Treating ePHI security as a mere "check-box" exercise isn't just negligence; it's a guaranteed pathway to devastating data breaches and multi-million dollar penalties.
“Enacted in 1996, the Health Insurance Portability and Accountability Act (HIPAA), also known as Public Law 104-191, established fundamental standards for safeguarding the privacy and security of individually identifiable health information managed by entities covered under HIPAA regulations.”
More to the point, according to the U.S Department of Health and Human Services, all organizations that collect and store ePHI are required to comply with specific mandates:
- Each organization is responsible and accountable for deploying and maintaining proper cybersecurity protection controls.
- Any material breach of ePHI must be reported, depending on the location, state, or country, within 60 days.
This accountability requirement apply equally to PHI and ePHI data.
What does ePHI stand for
ePHI stands for Electronic Protected Health Information, which refers to any individually identifiable health information that is created, stored, transmitted, or maintained in electronic form and is protected under the Health Insurance Portability and Accountability Act (HIPAA).
The Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996, and as a result, the initial Law provided thorough documentation of specifics around the protection of PHI information.
With the HIPAA Security Rule #2, published on February 20, 2003, formally introduced and mandated specific protections and requirements for electronic Protected Health Information (ePHI). Most organizations were required to comply with this rule by April 21, 2005.
“The Security Rule explicitly states that the security operations engineering team should safeguard electronic Protected Health Information (ePHI) by implementing administrative, physical, and technical safeguards.”
Both PHI and ePHI share common data fields, including:
- Name
- Address
- Birthday
- Phone
- Social Security Number
- Medical Record Number
ePHI medical records contain additional electronic data, including lab results, X-rays, treatment plans, medications, and exchanges with third-party firms.
With the introduction of Electronic Medical Records (EMR), CIOs, CISOs, and IT leaders needed to incorporate several new cybersecurity and physical controls. These controls broke down into three interconnected domains: administrative, physical, and technical.
Safeguarding ePHI beyond checking the box
“Organizations subject to HIPAA are required to implement administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and security of protected health information.”
These safeguards require frequent internal and external auditing to validate the various layers of project function as expected, or require an upgrade.
When ePHI security falters: The cascade of costs, consequences, and reputational damage
Failure to protect ePHI information is a costly and very damaging event for any organization, regardless of size, revenue, or location.
Noteworthy cases of ePHI data breaches include:
1. Anthem Inc.'s $16M settlement

Summary: The $16 million Anthem Inc. HIPAA breach settlement in 2018, stemming from a 2015 data breach affecting 78.8 million members, pushed OCR's total HIPAA penalties past $100 million.
The breach involved extensive theft of ePHI, with the OCR citing multiple HIPAA Rule violations, including inadequate risk analysis and security measures. This landmark settlement highlights the severe consequences of non-compliance.
2. New York-Presbyterian Hospital/Columbia University Medical Center's $4.8M fine

Summary: New York-Presbyterian Hospital and Columbia University Medical Center faced a $4.8 million fine for a 2010 ePHI data breach that affected 6,800 patients.
A physician's failure to secure a personal server led to the exposure of sensitive records online. This case exemplifies how inadequate security controls and risk assessments can lead to significant penalties, underscoring the importance of robust HIPAA compliance.
3. University of Texas MD Anderson Cancer Center's: $4.3M penalty
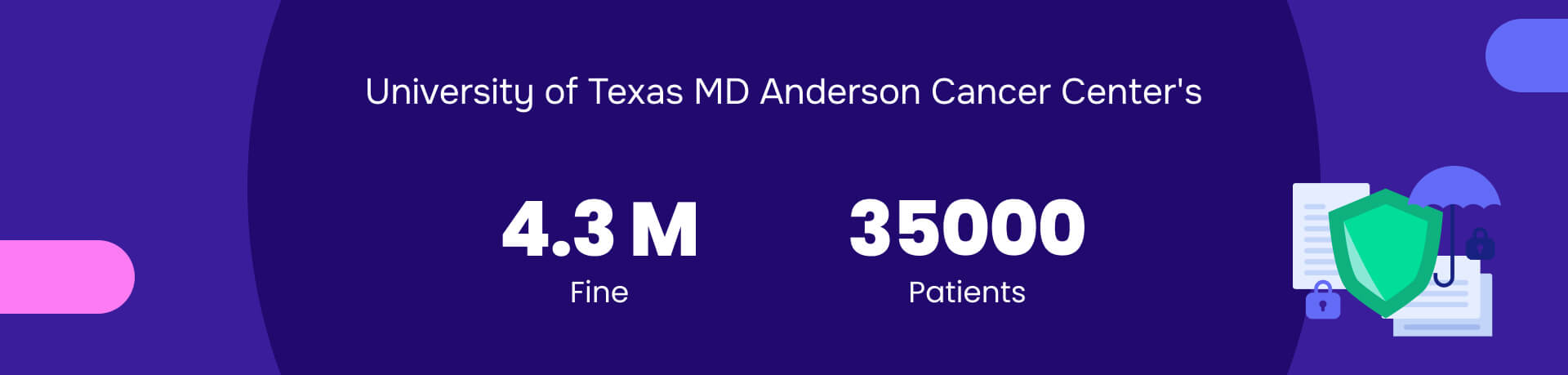
Summary: “The authorities fined the University of Texas MD Anderson Cancer Center $4.3 million for HIPAA violations.”
Authorities imposed the fine because of a 2012 laptop theft and a 2013 incident in which unencrypted USB drives containing the electronic health information (ePHI) of 33,500 patients went missing.
Despite having policies to protect data, the center failed to implement them adequately. This case underscores the crucial importance of protection ePHI to prevent significant penalties and data breaches.
Mastering ePHI compliance: From regulation to resilient security
Organizations under HIPAA compliance show strong governance when they have adopted proven industry security frameworks, including ISO 27001 and NIST 800 53.
HIPAA specifically doesn't require these frameworks to be implemented. However, HIPAA mandates several security controls to protect electronic protected health information (ePHI) data. These two frameworks specify these controls.
Before implementing any framework decision, organizations need to research the top security control solutions and validate whether they have the talent to deploy and manage these solutions.
Top 5 security controls protecting ePHI
Next-generation cyberattacks, powered by AI, are both a problem and a solution waiting to happen. Defense-in-depth strategies play a crucial role in protecting electronic protected health information (ePHI) data. Every layer within the security framework requires a robust solution set with experience and relevance in safeguarding electronic protected health information (ePHI) data.
Here is a breakdown of the top 5 security solutions that are critical in protecting ePHI data.
- Automated Redaction Software (e.g., Redactable): Redaction is crucial when sharing documents containing ePHI with unauthorized parties or for public release, ensuring only the "minimum necessary" information is disclosed. Redactable uses AI and OCR to identify and permanently remove sensitive data, including hidden metadata, from documents such as medical records. This technical control prevents accidental exposure and maintains HIPAA compliance during information sharing.
- Encryption (Thales - CipherTrust Data Security Platform): Thales is a top-tier vendor for enterprise-wide encryption, key management, and data protection across various environments (databases, files, cloud).
- Identity and Access Management (IAM) with Multi-Factor Authentication (MFA) (Cisco DUO): Cisco DUO is recognized for its ease of deployment, user-friendly push notifications, and robust security.
- Data Loss Prevention (Microsoft Purview DLP): Microsoft integrates seamlessly within the Microsoft 365 ecosystem, providing extensive data protection for Microsoft-centric environments. This DLP solution monitors, detects, and blocks sensitive data from leaving the organization's control. For ePHI, DLP can prevent accidental or malicious exfiltration of patient data via email, cloud uploads, or removable media.
- Security Information and Event Management (SIEM) with Cisco Splunk: Cisco Splunk centralizes security logs and events from across the entire IT infrastructure. This solution provides real-time monitoring, correlation of security events, and alerting for suspicious activities or potential breaches related to ePHI access and usage.
Beyond their strengths, the true power of these controls lies in their combined ability to diminish the threat of ePHI data loss significantly and lower risk.
Examples of ePHI
Electronic Protected Health Information encompasses any health data that can identify an individual when stored, transmitted, or processed electronically. Understanding specific examples helps organizations recognize what requires protection under HIPAA.
Direct patient identifiers in electronic form
Personal identifiers: HIPAA defines 18 specific identifiers that make health information into PHI when in electronic form. These include full names, Social Security numbers, medical record numbers, health plan beneficiary numbers, account numbers, certificate/license numbers, and any unique identifying numbers assigned by healthcare providers.
Contact information: Home and business addresses (including street address, city, county, and ZIP codes), telephone and fax numbers, email addresses, and website URLs linked to individuals.
Demographic data: Birth dates, death dates (when relating to the individual), ages over 89 (which HIPAA treats specially to reduce re-identification risk), and any dates directly related to an individual (admission, discharge, service dates).
Clinical and medical data
Treatment records: Diagnoses, treatment plans, surgical notes, therapy records, prescription information, and medication lists stored in Electronic Health Records (EHR) or Electronic Medical Records (EMR) systems.
Diagnostic information: Laboratory results, X-rays, MRI scans, CT scans, pathology reports, and any diagnostic imaging or test results linked to specific patients.
Billing and insurance data: Insurance claim forms, explanation of benefits, billing records, payment history, and any financial information tied to healthcare services.
Digital identifiers and biometric data
Technology markers: IP addresses when linked to health information (per OCR guidance), device identifiers for medical equipment, login credentials for patient portals, and digital signatures on medical documents.
Biometric information: Fingerprints used for patient identification, retinal scans, facial recognition data, voice patterns, and any other unique biological identifiers stored electronically.
Photographic evidence: Full-face photographs, images of distinctive physical characteristics, and any visual documentation that could identify patients.
Redaction failures: The unacceptable cost of compromised ePHI security
Mistakes made during the redaction of data can cause financial implications and long-term legal issues. Here are examples of organizations that have been fined millions of dollars for failing to redact ePHI information.
Manasa Health Center ($30,000 Settlement - 2021)

- The Issue: “This case directly involved an impermissible disclosure of protected health information (PHI) by a psychiatric service provider in response to a negative online review.” The organization publicly disclosed patient information to defend itself, which violates the HIPAA Privacy Rule's "minimum necessary" standard and is essentially a failure to redact/limit the sharing of PHI in a public forum.
- The Cost: $30,000 settlement and a corrective action plan. While a minor monetary penalty compared to the multi-million-dollar cases, it directly illustrates a public disclosure failure akin to a redaction error in public commentary.
Gulf Coast Pain Consultants: Clearway Pain Solutions Institute ($1.19 Million Civil Monetary Penalty -December 2024)

- The Issue: “OCR's investigation followed a breach report where a former contractor impermissibly accessed the electronic medical record system to retrieve PHI for potential fraudulent Medicare claims.” This access affected approximately 34,310 individuals. OCR alleged several HIPAA Security Rule violations, including:
- Failure to conduct an adequate risk assessment.
- Failure to review information systems activity.
- Lack of procedures to end system access.
- Lack of procedures for reviewing and changing user access.
- These failures directly led to unauthorized access and impermissible disclosure of ePHI, effectively a failure to "redact" access for an unauthorized party.
- The Cost: $1.19 million Civil Monetary Penalty.
Organizations that leverage legacy redaction tools, such as Adobe, will continue to be prone to errors and may not fully protect their electronic protected health information (ePHI) data.
Where can ePHI be stored
ePHI exists across numerous systems and locations within healthcare organizations, often in places that compliance teams overlook. Comprehensive protection requires understanding all potential storage locations and access points.
Primary healthcare systems
Electronic Health Records (EHR): Centralized patient data systems containing comprehensive medical histories, treatment plans, diagnostic results, and clinical documentation.
Electronic Medical Records (EMR): Practice-specific systems focusing on patient care within individual healthcare organizations, including treatment notes and administrative data.
Practice Management Systems: Administrative platforms handling scheduling, billing, insurance verification, and patient registration information.
Communication and collaboration platforms
Email systems: Patient communications, consultation requests, lab results, and administrative correspondence containing ePHI require encryption and access controls.
Messaging platforms: Secure messaging systems used for clinical communication, patient portals, and telehealth platforms facilitating remote consultations.
File sharing services: Cloud storage solutions, document management systems, and collaboration platforms where medical documents may be stored or transmitted.
Mobile and remote access points
Mobile devices: Smartphones, tablets, and laptops used by healthcare providers for accessing patient information, especially in telemedicine and home healthcare scenarios.
Wearable technology: Medical monitoring devices, fitness trackers integrated with healthcare systems, and remote patient monitoring equipment.
Backup and archival systems: Disaster recovery systems, automated backup solutions, and long-term data storage systems maintaining historical patient records.
Third-party and vendor systems
Business associate platforms: Systems operated by billing companies, transcription services, IT support providers, and other vendors processing ePHI on behalf of covered entities.
Cloud service providers: Amazon Web Services, Microsoft Azure, Google Cloud, and other cloud platforms hosting healthcare applications and data storage.
Analytics and reporting systems: Business intelligence platforms, quality improvement databases, and research systems containing de-identified or pseudonymized patient data.
Who must comply with ePHI requirements
HIPAA's ePHI protection requirements extend far beyond hospitals and doctors' offices, creating compliance obligations for numerous organizations and individuals throughout the healthcare ecosystem.
Covered entities (primary responsibility)
Healthcare providers: Hospitals, medical practices, dental offices, mental health providers, chiropractors, nursing homes, pharmacies, and any provider who electronically transmits health information in connection with standard transactions.
Health plans: Health insurance companies, HMOs, company health plans, government programs (Medicare, Medicaid), and any entity providing or paying for healthcare costs.
Healthcare clearinghouses: Organizations processing health information between providers and payers, including billing companies and entities converting data formats for electronic transactions.
Business associates (contracted compliance)
Technology vendors: EHR vendors, cloud service providers, IT support companies, and software developers handling ePHI on behalf of covered entities.
Administrative services: Billing companies, transcription services, legal firms representing healthcare entities (when performing services involving ePHI disclosure or access), accounting firms, and consultants accessing ePHI.
Third-party processors: Marketing companies handling healthcare communications, data analytics firms, research organizations, and quality improvement contractors.
Individual professionals and employees
Healthcare workers: Physicians, nurses, medical assistants, administrative staff, and any employee with access to ePHI must follow organizational security policies and procedures.
Contractors and consultants: Independent professionals working with healthcare organizations, temporary staff, and specialists providing services requiring ePHI access.
Students and trainees: Medical students, nursing students, residents, and interns receiving clinical training must comply with ePHI protection requirements.
Enforcement and penalties apply to all levels
Organizational responsibility: Covered entities face institutional penalties for HIPAA violations, with maximum aggregate annual penalties up to $2.1 million per violation category (as adjusted by recent HHS updates).
Individual accountability: Healthcare workers can face criminal prosecution for willful ePHI violations, with penalties including imprisonment up to 10 years and personal fines up to $250,000.
Contractual obligations: Business associates must maintain compliance through formal agreements and face direct penalties for violations, not just contract termination.
The key principle: any person or organization that creates, receives, maintains, or transmits ePHI must implement appropriate safeguards, regardless of their primary business function or size.
Redaction: A top security measure against ePHI data loss
AI-powered redaction from Redactable leverages military-grade encryption protection, ease-of-user, while reducing human error compels the legal community, healthcare providers, government agencies, and financial services firms to adopt this solution strategy.
- Ensuring Permanent Redaction: Automated redaction tools, guarantee the complete and irreversible removal of sensitive ePHI, including hidden metadata.

- Minimizing Human Error: By leveraging AI and OCR, these tools automate the redaction process, reducing the likelihood of human oversight or inconsistency.
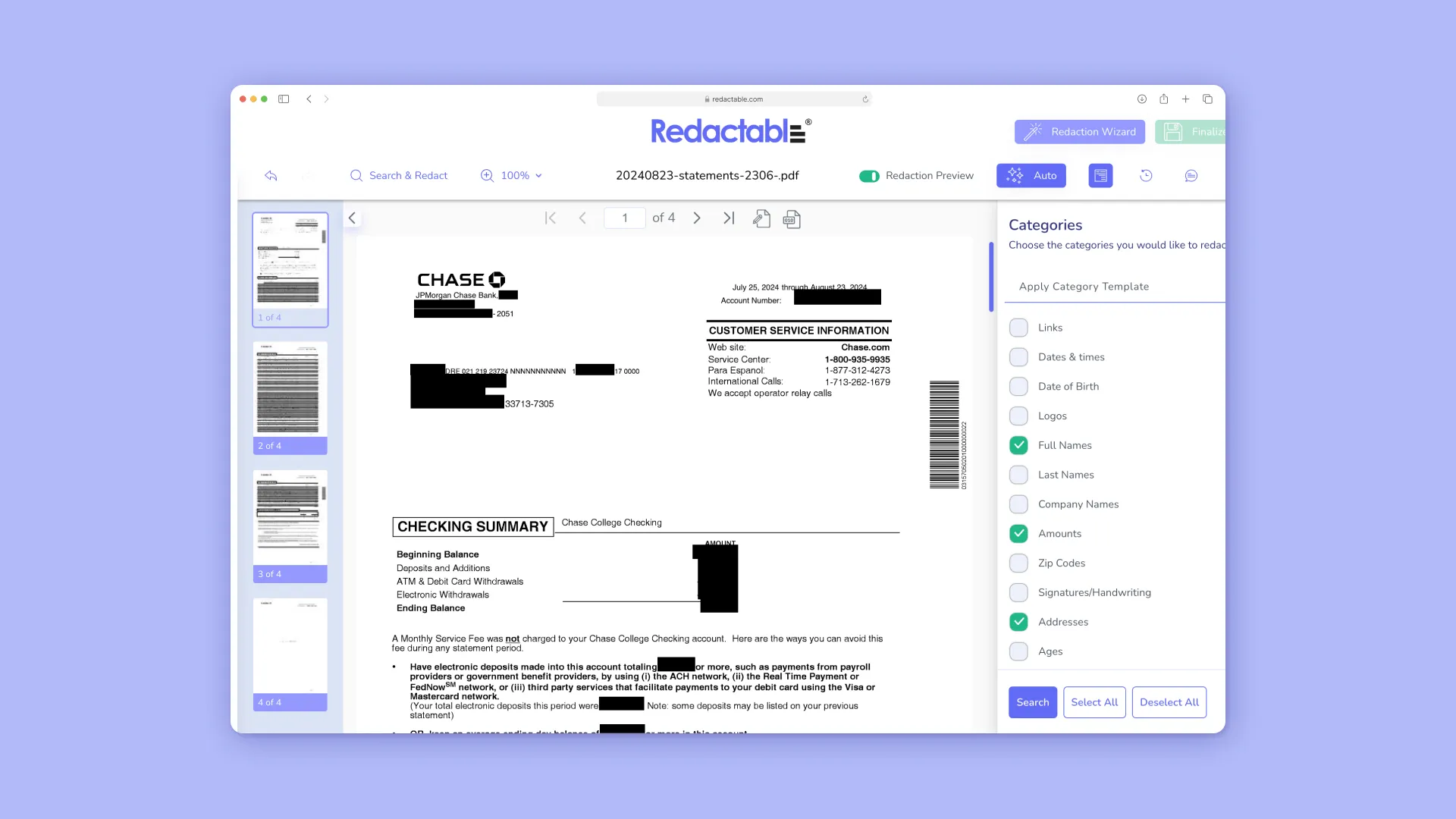
- Streamlining Compliance and Efficiency: Automated redaction significantly reduces the time and resources required for document review and redaction, converting lengthy manual tasks into efficient, automated processes.
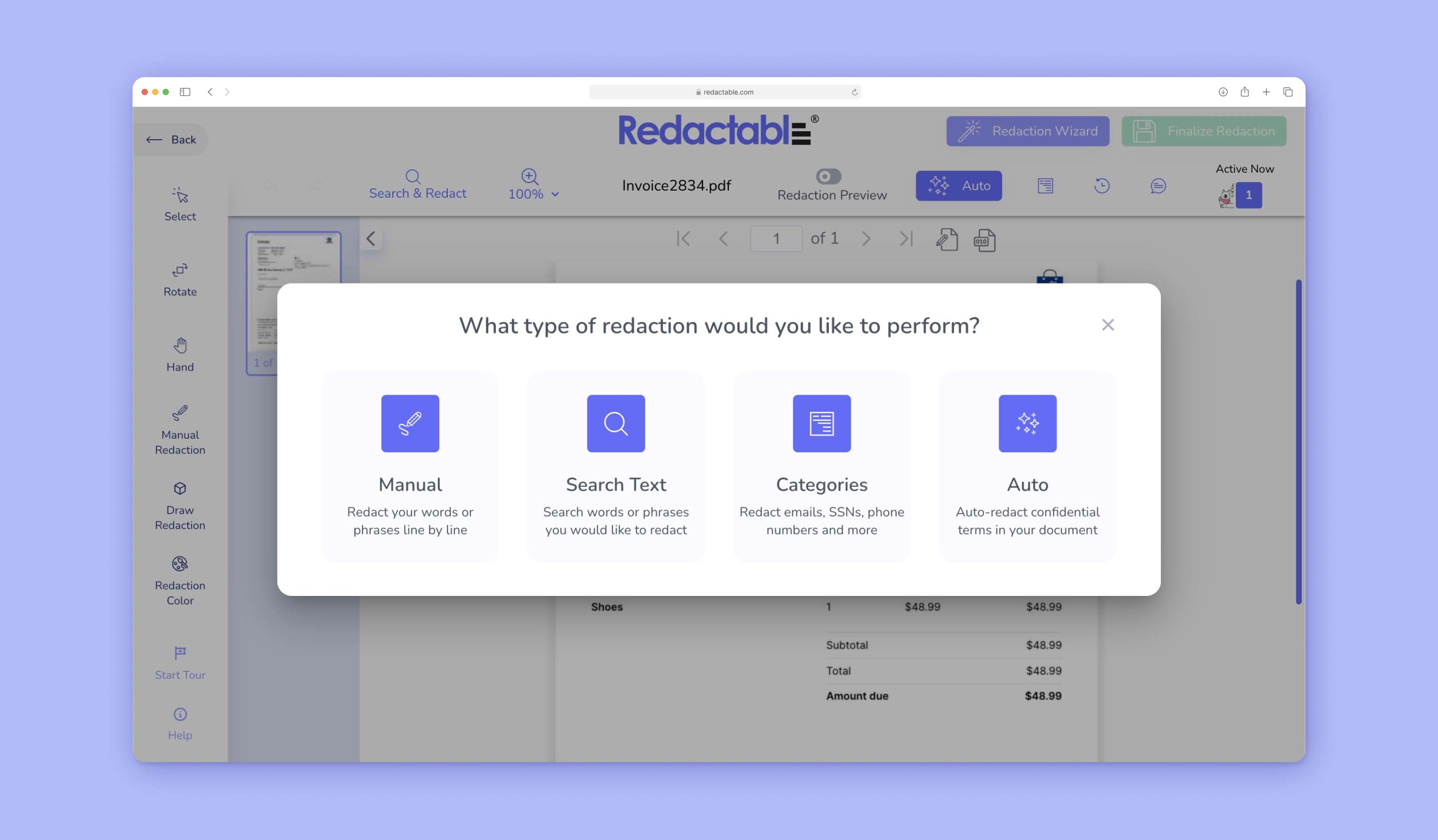
- Providing Audit Trails and Justification: The Redactable.com software creates comprehensive audit logs and certificates that detail every redaction action.
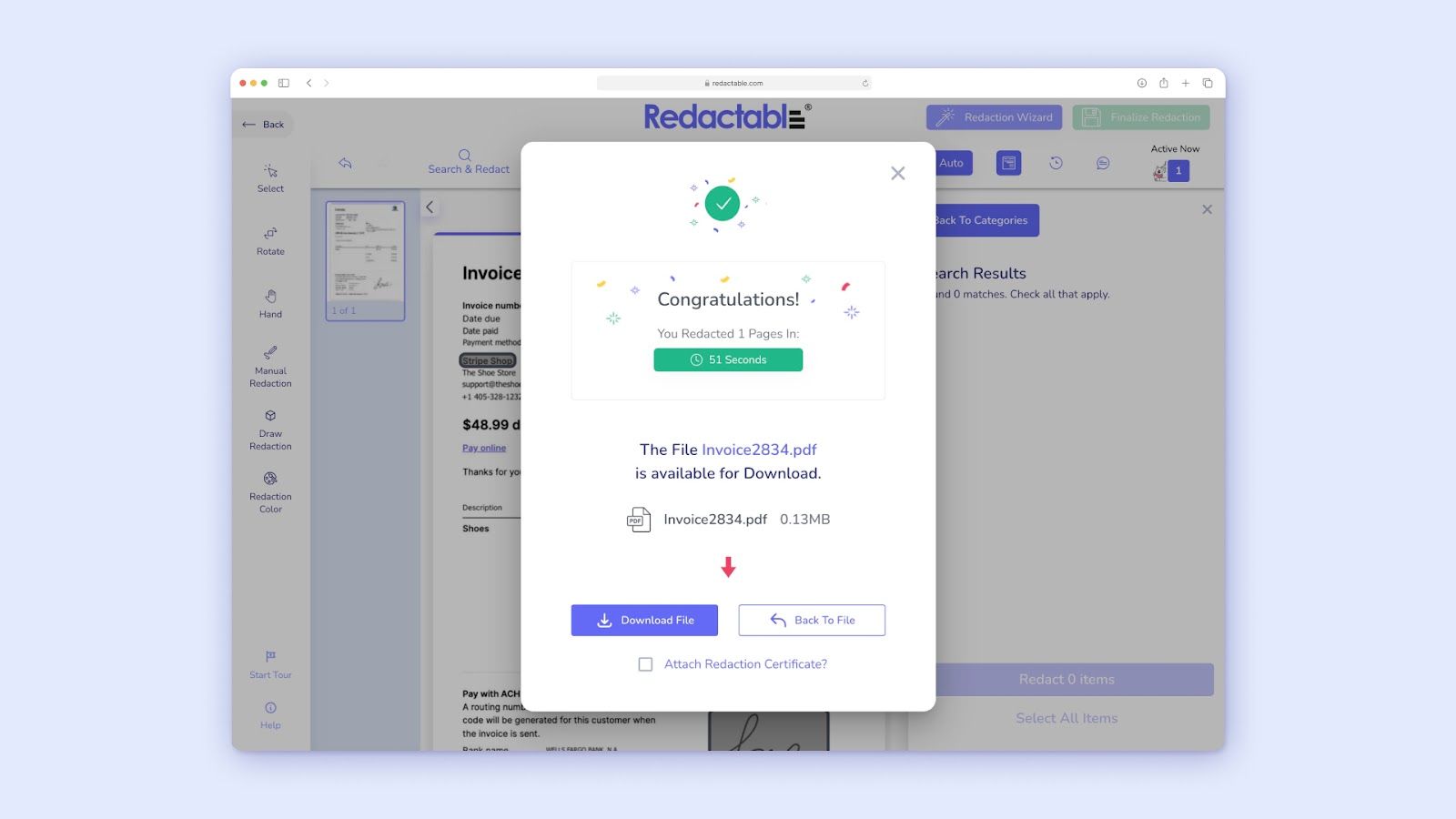
- Preventing Costly Fines and Reputational Damage: By ensuring accurate and permanent ePHI redaction, these tools directly help organizations avoid severe HIPAA violation fines and protect their reputation.
.jpeg)
Sign up today for a free trial and book a demo to see how Redactable can reduce your risk of ePHI data loss.







