Heritage Valley Health System paid $950,000 in a 2023 HIPAA settlement after a ransomware attack exposed Protected Health Information. OCR's investigation found inadequate risk analysis and audit controls - the organization couldn't demonstrate proper security measures because they lacked comprehensive documentation of system access and security activities.
The audit control failure transformed a security incident into a compliance catastrophe.
IBM's 2025 Cost of Data Breach Report found that 53% of breaches involved customer PII like Social Security numbers, medical records, and financial data. Organizations with comprehensive audit trails could reconstruct attack sequences, identify compromised data, and demonstrate due diligence to regulators. Those without audit trails faced average breach costs exceeding $4.5 million - and regulatory penalties that multiplied those costs.
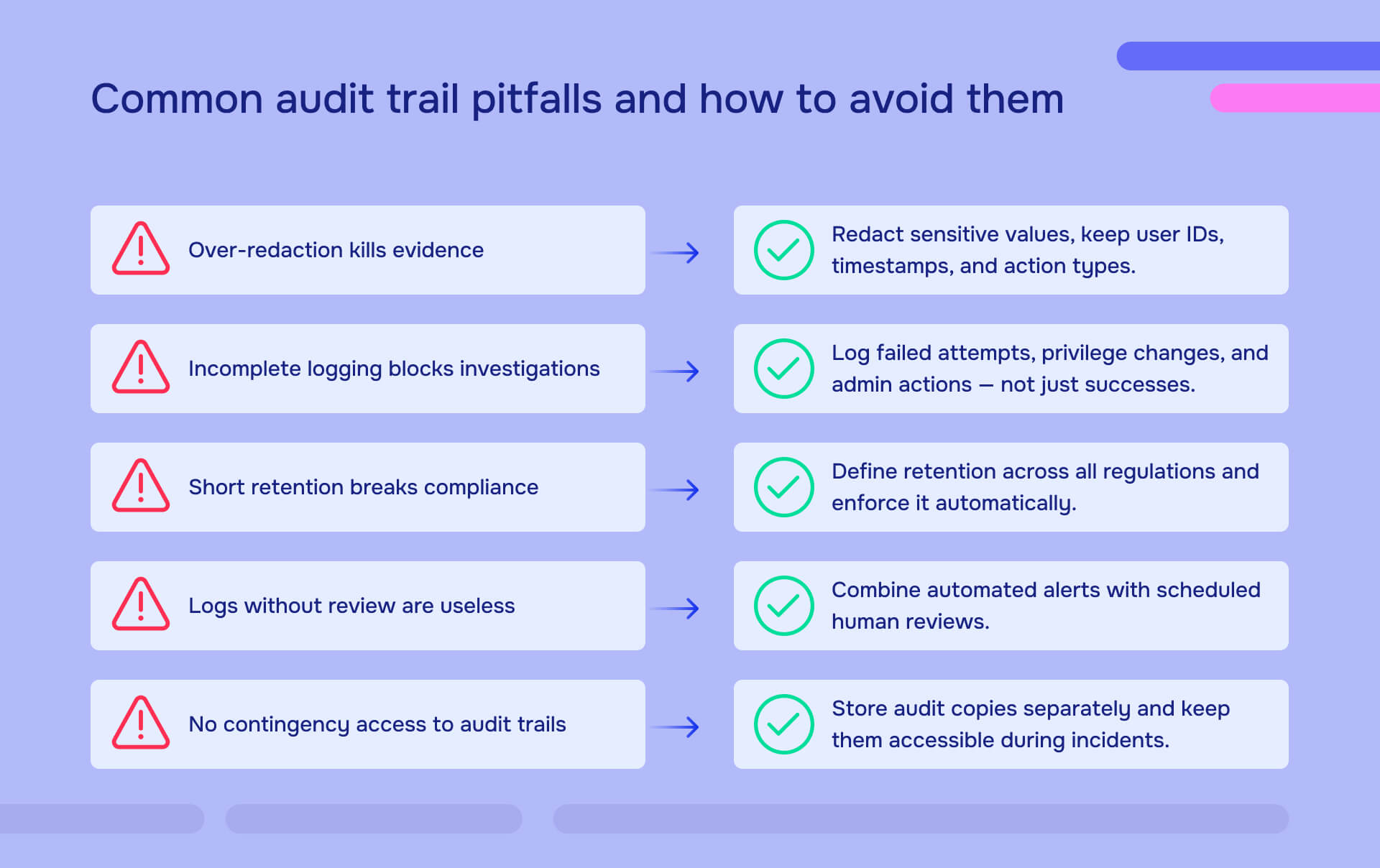
Research shows that 87% of organizational records contain some form of PII requiring audit trail documentation. Yet many organizations either maintain inadequate logs that can't satisfy auditors, or over-redact their audit trail reports and accidentally obscure the very evidence regulators need to verify compliance.
This guide explains what audit trails are, why they're legally required across healthcare, financial services, and data protection regulations, how to implement them properly, and how to balance transparency requirements with PII protection when generating audit trail reports.
What is an audit trail: meaning and definition
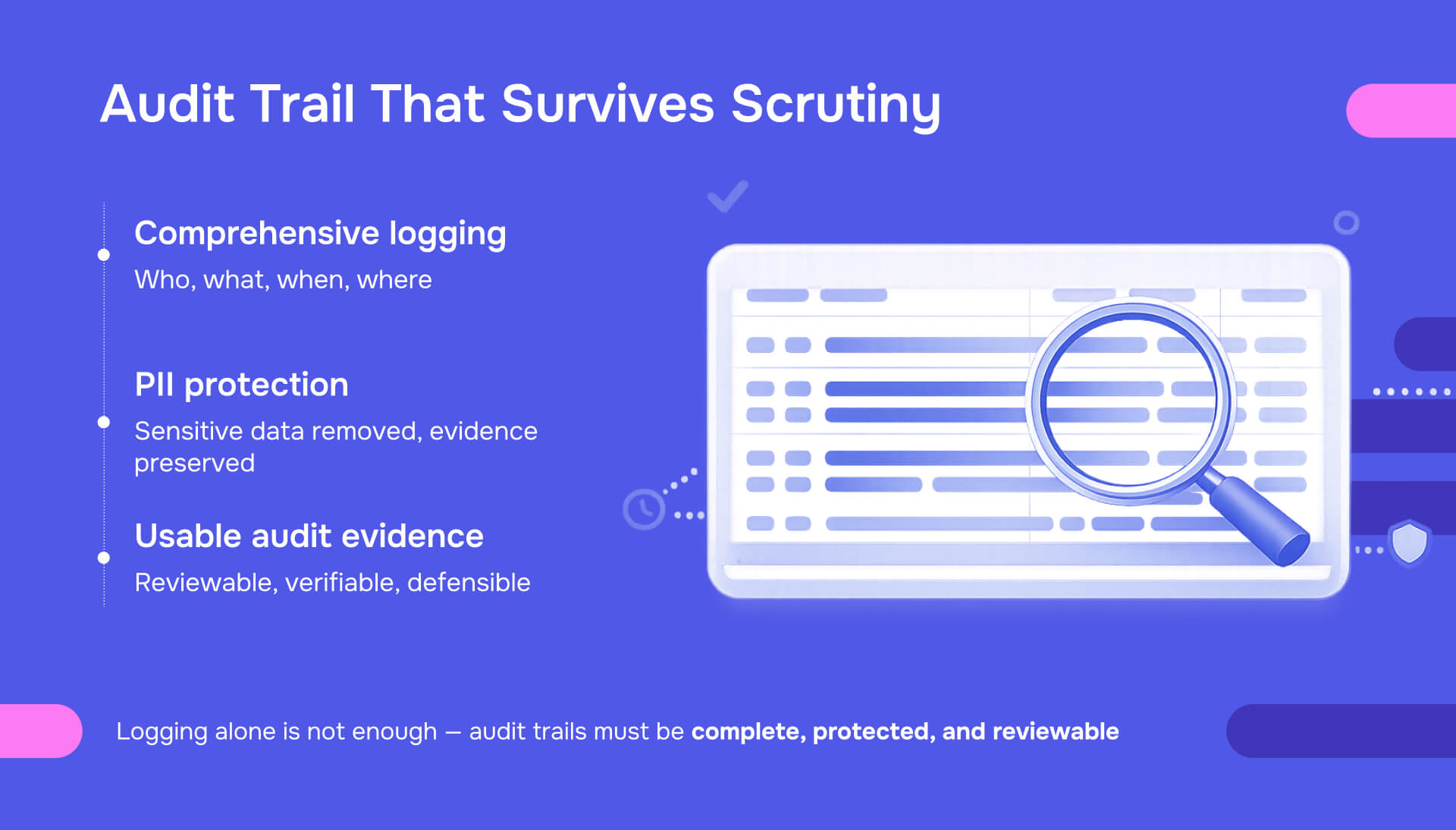
An audit trail is a chronological record of system activities that documents who accessed data, what actions they performed, when those actions occurred, and where they happened within a system. NIST defines it as documentary evidence that enables reconstruction of the sequence of activities affecting any operation or transaction.
The key distinction: audit trails differ from simple system logs because they're designed for forensic review and compliance verification, not just technical troubleshooting.
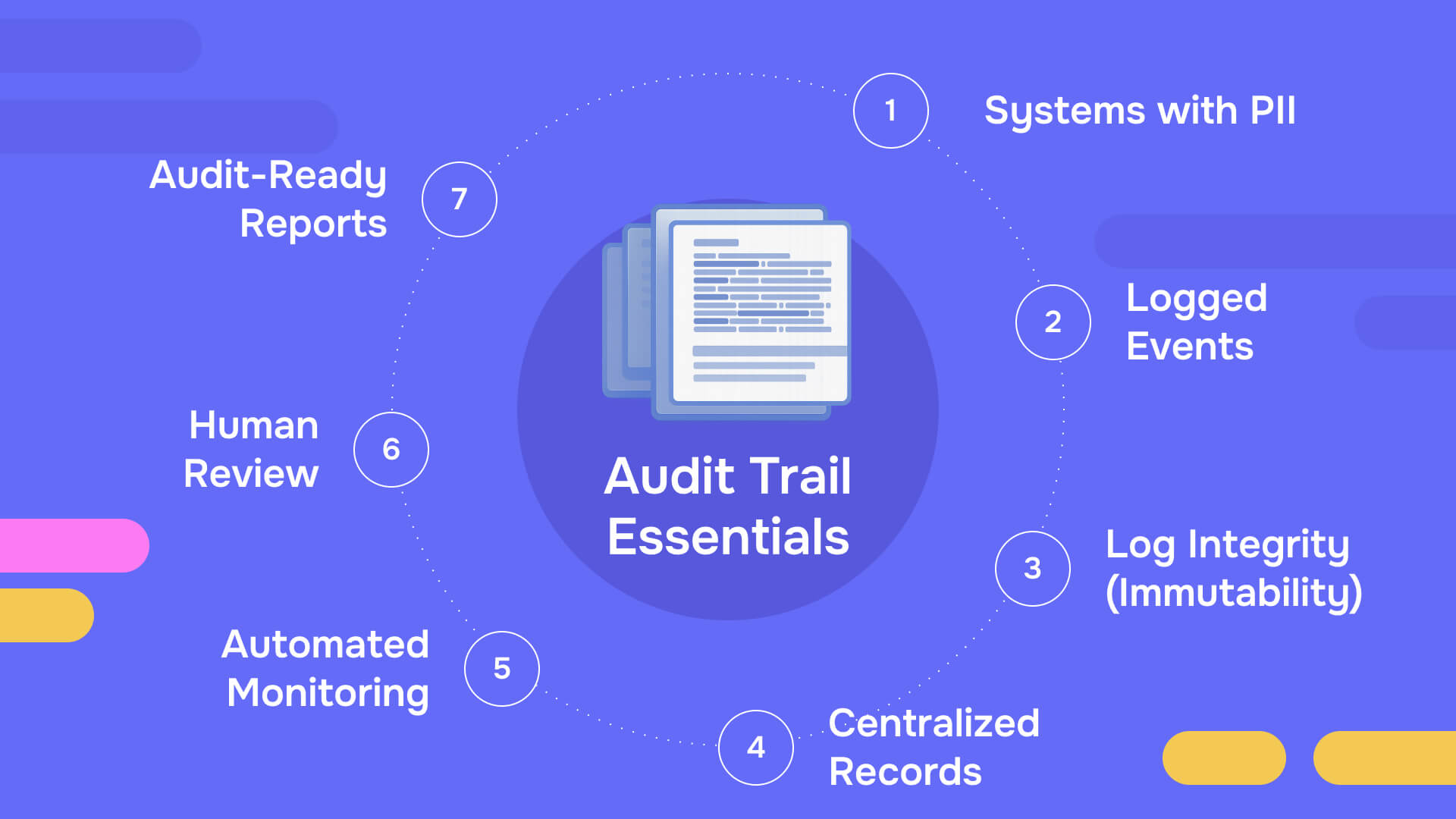
A complete audit trail captures:
- Who: User identification, authentication credentials, role assignments
- What: Specific actions - view, edit, delete, download, print, share
- When: Precise timestamps for each activity
- Where: System location, terminal ID, IP address, geographic data when relevant
- Why: Business justification or authorization basis when applicable
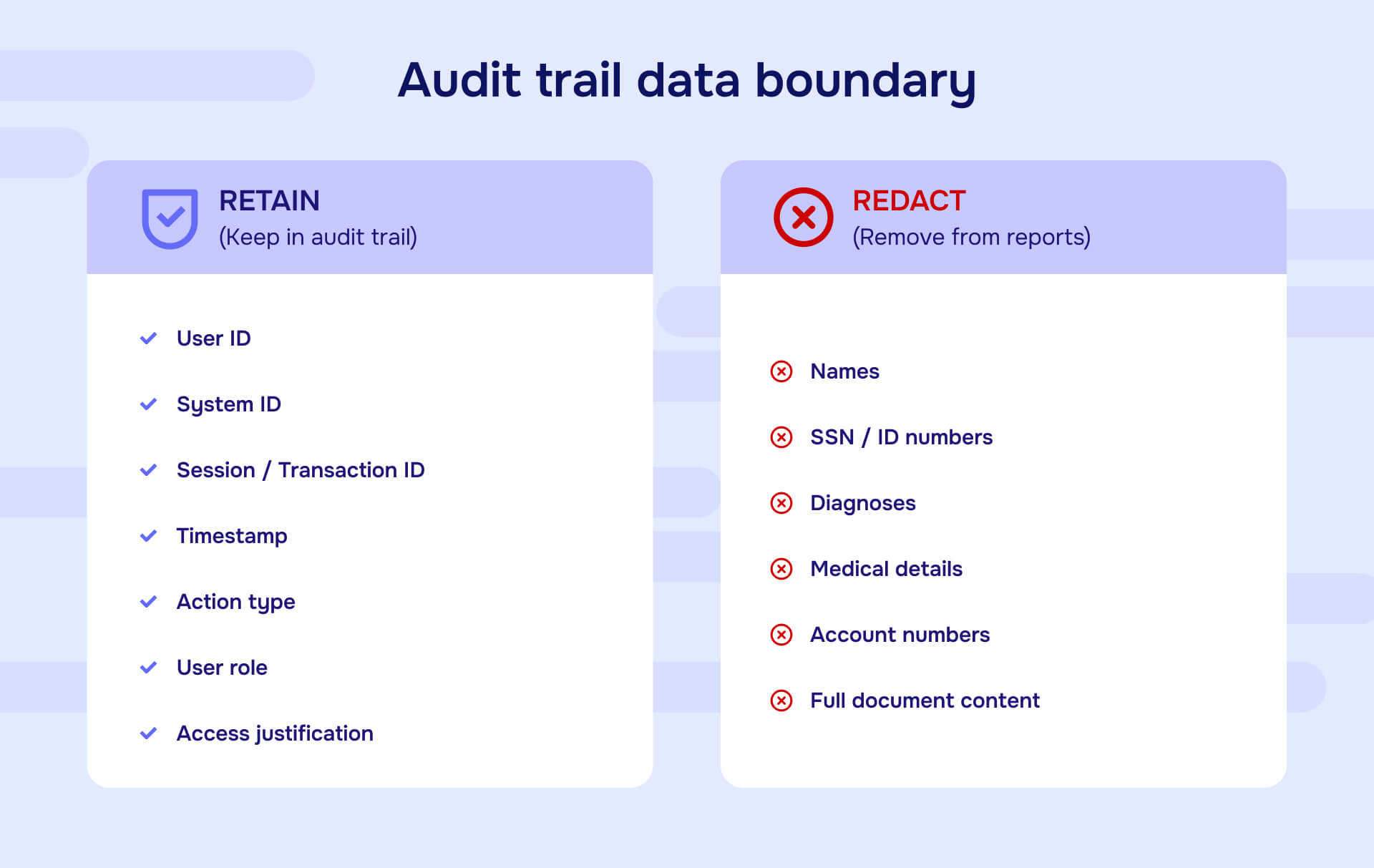
For PII protection, audit trails create a paradox: they must log data handling activities without storing the raw sensitive data itself. The trail documents that "User ID 47 accessed Patient Record 12345 at 14:32 on January 8, 2026" - but the audit trail itself shouldn't contain the patient's name, diagnosis, or other Protected Health Information.
This balance between transparency and privacy is what makes audit trail implementation complex for organizations handling sensitive data.
What is the purpose of audit trails
The primary purpose of audit trails is accountability - when every data access and modification is logged with user attribution and timestamps, unauthorized activity becomes detectable and individuals become responsible for their actions.
This accountability serves four critical functions:
Breach detection and investigation: Audit trails provide forensic evidence to determine what data was accessed, by whom, and whether exfiltration occurred. Without audit trails, organizations can't answer basic incident response questions during breaches.
Regulatory compliance: HIPAA's Audit Controls (45 CFR §164.312(b)) mandate mechanisms that record and examine activity in systems containing ePHI. During OCR audits, organizations must produce these records - without audit trails, compliance cannot be demonstrated.
Fraud prevention: Regular audit trail reviews reveal patterns indicating fraudulent activity - employees accessing records they have no business reason to view, unusual access volumes, modifications to financial data outside normal processes.
Legal defensibility: When litigation involves data handling practices, audit trails provide objective evidence. Employment disputes, malpractice cases, contract disagreements - audit trails resolve factual disputes with verifiable records.
The main purpose of audit trails is turning data handling from an invisible, unverifiable activity into a documented, reviewable process. Organizations without audit trails can't detect problems, can't prove compliance, and can't defend their practices when questioned.
Audit trail requirements across regulations
Multiple regulations mandate specific audit trail implementation and retention requirements:
Frequently asked questions
An audit trail is a chronological record documenting who accessed data, what actions they performed, when those actions occurred, and where they happened within a system. It's important because regulations like HIPAA, GDPR, and SOX legally require audit trails, they provide forensic evidence during breach investigations, they demonstrate compliance during regulatory audits, and they create accountability that deters unauthorized access. Organizations without audit trails cannot prove they implemented required safeguards, cannot investigate incidents effectively, and face significantly higher penalties when breaches occur.
Complete audit trails must include: user identification showing who performed actions, precise timestamps documenting when actions occurred, specific action types (view, edit, delete, download, print, share), system locations identifying where actions originated (terminal IDs, IP addresses), authorization levels showing what permissions users possessed, business justifications when applicable, and session information documenting duration and scope of access. For regulatory compliance, audit trails should capture these elements without storing the raw sensitive data that actions involved - documenting that "Patient Record 84732" was accessed rather than including the actual medical information.
In healthcare, audit trails serve multiple critical purposes required by HIPAA: demonstrating that only authorized personnel access Protected Health Information for legitimate treatment, payment, or operations purposes; detecting inappropriate access such as employees viewing records of family members or celebrities; enabling investigation when breaches occur to determine what PHI was compromised; proving compliance during Office for Civil Rights audits; and creating accountability that deters privacy violations. Healthcare audit trails must be retained for six years and reviewed quarterly to identify anomalies, with the audit trail documentation itself becoming part of the compliance record.
Retention requirements vary by regulation: HIPAA requires six years from creation or last active date for healthcare audit trails; GDPR doesn't specify exact timelines but requires retention as long as processing activities continue; CCPA mandates minimum 12 months for consumer request records; SOX requires retention for seven years for financial audit trails; and NIST recommends retention periods aligned with operational and regulatory needs, typically multi-year for systems containing PII. Organizations subject to multiple regulations must retain audit trails for the longest applicable period, and retention policies should account for litigation holds that may require preservation beyond standard timelines.
System logs record technical events for troubleshooting and performance monitoring - server errors, network connections, application crashes. Audit trails are specifically designed to document security-relevant activities for compliance verification and forensic investigation - who accessed sensitive data, what modifications occurred, whether proper authorization existed. While system logs may capture some of the same information, audit trails are structured to enable reconstruction of event sequences, demonstrate regulatory compliance, and provide evidence for investigations. Audit trails require immutability, defined retention periods, regular review protocols, and often must be produced for regulators and courts - requirements that don't typically apply to general system logs.
Small organizations should start by identifying all systems containing PII or regulated data, enable built-in audit logging features (most applications have logging that defaults to disabled), centralize logs in a secure location with automated retention, establish quarterly review schedules with documented findings, train personnel on interpreting audit data and escalating anomalies, implement role-based access so only appropriate users can view audit trails, and define procedures for generating audit trail reports with proper PII redaction when regulators or auditors request documentation. Many cloud-based systems include audit trail capabilities that don't require expensive infrastructure - leverage these rather than attempting to build custom solutions. The key is systematic implementation even at small scale, not sophisticated technology.
Audit trails often must reference PII to document what data was accessed, but they should not store raw sensitive values. Use non-identifiable reference numbers (Patient ID 84732 rather than "John Smith"), tokenized identifiers for financial accounts, role-based justification codes rather than detailed medical information, and hash values for sensitive identifiers that require matching without exposure. When generating audit trail reports for external sharing, apply permanent redaction to any remaining sensitive values while preserving timestamps, user IDs, action types, and other metadata that demonstrates compliance. The goal is creating verifiable records of activity without making the audit trail itself a target for data theft.
More About
Data Privacy
Ready to get started?
No credit card required
Start redacting for free
Cancel any time