Imagine a federal prosecutor uploading what they believe is a properly redacted court filing. Within hours, a journalist copies text from the "blacked out" sections, pastes it into a text editor, and publishes grand jury testimony that was never supposed to see daylight. The court orders an emergency seal, demands explanations, and the case makes headlines as another "redaction failure."
This scenario isn't uncommon - it follows the pattern of multiple real incidents where black rectangles were overlaid on text without actually removing the underlying content. The failures weren't sophisticated hacks. In most cases, people simply drew visual masks over sensitive information, leaving the actual text completely intact and searchable.
Courts have sanctioned parties for failed redactions that exposed confidential data on public dockets. The consequences: forced re-sealing of documents, corrective productions, attorney fee awards, and damaged credibility with judges who expect basic competence in protecting sensitive information.
Here's what makes redaction failures so common: most professionals treat "redact" as a cosmetic editing step, not a risk-control function. They assume someone else checked it, delegate it to junior staff under time pressure, and use quick visual fixes instead of defensible methods.
The reality: redaction is mandated by Federal Rule of Civil Procedure 5.2 for court filings containing social security numbers, birth dates, and minors' names. Failing to redact properly can waive confidentiality and trigger sanctions. Federal guidance on protecting personally identifiable information treats improper disclosure as a security incident requiring the same response as any other data breach.
This article unpacks what "redact" really means in law and practice, how it differs fundamentally from editing, the myths that lead to catastrophic failures, and a practical framework for avoiding black-box mistakes that can overturn months of careful legal work or compliance efforts.
What does "redact" mean in law and practice?
Redact means obscuring or removing confidential information from a document before sharing it, while leaving non-sensitive content visible. It's retroactive editing specifically to protect privileged communications, personal privacy, trade secrets, or other information whose disclosure would create legal or security risks.
The term carries specific legal weight. Legal dictionaries define redaction as the process of removing confidential material to protect attorney-client privilege and privacy rights. Courts and regulatory agencies use "redact" to describe a compliance mechanism, not casual document cleanup.
Read also: What does redacted mean in law
How courts and rules use the term
Federal Rule of Civil Procedure 5.2 establishes redaction as a mandatory privacy protection in court filings. The rule requires parties to redact:
- Social security numbers (show only last four digits)
- Taxpayer identification numbers (show only last four digits)
- Birth dates (show only year)
- Financial account numbers (show only last four digits)
- Names of minors (use initials only)
This isn't a suggestion - it's a procedural requirement. Failure to redact these identifiers from public filings violates the rule and can result in orders to file corrected versions, seal documents retroactively, or face sanctions.
Many local court rules and administrative agencies adopt similar or more expansive redaction requirements. State courts, federal agencies responding to FOIA requests, and regulatory bodies all use "redact" with the same compliance meaning: removing information whose disclosure would violate privacy laws, confidentiality obligations, or protective orders.
Why "redact" appears in so many contexts
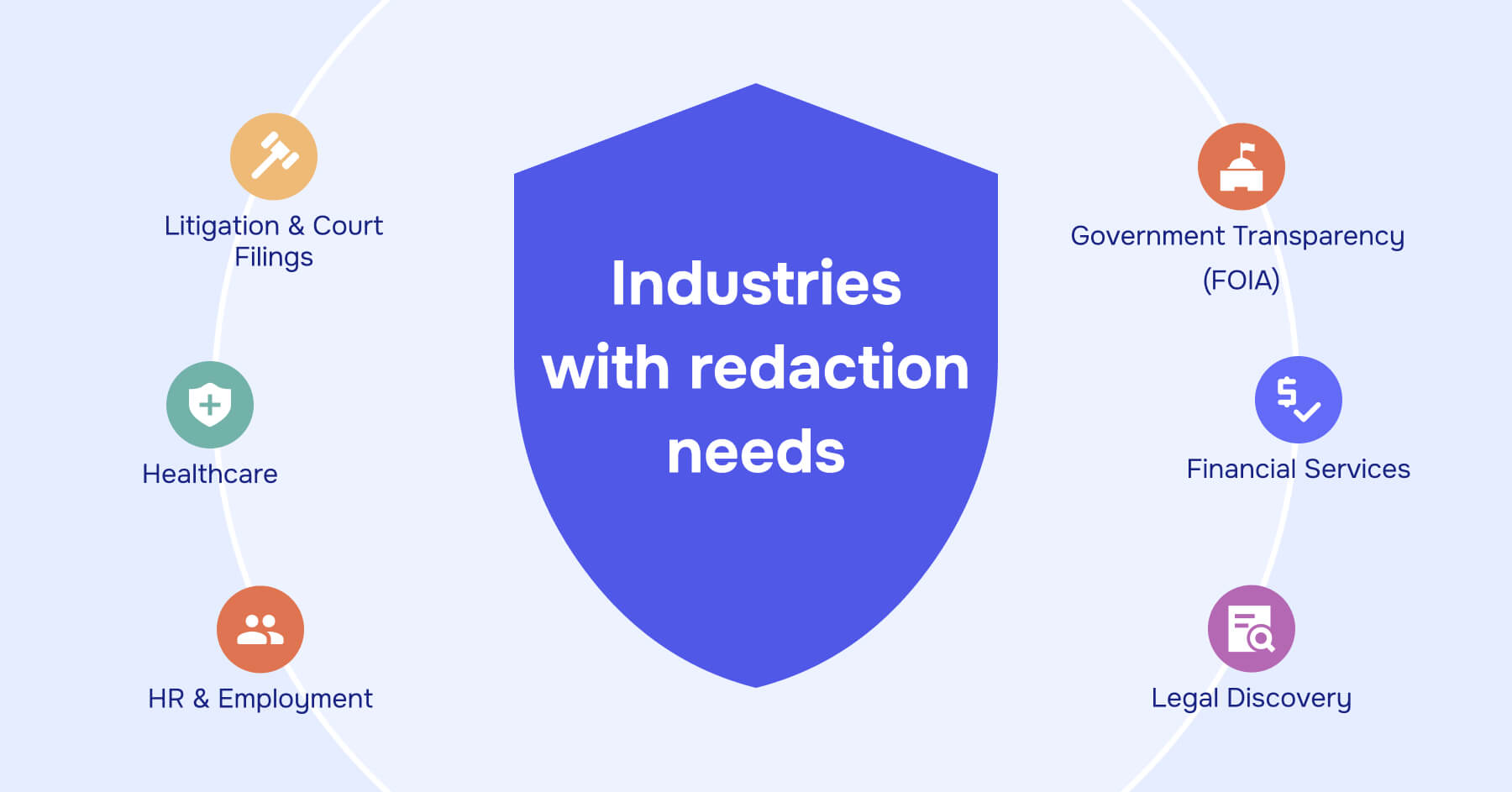
You encounter redaction requirements across multiple domains:
Litigation and court filings: Protecting personal identifiers, privileged communications, trade secrets, and confidential settlement terms in public dockets
Government transparency: Balancing public records access with individual privacy in FOIA responses, open records requests, and agency disclosures
Healthcare: Removing or de-identifying protected health information from medical records shared for research, quality assurance, or legal compliance under HIPAA and related privacy rules
HR and employment: Protecting employee personal information in records shared with regulators, auditors, or other employees during investigations
Financial services: Redacting account details, social security numbers, and other sensitive data from documents shared with third parties or produced in regulatory examinations
Legal discovery: Removing privileged attorney-client communications and work product from documents produced to opposing parties
Each context has specific rules defining what must be redacted, but the underlying principle remains constant: certain information carries legal, privacy, or security risks that require removal before broader disclosure.
Redaction vs. editing: Why the distinction matters
Most document work involves editing - improving clarity, fixing errors, strengthening arguments. Redaction is different in purpose, method, and consequences.

Read also: What is redaction? A complete guide
Conceptual difference
Editing improves language, structure, and readability. You're making the document better at communicating its intended message. Good editing is invisible—readers shouldn't notice the editor's hand.
Redaction removes or masks data whose disclosure would create legal, ethical, or security risk. You're not improving the document; you're protecting specific information from exposure. Redaction deliberately leaves visible evidence that something was removed—black bars, "[REDACTED]" markers, or white space where content used to be.
The purposes diverge completely. Editing serves persuasion and comprehension. Redaction serves compliance and risk management.
Consequences difference
A bad edit might make a brief less persuasive or introduce grammatical errors. Embarrassing, perhaps, but typically fixable with corrections.
A bad redaction can:
- Violate court rules and trigger judicial sanctions
- Breach privacy laws and expose the organization to regulatory action
- Waive attorney-client privilege and undermine litigation strategy
- Enable identity theft when personal identifiers leak into public records
- Damage organizational reputation when "failed redaction" becomes a news story
Cases exist where improper redaction on e-filing systems exposed protected testimony or personal identifiers, prompting judges to demand explanations, award attorney fees to opposing counsel, and question the competence of the offending party's legal team.
The stakes are fundamentally different. Editing errors affect quality. Redaction failures affect legal compliance, security posture, and evidentiary integrity.
Why the confusion persists
Both activities involve changing documents. Both often happen in the same software. Both can be delegated to support staff. These surface similarities mask the profound difference in consequences.
Organizations that treat redaction as "just another editing task" consistently make preventable mistakes. Those that recognize redaction as a distinct compliance function—with specific training, verification steps, and accountability—avoid most failures.
What actually needs to be redacted?
Redaction requirements depend on context, but certain categories appear across multiple domains.
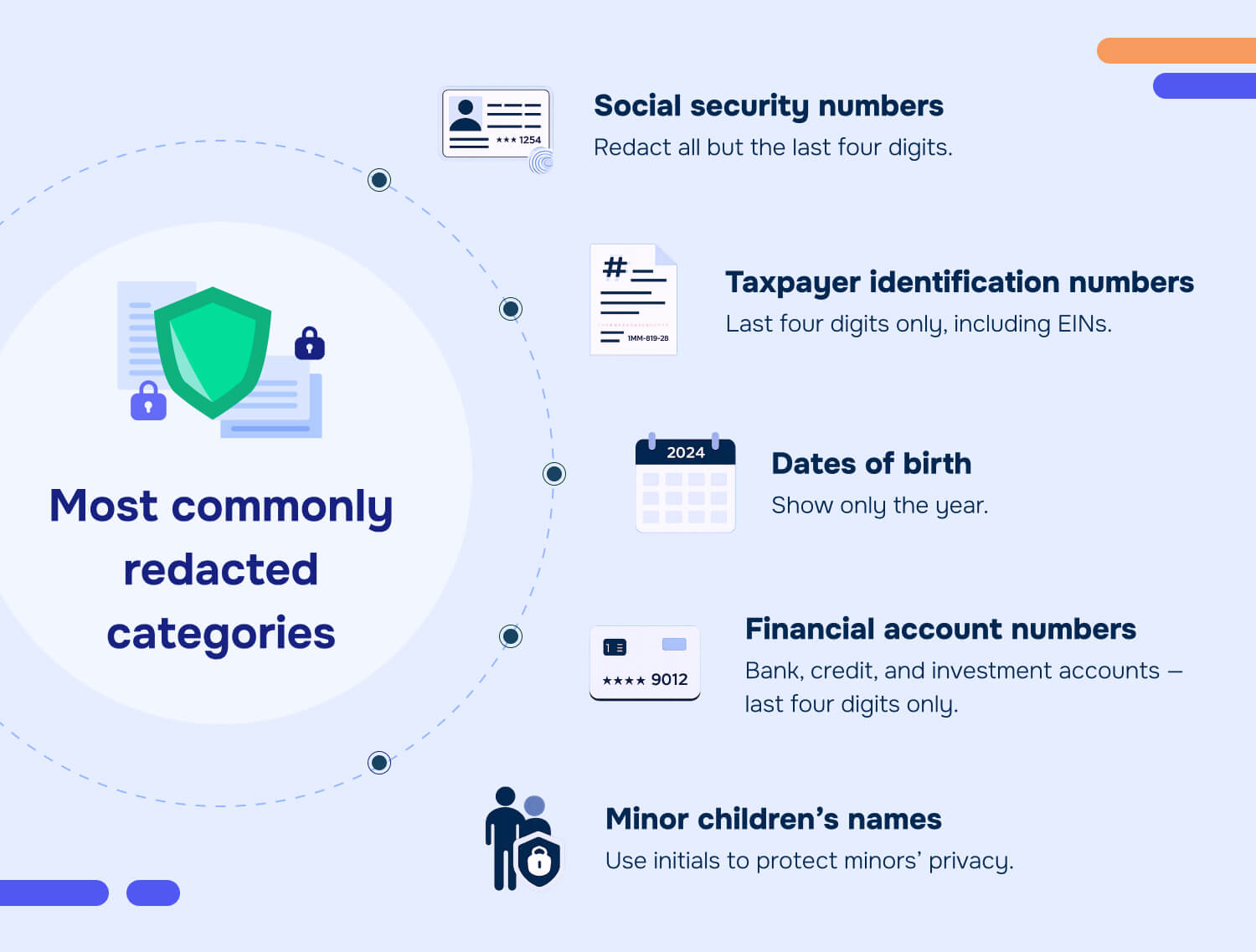
Core categories from court rules
Federal Rule of Civil Procedure 5.2 provides a baseline for court filings:
Social security numbers: Redact all but the last four digits. Full SSNs enable identity theft and financial fraud.
Taxpayer identification numbers: Same rule - last four digits only. Includes employer identification numbers (EINs) when used to identify individuals.
Dates of birth: Show only the year. Full birth dates combined with names become powerful identifiers for fraudulent accounts.
Financial account numbers: Last four digits only. Applies to bank accounts, credit cards, investment accounts, and other financial identifiers.
Minor children's names: Use initials only. Protects children's privacy in proceedings involving abuse, neglect, custody disputes, or juvenile matters.
These categories reflect identifiers with high fraud and privacy risk. But redaction obligations extend well beyond this list depending on your industry and the specific document's purpose.
Broader personally identifiable information
NIST Special Publication 800-122 provides federal guidance on protecting PII. The framework recognizes that combinations of seemingly harmless data points can substantially increase risk.
Examples:
- Name + date of birth + address = high-risk PII requiring protection
- Name + place of birth + mother's maiden name = common security question answers
- Photo + location data + timestamp = tracking and surveillance risks
NIST's approach: assess PII in context. Information that seems innocuous in isolation can become sensitive when combined with other available data.
This matters for redaction decisions. You might not redact someone's hometown in a biography, but you would redact hometown from a document that also contains their full name, birth date, and current address.
Domain-specific sensitive information
Beyond personal identifiers, redaction applies to:
Privileged communications: Attorney-client communications, work product, common-interest materials shared among co-defendants or co-plaintiffs. Disclosure waives privilege.
Trade secrets and confidential business information: Manufacturing processes, customer lists, pricing strategies, merger negotiations. Disclosure harms competitive position and may breach confidentiality agreements.
Medical information: Diagnoses, treatment details, test results, mental health records. HIPAA and state privacy laws require protection.
Law enforcement and security information: Investigative techniques, informant identities, ongoing investigation details, security vulnerabilities. Disclosure can endanger lives and compromise operations.
Sealed or protected information: Content subject to protective orders, confidential settlement terms, classified national security information. Court orders or regulations mandate redaction.
In public records and FOIA contexts, agencies must balance transparency with privacy, redacting medical details, home addresses, and personal information from released documents while preserving public accountability.
Why redaction is so overlooked (and why that's dangerous)
Despite high stakes, redaction consistently receives inadequate attention. Several factors explain this pattern.
Psychology and workflow myths
Many professionals mentally categorize redaction as "formatting" or "cosmetic cleanup"—tasks perceived as low-skill and safely delegated. This underestimates redaction's legal and security significance.
The delegation problem compounds when supervisors assume "someone else checked it." Junior staff members receive documents with instructions to "redact the SSNs" without training on proper methods, verification steps, or consequences of failure. Senior staff members trust that it was done correctly without reviewing the work.
Redaction typically happens at the final step—immediately before filing, publication, or transmission. Time pressure intensifies. The urgent desire to meet a deadline overwhelms the careful attention proper redaction requires. Quick visual fixes substitute for defensible methods.
Technical illusions of safety
Common redaction failures stem from not understanding how PDF and document files work:
Black rectangles drawn over text: Many people use drawing tools or shape layers to cover sensitive information. The underlying text remains in the file, completely intact and searchable. Copy-paste reveals it instantly.
Highlight-based masking: Using black highlighting or text color changes to make text "invisible" leaves the actual text unchanged in the document's data structure.
Font color matching background: Changing text to white on a white background hides it visually but not structurally. The text is still there.
Covered objects: Placing images or shapes over sensitive content in presentation or document software doesn't remove the underlying content—it just layers something on top.
Metadata and hidden data: Comments, tracked changes, hidden text, document properties, and previous versions often contain sensitive information that remains in the file even when not visible on screen.
Investigations and legal ethics commentary are filled with examples where journalists, opposing counsel, or curious readers revealed redacted text by simply copying, pasting, or printing the document. In some cases, adjusting PDF layer visibility or removing covering objects exposed content the author believed was protected.
The "it looks redacted" trap

Visual appearance creates false confidence. If you can't see the sensitive information on your screen, you assume it's truly gone. But files have structure beyond what displays in viewers. Text, metadata, and historical versions persist in ways that visual inspection doesn't reveal.
Testing redaction requires actively trying to break it—attempting to copy text, searching for keywords that should be gone, examining document properties, and opening the file in different applications. Most people skip these verification steps because the document "looks fine."
Consequences of getting redaction wrong
Failed redactions create concrete harms across multiple dimensions.
Privacy and security breaches
When court or agency documents leak personal identifiers, the exposed data enables identity theft, financial fraud, and harassment. Social security numbers appearing in public court dockets allow fraudsters to open accounts, file false tax returns, and access medical records. Home addresses in released records expose domestic violence victims to their abusers.
Federal guidance treats improper PII exposure as a security incident requiring response planning—notification to affected individuals, credit monitoring services, investigation of how the breach occurred, and corrective actions to prevent recurrence.
Legal sanctions and costs
Courts may order documents sealed retroactively, require corrected filings, and award attorney fees or other sanctions when parties fail to redact properly. Judges criticize "technical weaknesses" in redaction and shift costs to the offending party.
Sanctions can include:
- Monetary penalties paid to the court
- Reimbursement of opposing counsel's fees for bringing the issue to the court's attention
- Adverse inferences or evidentiary sanctions in the underlying case
- Referral to disciplinary authorities for attorney misconduct
Beyond formal sanctions, redaction failures waste judicial time addressing preventable problems, damaging the responsible party's credibility with the court.
Loss of privilege and strategic position
Disclosure of privileged or work-product material - even accidentally - can constitute waiver, undermining litigation strategy and forcing production of related documents that would otherwise remain protected.
When privileged communications appear in public filings due to inadequate redaction, opposing counsel argues the privilege has been waived. Courts then must determine whether the disclosure was inadvertent (potentially preserving privilege under Federal Rule of Evidence 502(b)) or negligent (potentially waiving privilege entirely).
Even when privilege survives under Rule 502, strategic damage persists. Opposing counsel has seen your confidential legal analysis, identified your vulnerabilities, and gained insight into your litigation strategy. The bell can't be unrung.
Reputational damage and trust erosion
Organizations that mishandle confidential information face public trust consequences beyond legal penalties. "Bad redaction" stories become news articles that persist online, linked to the organization's name in search results.
Clients, customers, and stakeholders question competence when they learn sensitive data was exposed through preventable errors. Prospective clients conducting due diligence discover the redaction failure and factor it into their risk assessment.
For law firms, redaction failures can trigger malpractice claims when clients suffer damages from disclosed confidential information. For corporations, inadequate redaction can violate contractual obligations to business partners and prompt termination of relationships.
Read also: Unredacted Epstein files show why secure redaction is mandatory, not optional
How to redact properly
Effective redaction requires process, not just tools.
Read our complete guide on how to redact a PDF
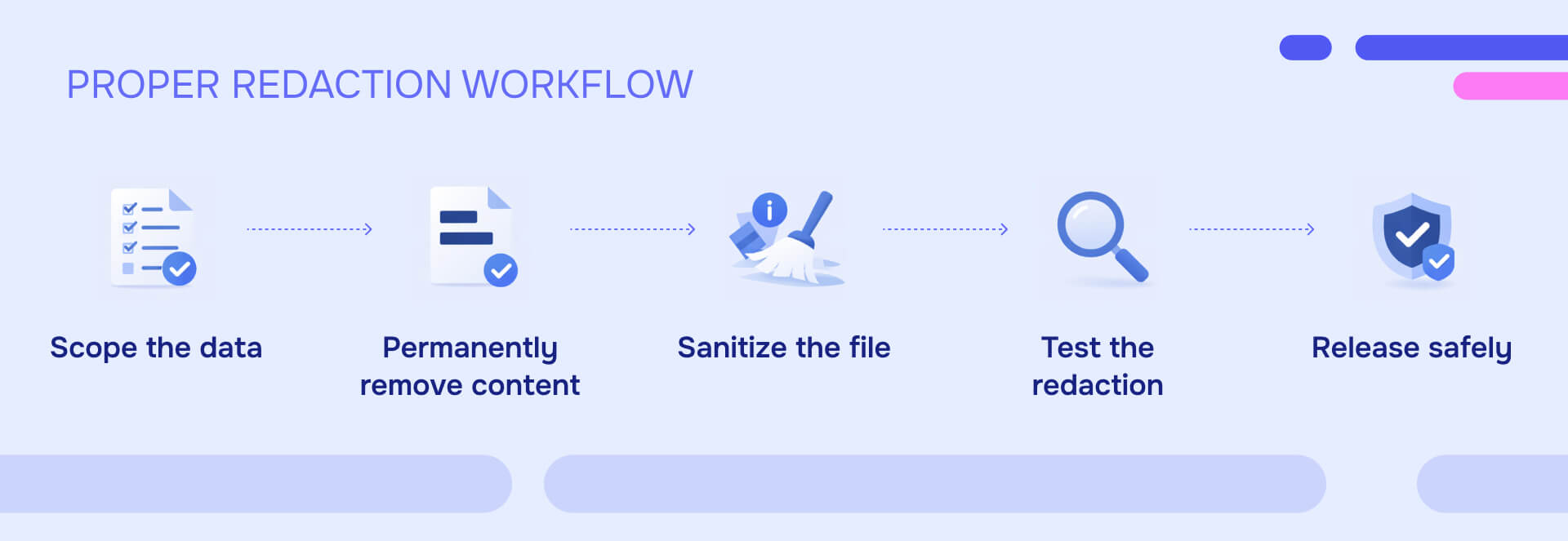
Start with scoping
Before touching a document, identify what types of data must be protected under applicable law, regulation, and court rules.
Ask:
- What jurisdiction's rules apply? Federal courts follow FRCP 5.2, but state courts and agencies have different requirements.
- What type of document is this? Court filings, FOIA responses, discovery productions, and public disclosures each have specific redaction obligations.
- What sensitive information categories are present? Personal identifiers, privileged communications, trade secrets, medical information, sealed content?
- What's the risk if this information is disclosed? Privacy harm, privilege waiver, competitive disadvantage, regulatory violation?
Build a simple internal redaction policy or checklist that references applicable rules and identifies who's responsible for redaction decisions, who performs the redaction, and who verifies it before release.
Use methods that actually remove content
Visual masking doesn't work. You need permanent removal.
Permanent redaction means the sensitive information is completely extracted from the file. It's not hidden under layers, not masked by covering objects, not made invisible through formatting - it's gone. The data doesn't exist in the file's structure.
When evaluating redaction methods:
- Can I select and copy text from redacted areas? (If yes, it's not truly redacted)
- Can I search the document for keywords that should be removed? (If they're found, redaction failed)
- Does the file's metadata contain sensitive information in author fields, comments, or document properties? (This needs separate sanitization)
- Are there previous versions or tracked changes embedded in the file? (These often escape visual redaction)
Government guidance recommends using redaction features built into professional PDF software or dedicated redaction tools designed for compliance purposes, not improvised visual masking methods.
For organizations handling significant volumes of documents requiring redaction - law firms managing discovery, government agencies processing FOIA requests, healthcare providers sharing medical records, HR departments handling employee files - purpose-built redaction tools ensure permanent removal of sensitive data including text, images, and metadata.
Flatten and sanitize documents
After redacting content:
Flatten the document: Convert it to a format where layers, objects, and structures that could hide information are merged into a single visual representation. Many redaction failures occur because covering objects can be moved or deleted to reveal underlying content.
Remove metadata: Document properties (author, company, creation date, edit history), comments, tracked changes, hidden text, and embedded objects all persist in files. Sanitization strips this metadata that often contains sensitive information.
Verify the output: Don't assume redaction worked. Test it.
Test before release
At least one other person should try to "break" the redaction:
- Copy-paste test: Select all text and paste into a text editor. Redacted content should not appear.
- Search test: Search for keywords that should be redacted. They shouldn't be found.
- Metadata test: Check document properties and file information for sensitive data in author fields, comments, or custom properties.
- Visual test in multiple applications: Open the file in different PDF readers and ensure redacted areas remain protected across viewers.
- Print test: Print the document or convert to another format (if that's how it will be used). Sometimes redaction that appears solid on screen fails in other output methods.
This verification step catches most failures before they become public problems. Build it into your workflow as a required step, not an optional check.
Train staff with real examples
Show your team examples of both good and bad redactions from government and court contexts. Demonstrate how common visual masking methods fail and why permanent removal matters.
Include redaction in onboarding for any staff members who will handle sensitive documents. Make it clear that redaction is a compliance function with legal consequences, not a formatting task.
Redaction in the broader privacy and compliance picture
Redaction fits within larger data protection strategies.
One element in layered defenses
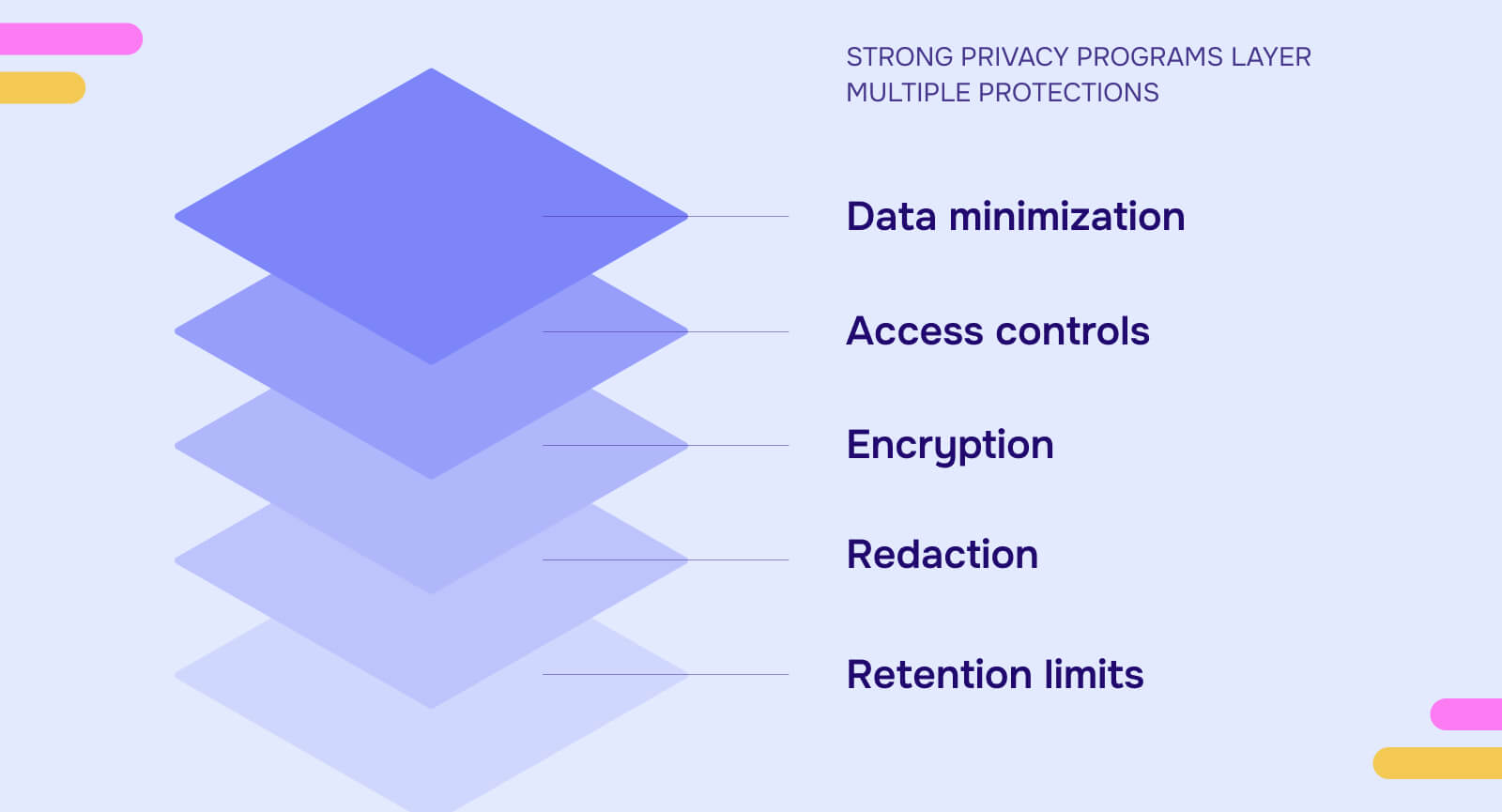
Regulatory guidance treats redaction alongside other data protection techniques - data minimization (collecting only what's necessary), access controls (limiting who can view sensitive information), encryption (protecting data in transit and at rest), and retention limits (deleting data when no longer needed).
Each technique addresses different risks:
- Minimization reduces the amount of sensitive data you hold
- Access controls limit who can reach sensitive data you hold
- Encryption protects sensitive data from unauthorized access during transmission or storage
- Redaction removes sensitive data before broader disclosure
- Retention limits ensure sensitive data doesn't persist indefinitely
Strong privacy programs use all these techniques together. Redaction becomes critical at the boundary - when documents must move from protected internal environments to less controlled external contexts.
Privacy impact assessment integration
Reviewing "where documents go public"—court dockets, FOIA responses, regulatory disclosures, websites—is a critical part of privacy impact assessments and incident response planning.
During privacy impact assessments, identify:
- What documents your organization routinely makes public or shares externally
- What sensitive information those documents typically contain
- Whether current redaction practices adequately protect that information
- Who's responsible for redaction decisions and execution
- How redaction is verified before release
Organizations that discover redaction failures during privacy assessments can fix them before they cause harm. Those that overlook redaction during assessment planning learn about gaps when failures occur publicly.
When redaction intersects with your work
Rethink "redact" every time you encounter it. The word signals that legal duties, privacy risks, and reputational stakes are present - not just a cosmetic document adjustment.
If you see "redact the SSNs before filing" or "this needs to be redacted before release," recognize you're being asked to perform a compliance function with real consequences. Approach it with the same care you'd give any task that could result in sanctions, regulatory violations, or security incidents.
Practical next steps:
- Audit recent redactions: Pull a sample of recently filed or shared documents that should have been redacted. Verify the redaction actually worked using the tests described in Section 6.
- Update internal guidelines: Name specific individuals responsible for redaction decisions and verification. Document what methods are acceptable and what constitutes adequate testing.
- Bring redaction into governance conversations: Discuss redaction practices with counsel, privacy officers, and compliance teams. Ensure everyone understands it's a risk-control function, not clerical work.
- Invest in proper tools: For organizations with ongoing redaction needs, purpose-built tools designed for permanent removal pay for themselves by preventing a single failure.
Take action on redaction
The smallest word carries the biggest consequences because redaction sits at the intersection of legal compliance, privacy protection, and security risk management.
Every "redact this before filing" instruction represents a moment where proper execution prevents harm and careless execution creates liability. Approach redaction with the seriousness it deserves - as a compliance function requiring specific skills, verification steps, and accountability, not as cosmetic document cleanup.
Invest in understanding proper redaction methods, use tools designed for permanent removal rather than visual masking, build verification testing into your workflows, and train everyone who handles sensitive documents on why redaction matters.
The organizations that get redaction right avoid sanctions, privilege waivers, privacy breaches, and reputation damage. Those that treat it casually discover the consequences when failures become public.
Need to redact sensitive information from your documents? Ensure complete, permanent removal of confidential data - not just visual masking that leaves content recoverable. Try Redactable for AI-powered permanent redaction with guaranteed metadata removal, or book a demo to see redaction in action.







