actors, likely nation-state adversaries employing advanced persistent threat (APT) tactics against vulnerable criminal justice cyber security infrastructure. The attack follows documented patterns from previous breaches, particularly the 2020 SolarWinds supply chain compromise that affected the same federal court systems.
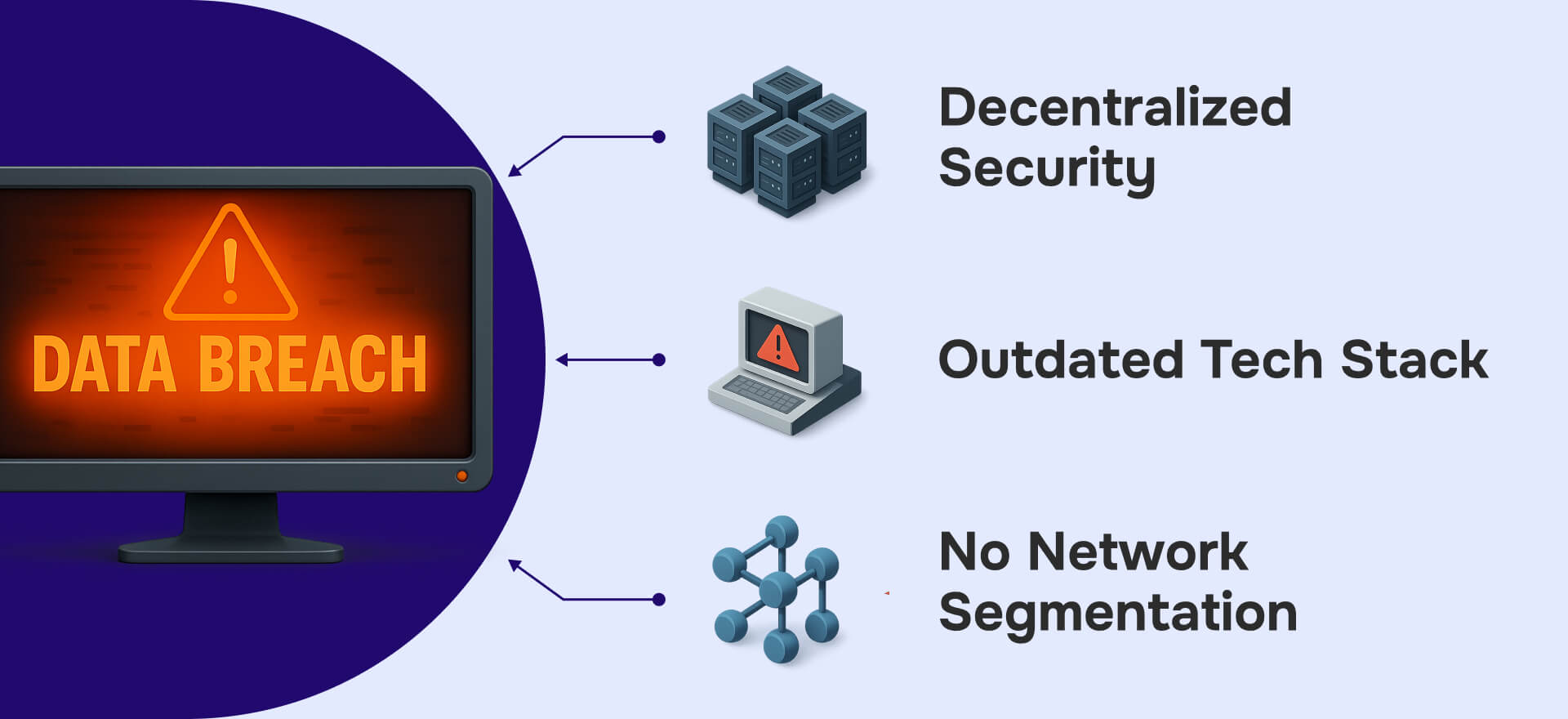
Outdated systems amplified the impact of poor data minimization. The current federal court hack exploited fundamental architectural weaknesses including the decentralized security model with 204 separate court websites managed by personnel with varying security expertise, outdated technology stack predating modern web security frameworks, and insufficient network segmentation between public PACER access and internal CM/ECF systems. Judge Michael Scudder's June 2025 congressional testimony revealed that federal courts blocked approximately 200 million harmful cyber "events" in fiscal year 2024 alone, demonstrating persistent targeting of aging infrastructure.
Legal frameworks fail to protect against modern court hack threats
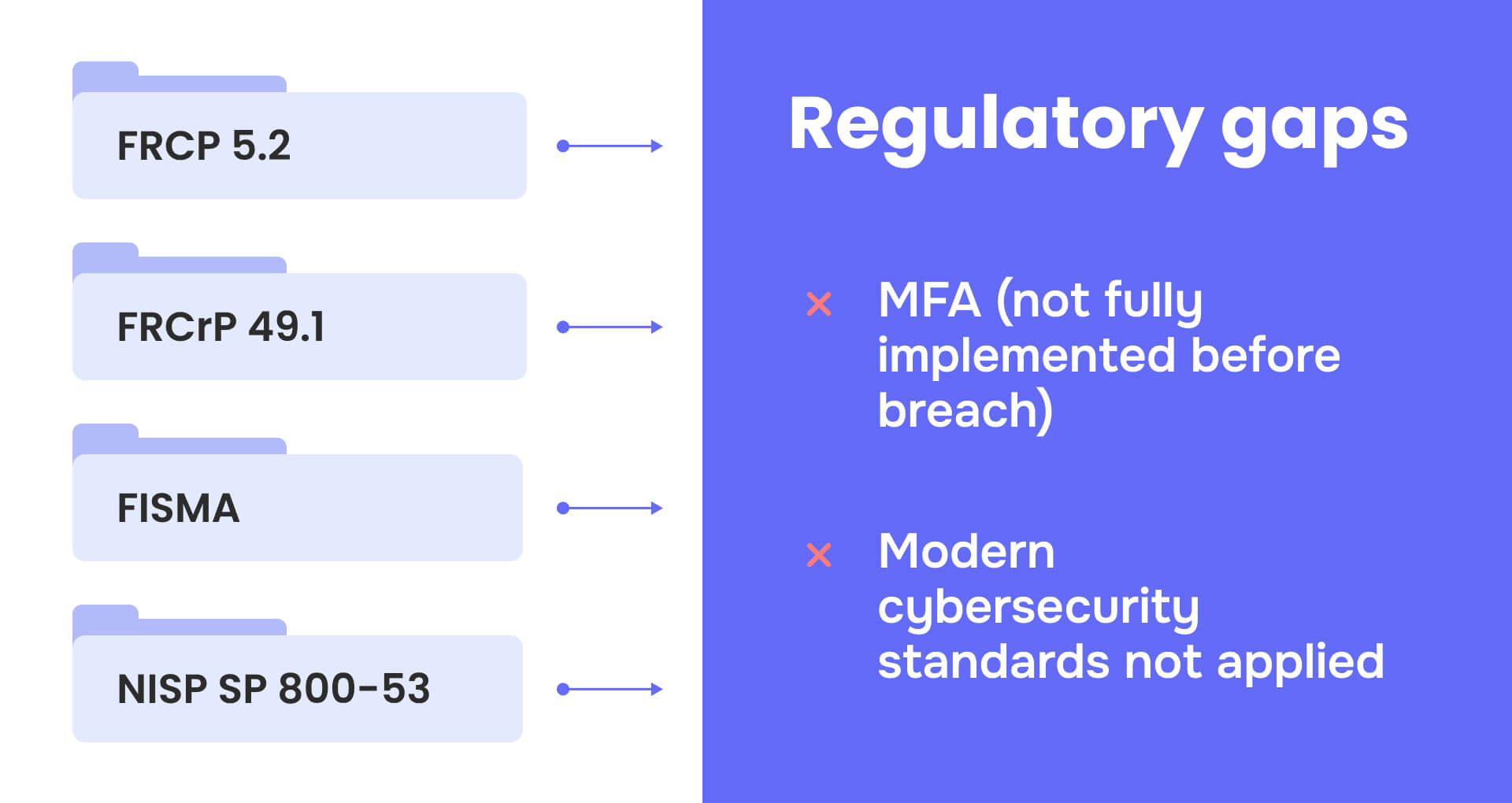
The regulatory landscape governing PACER security involves multiple overlapping frameworks that have struggled to keep pace with evolving cyber threats. Federal Rule of Civil Procedure 5.2 requires redaction of specific personal identifiers but places responsibility on filing parties rather than establishing system-level protections. Federal Rule of Criminal Procedure 49.1 provides similar requirements for criminal cases, while Federal Rule of Bankruptcy Procedure 9037 applies comparable standards to bankruptcy proceedings.
The Federal Information Security Modernization Act (FISMA) mandates comprehensive information security programs for federal agencies including the judicial branch, requiring annual security reviews and risk assessments. NIST SP 800-53 Rev. 5 provides over 1,000 security and privacy controls, but implementation across the decentralized court system has been inconsistent.
Critical regulatory gaps have emerged, particularly around multi-factor authentication implementation and modern cybersecurity standards. While MFA was mandated by August 25, 2025, the breach occurred before full implementation. The 2024 Loper Bright decision eliminating Chevron deference has created additional uncertainty around agency cybersecurity regulations, requiring more explicit Congressional authorization for cybersecurity measures.
Historical pattern shows escalating court hack targeting judicial systems
The PACER breach represents the latest in an escalating series of attacks on court systems and legal document repositories. The 2020 federal court breach, revealed by Rep. Jerry Nadler in July 2022, involved "three hostile foreign actors" and was described as having "startling breadth and scope." This previous incident lasted from early 2020 into 2021, providing prolonged unauthorized access to sealed court documents and national security matters.
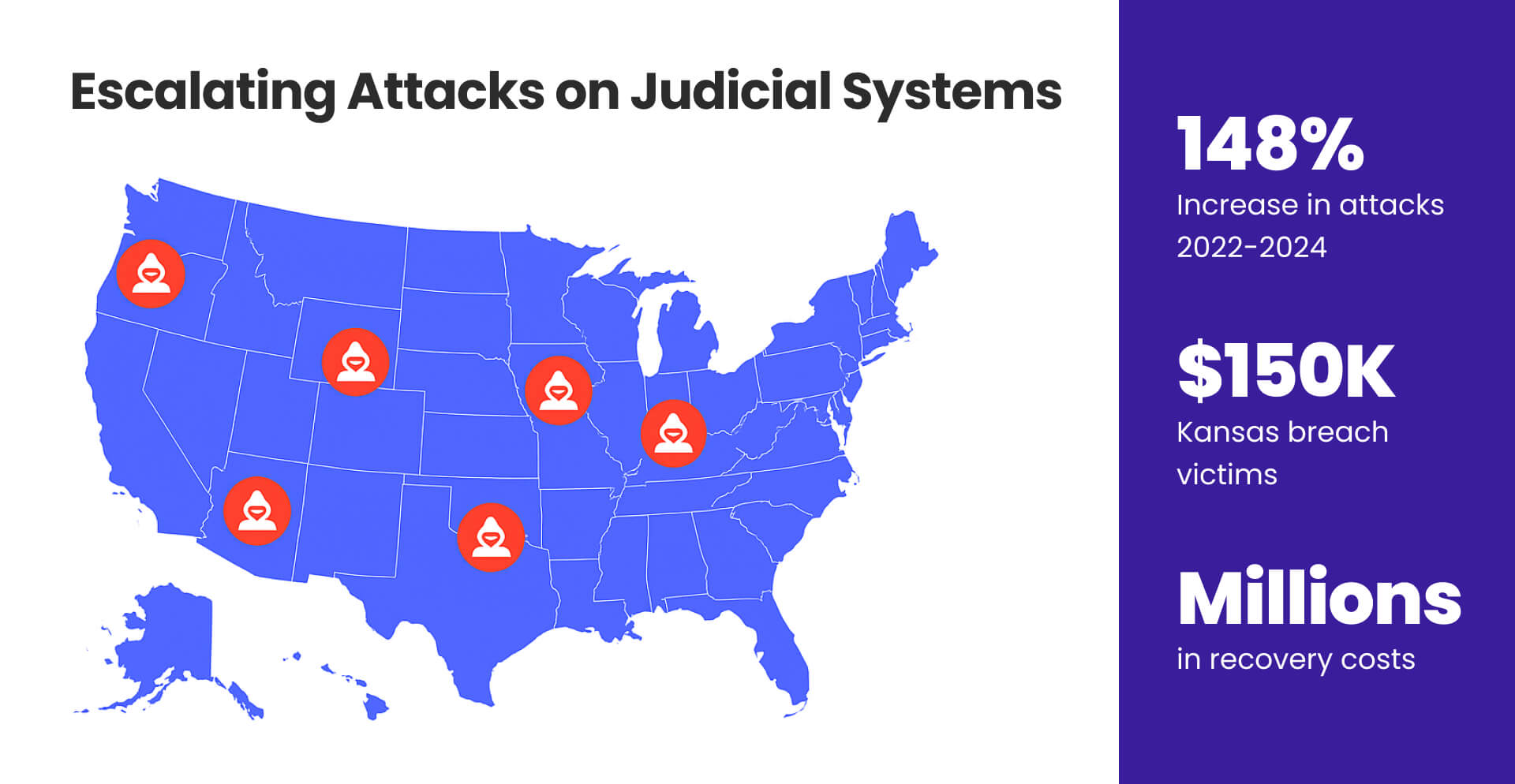
State court systems have faced similar sophisticated attacks. The October 2023 Kansas Supreme Court breach by Russian ransomware operators affected 150,000 individuals and kept courts offline for four months, costing millions in recovery efforts. Other states including Pennsylvania, Florida, Georgia, Missouri, Mississippi, Colorado, and Ohio experienced similar attacks between 2022-2024, with a 148% increase in malware attacks against state and local governments.
Major law firm breaches demonstrate broader vulnerabilities in legal document repositories. The 2016 Panama Papers exposed 11.5 million documents from Mossack Fonseca, while 2020's attack on Grubman Shire Meiselas & Sacks by REvil ransomware targeted entertainment law firm client data. Recent statistics show 29% of law firms reported security breaches in 2023, with average breach costs reaching $5.08 million for professional services.
The pattern reveals systematic targeting by nation-state actors, particularly Russia and China, focused on espionage, disruption, and political influence operations. Common attack methodologies include spear-phishing campaigns, supply chain attacks through third-party vendors, exploitation of unpatched vulnerabilities, and social engineering targeting high-value individuals.
Federal court cyber security proves insufficient against modern breaches
Expert assessments reveal that PACER and CM/ECF systems are fundamentally inadequate for current threat levels. Judge Michael Scudder's June 2025 congressional testimony characterized both systems as "outdated, unsustainable due to cyber risks, and requiring replacement." External security experts echoed this assessment, concluding that both systems require complete overhaul rather than incremental improvements.
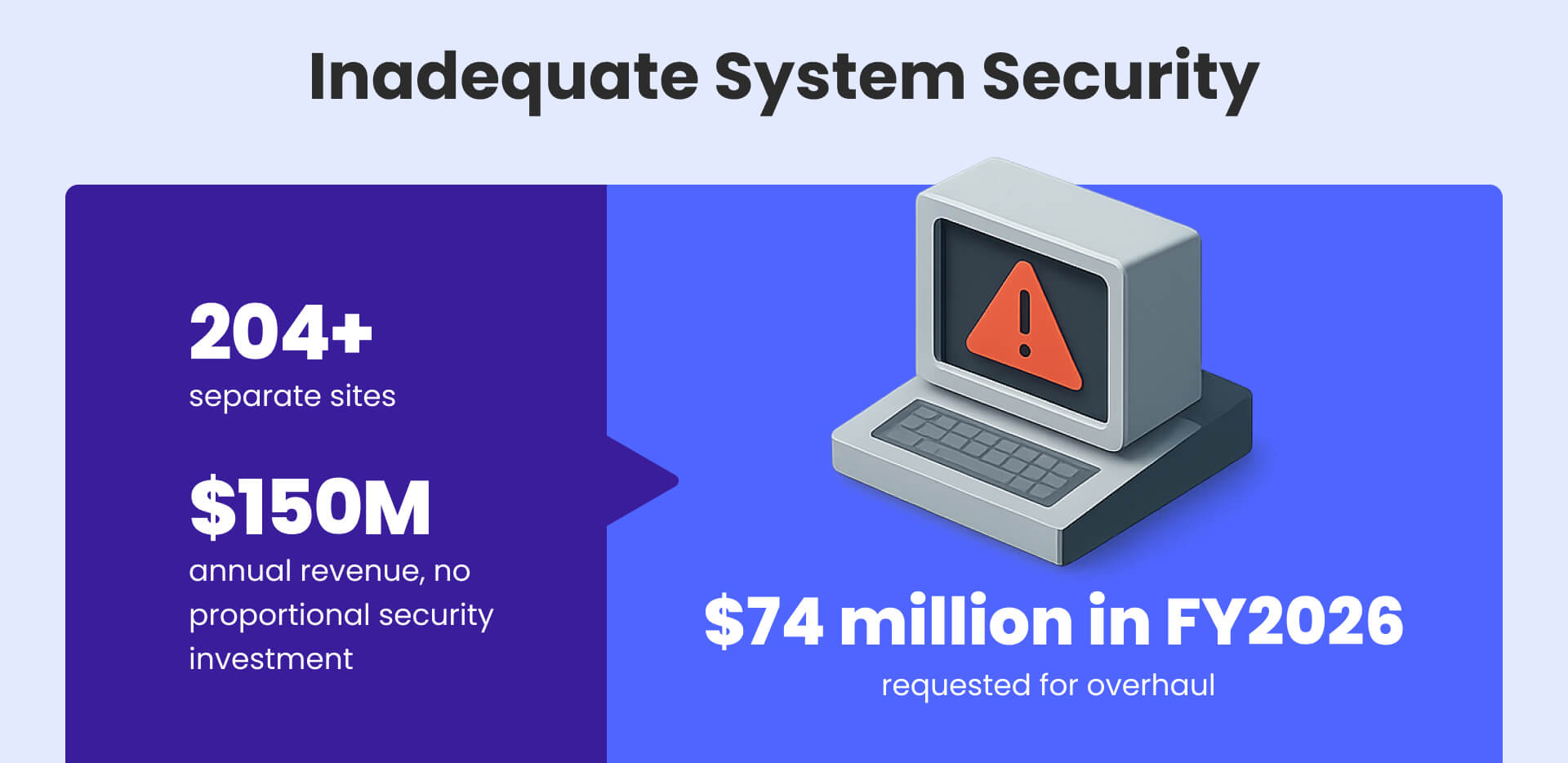
Critical vulnerabilities persist due to legacy architecture predating modern security frameworks, the distributed system of 204+ websites creating inconsistent security implementations, and lack of centralized security management. The Free Law Project's analysis noted that security fixes take six months to implement across the distributed system, as demonstrated by the 2017 CSRF vulnerability response.
Expert recommendations emphasize the need for complete system replacement rather than incremental fixes. Cybersecurity professionals advocate for centralization and standardization, adoption of modern web frameworks with built-in security, regular third-party security audits, establishment of bug bounty programs, and implementation of zero-trust architecture. The current system generates $150 million annually but lacks proportionate security investment.
Budget requests reflect recognition of security inadequacy. The Justice Department has requested $74 million in FY2026 specifically for federal judiciary electronic case filing system overhaul, emphasizing "agile" software development methodology with integrated cybersecurity from ground up.
PACER hack threatens fundamental integrity of American justice system
Sealed document exposure compromises fundamental judicial protections including sealed indictments, unserved search warrants, arrest warrants, witness statements, cooperation agreements, national security-related court filings, and evidence with "proprietary economic value." As cybersecurity experts warned, this exposure "risks derailing criminal investigations and could lead to witness intimidation or worse."
Attorney-client privilege faces new challenges as the hack raises concerns about legal strategies contained in court filings, settlement negotiations documented in sealed records, and work product doctrine protections being compromised. The American Bar Association's Model Rule 1.1 requires lawyers to maintain competence including understanding technology risks, but the breach highlights challenges attorneys face when relying on compromised federal court systems.
Federal law enforcement operations suffer operational security compromises through exposure of investigation methodologies, surveillance techniques, cooperating witness networks, and prosecutorial strategies. The breach affects the federal Witness Security Program (WITSEC), which has protected over 19,000 witnesses and family members since 1971, undermining the program's fundamental security principles.
The breach has accelerated comprehensive reform efforts previously moving slowly through government bureaucracy. The Justice Department's $74 million FY2026 budget request for complete system overhaul represents recognition that incremental security improvements cannot address fundamental architectural vulnerabilities.
Long-term modernization plans envision complete replacement of legacy PACER system with cloud-based case management featuring modern security architecture, unified search functionality across all federal courts, agile software development approaches, and advanced AI-driven threat detection and response capabilities. The new system will incorporate user-centered design, integrated cybersecurity from ground up, and modern technology architecture replacing decades-old legacy systems.
Congressional action has accelerated around increased cybersecurity funding for federal courts, potential Open Courts Act modifications for security requirements, Technology Modernization Fund applications for judicial systems, and enhanced coordination with executive branch cybersecurity agencies. Multiple congressional committees have conducted classified briefings and requested follow-up sessions for September 2025.
Conclusion: A critical inflection point for criminal justice cyber security
This PACER hack represents a fundamental watershed moment for criminal justice cyber security, exposing decades of deferred modernization that threatens the core integrity of American justice operations. The breach demonstrates that incremental security measures cannot address systemic vulnerabilities in legacy infrastructure, while nation-state adversaries increasingly view judicial systems as high-value targets requiring security commensurate with national security systems. The path forward demands immediate congressional funding for complete system replacement and recognition that modern criminal justice cyber security requires infrastructure capable of implementing proper data minimization principles through automated solutions rather than failed manual methods that outdated systems force organizations to use.
Solutions like Redactable's AI-powered automated redaction platform represent the kind of modern, security-first technology the federal court system needs - offering 98% time savings while ensuring permanent removal of sensitive information and metadata that manual methods consistently fail to protect. Proper data minimization through automated redaction isn't just about efficiency; it's about preventing the next catastrophic breach that could compromise ongoing investigations and endanger lives.
Protect your organization from data breaches with automated redaction - start your free trial today. If you want to learn more about implementing data minimization strategies while working with client data - schedule a free consultation with our team.







