TikTok paid €530 million (approximately $600 million USD) in GDPR fines in 2025 from Ireland's Data Protection Commission for violating Article 46 data transfer safeguards when transferring personal data to China. The penalty stemmed from inadequate protections for cross-border data flows - a failure in the controller-processor relationship where TikTok, as data controller, didn't ensure its Chinese processors maintained GDPR-compliant safeguards.
Half of all organizational records contain some form of PII, according to NIST benchmarks—yet many organizations lack complete inventories of what sensitive data they hold and where it's stored. That gap creates the conditions for breaches that expose millions to identity theft. When a phishing email arrives or a vendor requests customer data, does your team know whose responsibility it is to evaluate the risk?
The confusion is expensive. Over 53% of 2025 data breaches targeted customer PII like Social Security numbers, addresses, and account numbers. The average cost per record lost reached $160. Most of these breaches happened not because of technical failures, but because someone in the organization didn't know their role in protecting sensitive information.
This guide breaks down who is responsible for protecting PII at your company, which privacy controls are everyone's responsibility, how to delegate tasks safely without creating bottlenecks, and why phishing remains the top breach vector that every role must address.
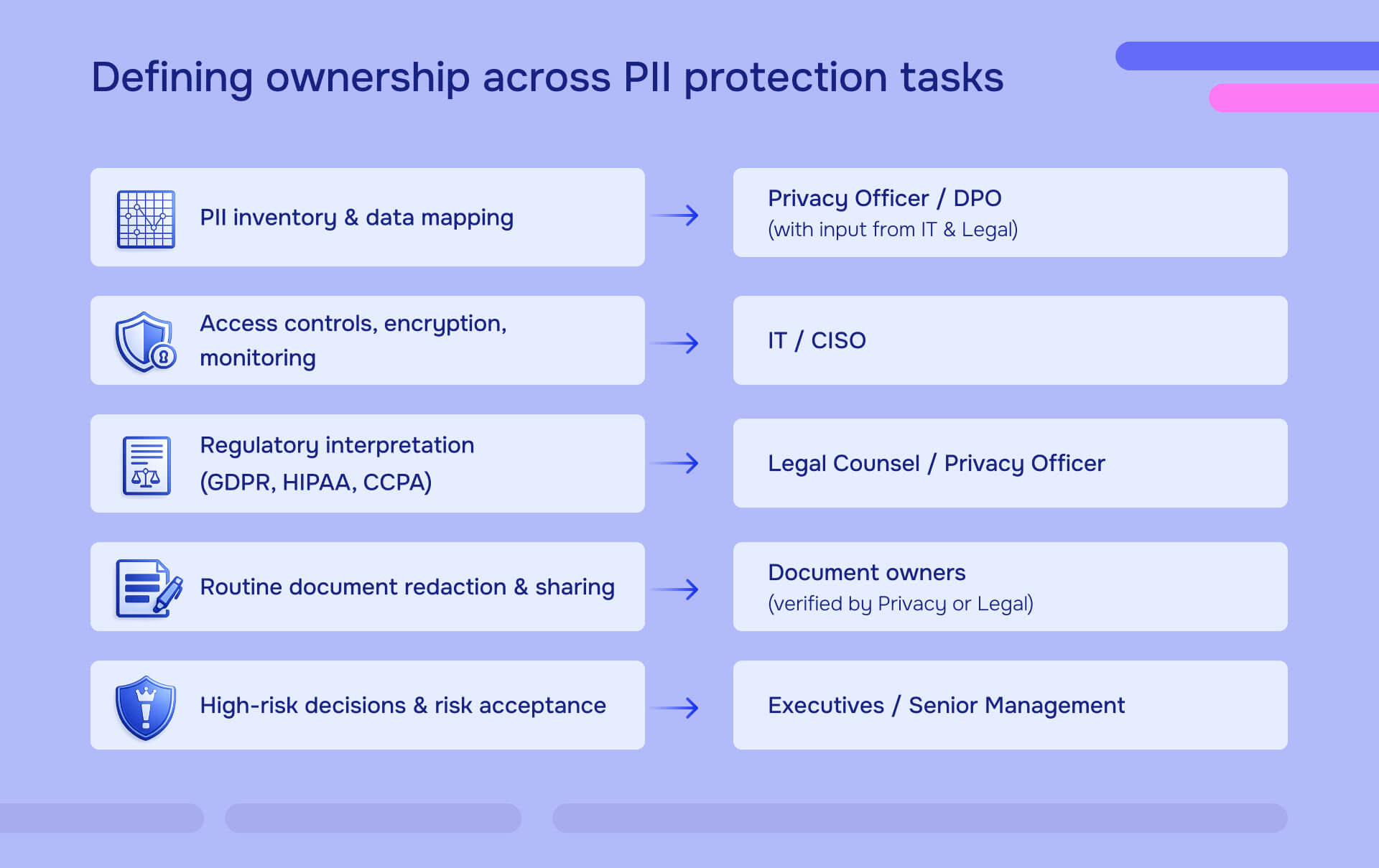
Who is ultimately responsible for protecting PII at your company
Ultimate accountability rests with senior leadership - boards and CEOs bear final liability when breaches occur. NIST SP 800-122 makes this explicit: senior management must allocate resources for PII protection and ensure that safeguards are implemented across the organization.
The legal structure matters. Data controllers decide purposes and ensure compliance under GDPR and CCPA - typically your company's executive team. Data processors handle execution under contracts - your vendors and service providers. When processors fail, controllers still face penalties.
Privacy officers and legal counsel define specific obligations. NIST guidance emphasizes consulting these roles to understand what laws apply to your PII holdings—Privacy Act, HIPAA, CCPA, GDPR, industry-specific regulations. They translate regulatory language into operational requirements.
CISOs manage the cybersecurity infrastructure that protects PII from threats like phishing, ransomware, and unauthorized access. This role implements the technical controls—encryption, access restrictions, monitoring systems—that prevent breaches.
But everyone shares vigilance. Every employee who handles PII has responsibility for spotting and reporting risks. The person who receives a phishing email, the manager who gets a vendor data request, the assistant who prepares documents for external sharing - they all make decisions that affect PII protection.
The breakdown creates problems. When everyone thinks someone else is responsible, no one takes ownership. When senior leadership assumes IT handles everything, they don't allocate sufficient resources. When IT assumes legal approves all data sharing, they don't implement proper access controls.
Clear role definition prevents this confusion.
Breaking down team roles and responsibilities
Different roles own different aspects of PII protection. The key is understanding what each role does, when to involve them, and how to escalate appropriately.
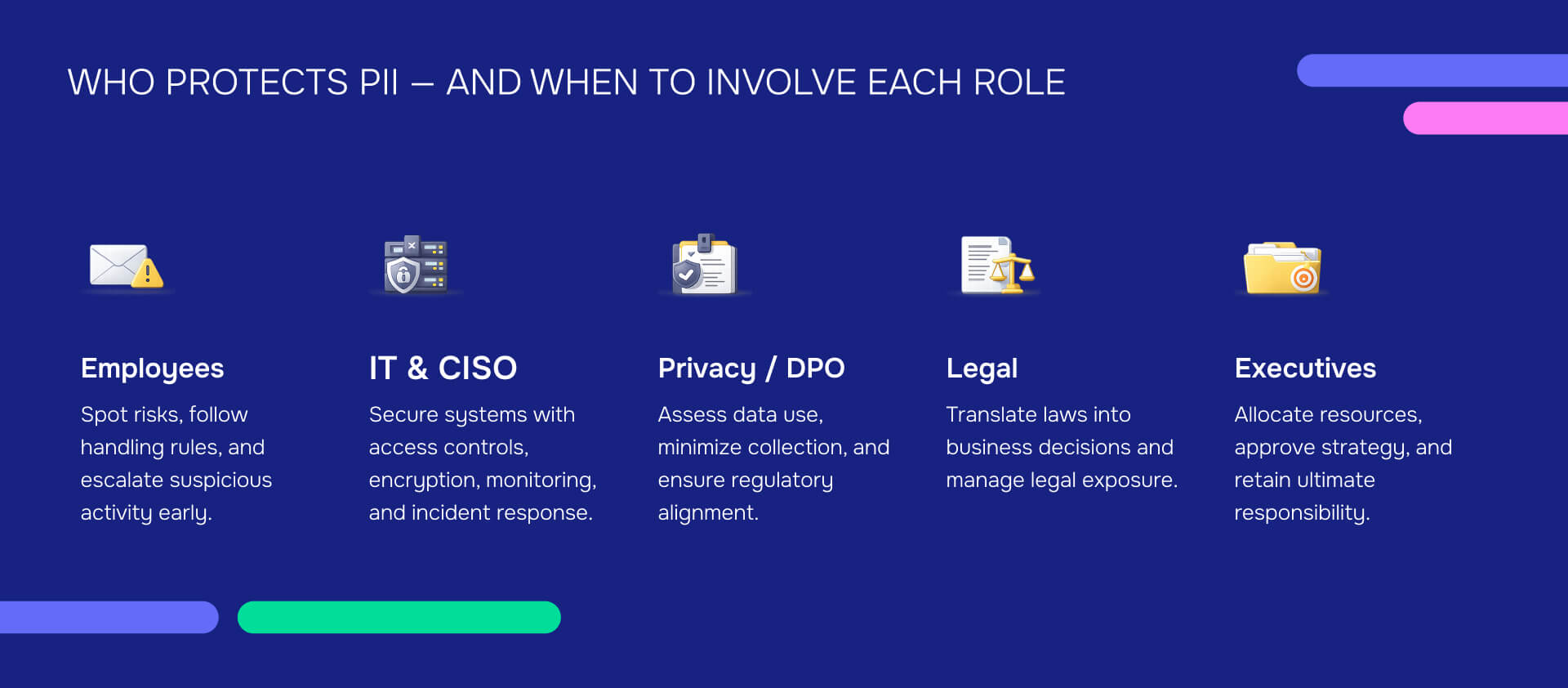
Employees: Everyone's responsibility
Every employee must follow PII safeguards as part of daily work. This isn't abstract policy - it's the person who spots a phishing email and reports it instead of clicking, the team member who questions why a vendor needs Social Security numbers, the manager who challenges excessive PII collection in a new form.
Training makes this practical. Employees need to recognize what constitutes PII, understand basic handling rules, know how to report concerns, and follow established procedures for sharing or storing sensitive data.
When to involve them: Immediately for anything suspicious. Don't wait to escalate phishing attempts, unexpected data requests, or situations where PII seems at risk.
IT and CISO: Technical safeguards
IT teams and CISOs secure systems through access controls, encryption, monitoring, and breach response. Delegate routine cybersecurity tasks here—implementing multi-factor authentication, configuring firewalls, managing user permissions, monitoring for intrusions.
This role owns the infrastructure layer. They can't make legal or policy decisions about what PII to collect or how to use it, but they control how systems protect whatever PII the organization holds.
When to involve them: For technical threats like phishing campaigns, system vulnerabilities, access control issues, or any indication of unauthorized access to PII.
Privacy officers and DPOs: Regulatory compliance
Privacy officers assess impacts, minimize collection, and conduct privacy impact assessments. For organizations under HIPAA, this role ensures compliance with Protected Health Information requirements. For companies subject to CCPA or GDPR, Data Protection Officers manage regulatory obligations.
These roles interpret how regulations apply to specific business activities. When you're launching a new product that collects customer data, the privacy officer determines what consent you need, what disclosures are required, and what security measures are mandatory.
When to involve them: Policy gaps, new data collection initiatives, vendor assessments, audits, or whenever you're unsure if an activity complies with privacy regulations.
Legal counsel: Interpretation and risk management
Legal counsel interprets laws and advises on compliance across jurisdictions. They handle questions about the Privacy Act, OMB guidance, state laws, contractual obligations, and liability exposure. They also advise on hiring consultants or engaging service providers who will handle PII.
Legal translates regulatory requirements into business decisions. When a regulation says you must implement "reasonable security measures," legal counsel defines what that means for your organization given your size, resources, and risk profile.
When to involve them: Cross-departmental policy revisions, major system integrations, vendor contracts involving PII, breach response, or any situation with potential legal exposure.
Executives and CEO: Resources and oversight
Senior management allocates resources and maintains ultimate responsibility per NIST SP 800-122 (Section 3.2, page 3-2). No amount of delegation removes this accountability. When a breach occurs, regulators look to the top—did leadership provide adequate budget, enforce policies, and ensure proper training?
Executives make the strategic decisions: how much to invest in security infrastructure, whether to collect certain types of PII, which markets to enter (each with different regulations), and how to respond when prevention fails.
When to involve them: High-risk projects, significant policy changes, budget decisions for security infrastructure, breach response coordination, or situations that could result in regulatory penalties or reputational damage.
What PII protection tasks are everyone's responsibility
Vigilance and reporting are everyone's responsibility. NIST emphasizes that while specialized roles implement specific controls, all personnel must remain alert to potential PII exposure.
The practical controls everyone owns:
- Spotting anomalies: Unusual data requests, suspicious emails, unexpected access attempts, vendors asking for information they shouldn't need.
- Following procedures: Using approved channels for sharing PII, encrypting sensitive documents, properly disposing of records containing PII, locking screens when away from desks.
- Questioning excessive collection: Challenging forms or processes that collect more PII than necessary. The person closest to the work often spots unnecessary data gathering before privacy officers review it.
- Immediate reporting: Flagging potential breaches, phishing attempts, or policy violations upward without delay. The cost of investigating a false alarm is trivial compared to the cost of ignoring an actual breach.
This shared responsibility doesn't mean everyone makes compliance decisions - it means everyone contributes to the intelligence system that catches problems before they become breaches. The administrative assistant who questions why a new vendor needs employee Social Security numbers might prevent a breach that the CISO never sees.
The breakdown happens when "everyone's responsibility" becomes "no one's responsibility." Clear escalation paths fix this: employees spot and report, specialized roles investigate and decide, management provides resources and oversight.
Is phishing responsible for PII data breaches
Phishing attacks caused over 300,000 healthcare data breaches yearly, with credential theft remaining the primary attack vector. Recent FBI and CMS warnings emphasize phishing as the top threat to PII security across sectors.
The mechanism is straightforward: an employee receives an email that appears to come from IT, a vendor, or management. The email requests login credentials, contains a malicious link, or includes an attachment with malware. One click grants attackers access to systems containing PII.
Healthcare proves especially vulnerable because Protected Health Information commands high black market prices and healthcare workers often operate under time pressure that makes them more likely to click without careful evaluation.
Every role prevents phishing differently:
- Employees receive training on spotting suspicious emails - odd sender addresses, urgent language demanding immediate action, requests for credentials, unexpected attachments. They report suspicious emails rather than deleting them, because one person's suspicious email might be targeting hundreds of others.
- IT and CISOs implement technical defenses: email filtering, multi-factor authentication that prevents credential theft from succeeding, monitoring systems that detect unusual access patterns, and regular security awareness training.
- Privacy officers ensure that breach notification procedures work when phishing succeeds. They maintain the documentation required to notify affected individuals and regulators within legal timeframes.
- Legal counsel manages the response when phishing leads to PII exposure—determining notification obligations, coordinating with law enforcement, managing public communications.
- Executives fund the infrastructure and training that prevents phishing and respond decisively when prevention fails.
The shared responsibility model applies directly: technical controls reduce phishing success rates, but employee awareness provides the final defense. NIST SP 800-122 emphasizes annual training as essential (Section 4.3, page 4-3), because phishing techniques evolve faster than technical defenses can adapt.
How to delegate PII protection tasks safely
Delegation prevents bottlenecks, but poor delegation creates gaps where no one owns critical tasks. The framework: delegate execution, maintain oversight, escalate based on risk.
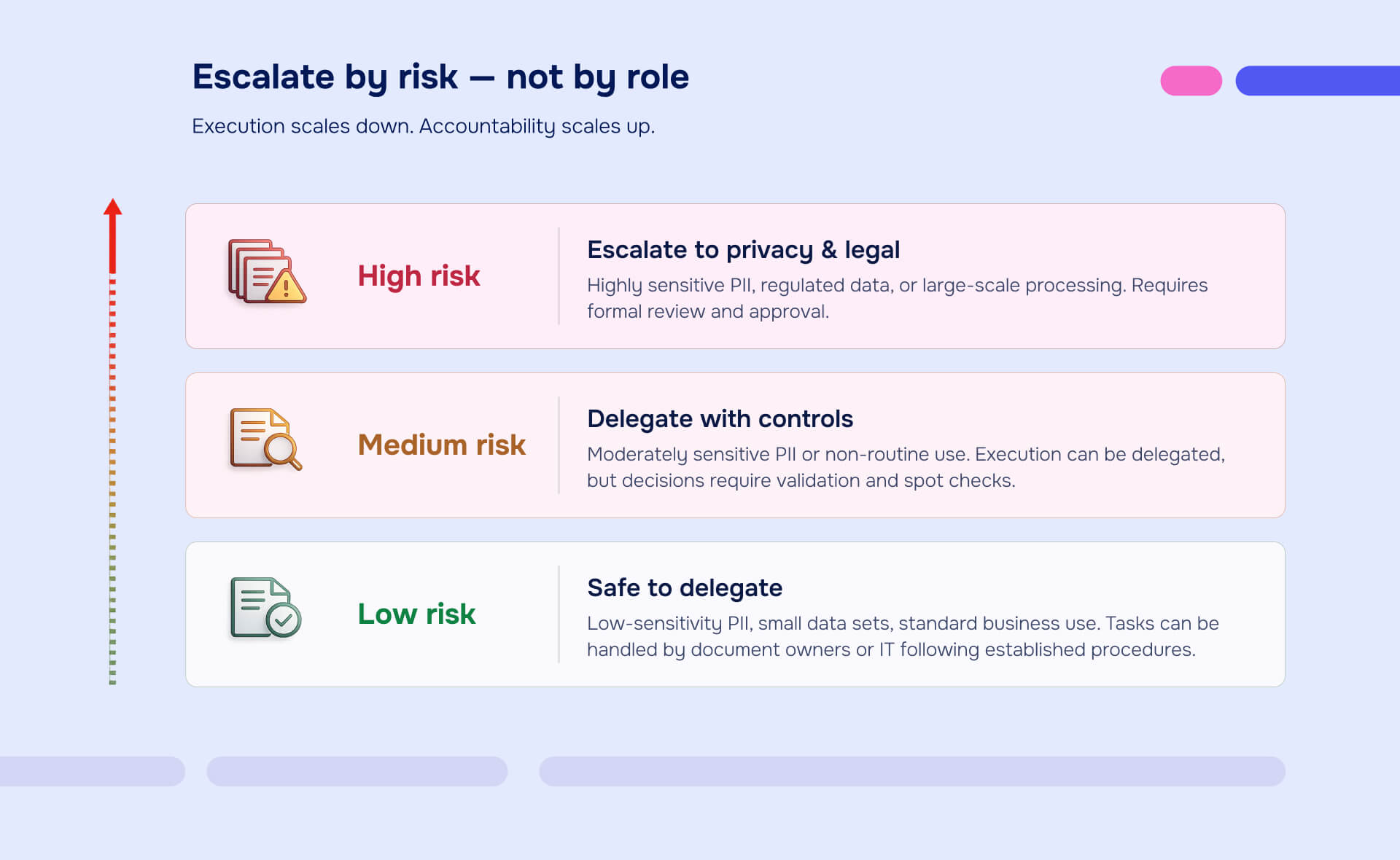
Routine tasks that don't require higher approval
- Low-risk data handling: Document owners and IT teams can handle routine PII tasks—preparing reports with properly redacted sensitive information, managing access to systems, implementing standard encryption protocols, following established procedures for data sharing.
- Phishing training and response: IT can manage ongoing awareness programs, email filtering configuration, and initial incident response for suspected phishing without executive involvement for each incident.
- Standard vendor assessments: For vendors who won't access PII or who are using established, approved platforms, routine due diligence can happen at operational levels.
Use NIST's risk factors for quick triage: identifiability (does it directly identify individuals?), quantity (hundreds of records or millions?), context (routine business use or novel application?), sensitivity (addresses or medical records?).
Low identifiability, small quantity, routine context, low sensitivity—delegate freely. Any factor elevated—escalate.
When to involve specialized roles
Data integration projects: New systems that combine data sources require privacy officer and legal review, particularly if they create new ways to identify individuals or enable new uses of existing PII.
Regulated data: HIPAA-covered Protected Health Information always requires privacy officer involvement. Don't delegate HIPAA compliance decisions to IT alone.
Cross-border transfers: GDPR and other international regulations create complex requirements for moving PII across borders. Legal counsel must evaluate these before implementation.
Third-party access: When external vendors, contractors, or service providers will access PII, privacy officers and legal counsel should review contracts, assess security measures, and document the data processing agreement.
High-volume processing: Projects involving millions of records, even if routine, warrant specialized review because the impact of errors scales with volume.
What requires executive decision-making
- Resource allocation: Only executives can decide to fund security infrastructure, hire specialized roles, or prioritize PII protection over competing business needs.
- Risk acceptance: When compliance is too expensive or operationally difficult, executives must explicitly accept the risk. They cannot delegate this decision.
- Breach response strategy: The decision to notify affected individuals, engage with media, or cooperate with regulators requires executive approval because it affects reputation and legal exposure.
- Policy exceptions: Requests to violate established PII policies for business reasons must reach executives who can weigh business value against compliance risk.
When external consultants make sense
Most organizations don't need consultants for basic PII protection. NIST guidance assumes internal resources handle routine compliance.
Consultants add value when:
- You lack internal privacy officers or DPOs and face immediate compliance deadlines
- You're entering new regulatory environments (expanding to EU markets requiring GDPR compliance)
- You're responding to a breach and need specialized incident response expertise
- You're implementing complex technical controls beyond your IT team's capabilities
Don't hire consultants to avoid building internal capability. Privacy and security require ongoing attention that consultants can't provide intermittently.
Who performs PII redaction in different contexts
Redaction is a specific PII protection task with clear delegation rules based on document type and regulatory context.
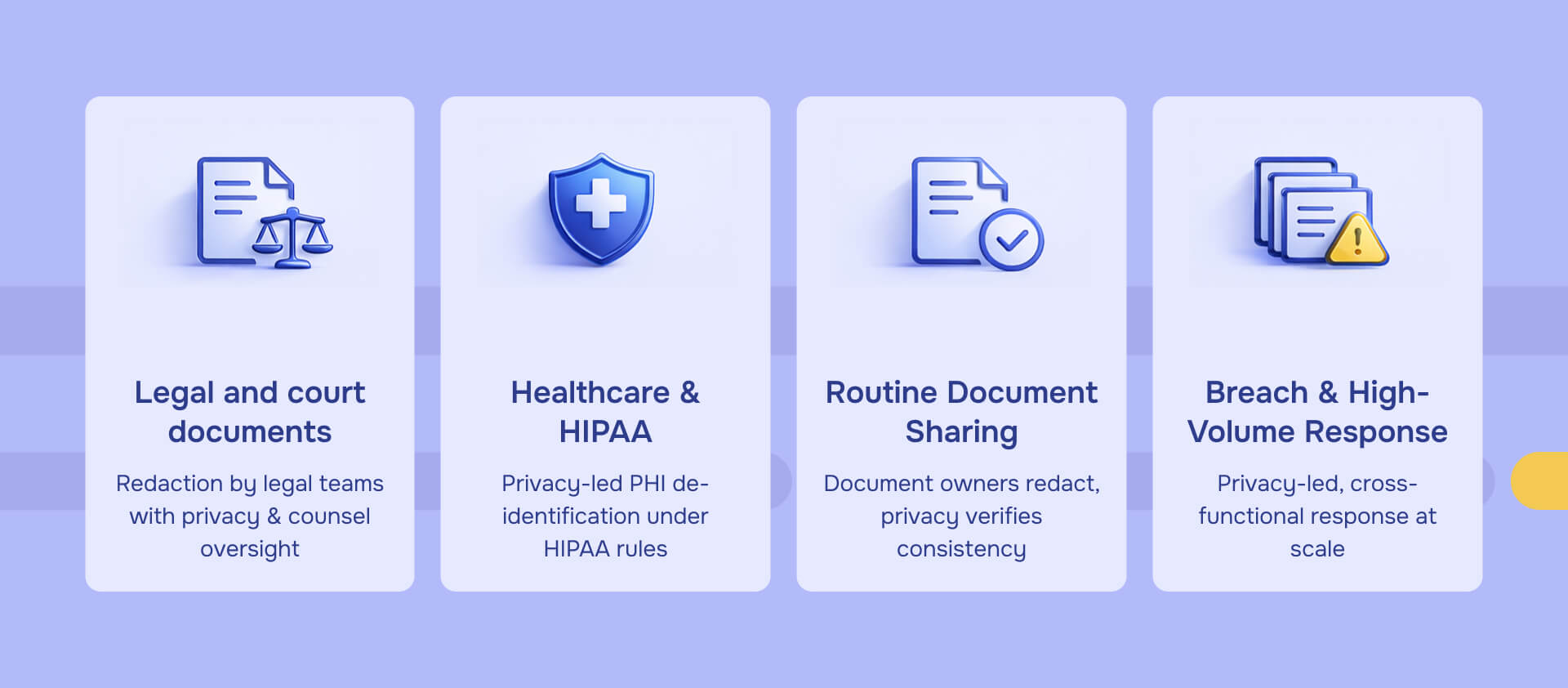
Legal and court documents
Legal and compliance teams perform redaction for FOIA requests, discovery responses, and court filings, with privacy officer oversight and legal counsel approval. Federal agencies redact using specific FOIA exemptions for law enforcement records, medical information, and personal privacy protection.
Why this matters: Court documents have admissibility requirements and audit trail needs that make redaction errors particularly costly. Metadata that remains in "redacted" PDFs can be discovered by opposing counsel, exposing information you intended to protect.
1,732 U.S. breaches in the first half of 2025 exposed millions of Social Security numbers, often because metadata persisted after visual redaction. Simple black boxes over text don't remove the underlying content—the text remains in the file structure, fully recoverable.
Healthcare and HIPAA compliance
Compliance and privacy officers perform PHI de-identification, sometimes delegating to trained IT staff under supervision. HIPAA requires removing 18 specific identifiers before disclosure: names, geographic subdivisions smaller than state, dates (except year), phone numbers, fax numbers, email addresses, Social Security numbers, medical record numbers, health plan beneficiary numbers, account numbers, certificate/license numbers, vehicle identifiers, device identifiers, web URLs, IP addresses, biometric identifiers, full-face photos, and any other unique identifying characteristics.
Expert determination applies when statistical methods de-identify data while preserving analytical value. This requires specialized knowledge that most IT teams don't possess.
Routine document sharing
Document owners work with IT teams to redact routine reports and communications, with privacy office verification for consistency. This includes preparing board reports, vendor communications, and internal documents that will be shared beyond the team that created them.
The verification step catches common errors: inconsistent redaction (some instances of a name redacted, others visible), metadata that reveals redacted content, formatting that allows text recovery, and incomplete coverage of PII types.
High-volume or breach response situations
Cross-functional teams coordinate large-scale redaction - IT, legal, CISO, with privacy officers leading and executives funding resources as needed. Automation becomes necessary when you're processing thousands of documents, but human verification remains essential.
Breach response redaction is particularly urgent. When you've discovered unauthorized PII exposure, you need to assess what was exposed (requiring un-redacted review) and prepare redacted versions for notification and regulatory reporting (requiring rapid, verified redaction).
The coordination challenge: legal needs redacted versions for court filings, privacy needs them for regulatory notification, IT needs them for system cleanup, and management needs them for public communications. One redaction process serving multiple needs requires clear ownership—typically privacy officers coordinate with legal counsel approval.
Key redaction triggers that require immediate action
Certain situations demand redaction regardless of who performs it:
External document sharing: FOIA requests, court discovery, regulatory submissions, public records releases. OMB M-07-16 mandates minimization before external sharing.
Compliance requirements: HIPAA demands de-identification for research use, CCPA requires it for data sharing with processors, GDPR mandates it for legitimate interest processing.
High-impact PII: Social Security numbers, medical records, financial account numbers, biometric data—these warrant redaction even for internal use when recipients don't need that level of detail.
Breach response cleanup: After discovering unauthorized access, redacted versions prevent additional exposure during investigation and remediation.
The trigger that teams miss: metadata and hidden content. FTC enforcement actions increasingly target organizations that share documents with PII embedded in metadata, even when visible text is properly redacted.
Traditional PDF redaction tools add visual masks without removing underlying data. Copy the text, paste it into a word processor, and everything you thought you redacted appears intact. Search the document for a supposedly redacted Social Security number, and it shows up in results.
Proper redaction requires:
- Permanent removal of text from document structure
- Complete metadata stripping
- Verification through copy-paste and search tests
- Audit trail documentation for compliance purposes
Implementing clear PII protection responsibilities
Confusion about PII protection creates the conditions for breaches. Clear role definition, proper delegation, and documented procedures prevent the gaps where no one takes ownership.
Start with an annual PII inventory. NIST and OMB require knowing what PII you hold (Section 2.2, page 2-2), where it's stored, who accesses it, and why you need it. Purge unnecessary PII immediately - you can't breach data you don't hold.
Train on roles, not just threats. Employees need to know what they're responsible for (spotting and reporting), what IT handles (technical safeguards), what privacy officers do (regulatory compliance), what legal counsels (risk interpretation), and when to escalate to executives (high-risk decisions). Generic "security awareness" training doesn't create this clarity.
Establish escalation paths for common scenarios:
- Phishing email received → Report to IT immediately
- Vendor requests customer data → Privacy officer reviews necessity and legal approves contract
- New system will store PII → Privacy impact assessment before implementation
- Document needs external sharing → Redaction by appropriate role with verification
- Possible breach discovered → CISO coordinates immediate response, legal manages notification obligations
Build verification into delegation. When IT performs routine redaction, privacy spot-checks for consistency. When document owners prepare reports, someone verifies PII removal. When vendors process PII under contract, regular audits confirm compliance.F
Document everything. NIST emphasizes audit trails - who redacted what, when, under what authority, and what verification occurred. This documentation becomes essential during regulatory investigations or litigation.
The most important step: executives must demonstrate that PII protection is a priority through resource allocation and consequence enforcement. When leadership treats compliance as a formality rather than a requirement, confusion multiplies and breaches follow.
Organizations that define roles clearly, delegate appropriately, and implement proper verification procedures don't just avoid fines - they build the trust that comes from actually protecting the information customers and employees share with them.







