The public release of the Epstein files was supposed to be a transparency milestone. Instead, it became a major redaction failure that raised questions about how sensitive information was handled. Millions of pages of documents related to convicted sex offender Jeffrey Epstein are being made public under the Epstein Files Transparency Act. But reporters, data analysts, and online sleuths quickly discovered that the redaction process failed in fundamental ways.
In this article we look at why the redacted files were flawed, how poor redaction exposed hidden data, and what organizations must do to avoid similar failures.
Why are the Epstein files redacted?
Understanding why redaction was necessary helps explain why the failures were so problematic. he Epstein files required redaction for several critical reasons:
- Victim privacy protection: Many documents contain names, addresses, and personal details of victims, some of whom were minors at the time of the abuse. Federal law requires protecting victim identities in sensitive criminal cases, especially those involving sexual exploitation. Exposing this information could cause additional trauma and privacy violations for survivors who never chose to be public figures.
- Ongoing investigations: While Epstein died in 2019, investigations into his network and potential co-conspirators continued. Certain details needed to be redacted to avoid compromising active law enforcement operations, witness cooperation, or prosecutorial strategies in related cases.
- Third-party privacy: Not everyone mentioned in the documents was involved in criminal activity. The files contain names of employees, service providers, business associates, and others whose connection to Epstein was tangential or innocent. Publishing their information without context could unfairly damage reputations.
- National security considerations: Some materials reportedly touch on international connections and diplomatic matters that could have national security implications if disclosed without proper review.
- Legal standards and court orders: Various court proceedings over the years resulted in sealed documents and protective orders. The redaction process had to balance the new transparency mandate with existing legal protections and privacy rights established through litigation.
The tension between transparency and protection created a complex redaction challenge-one that required sophisticated tools and careful judgment. Unfortunately, the DOJ’s implementation fell short of these requirements, leading to the failures detailed below.
How redacted Epstein files were released?
Under a federal law passed in late 2025, the U.S. Department of Justice (DOJ) was required to publish all unclassified Epstein-related files by December 19, 2025. The aim was to increase accountability while protecting victim privacy. The files included court documents, images, contact lists, investigative records, and other materials linked to Epstein and his network.
Many were marked with heavy redaction blocks to remove sensitive personal information. Despite this, the initial public release drew swift criticism from lawmakers, survivors, and transparency advocates because the files were incomplete, heavily obscured, and technically flawed.
1. Redaction technical failures: Black boxes that did not work
The most talked-about problem with the Epstein redacted files was not just what was hidden, but how easy it was to undo the redaction. Investigators and ordinary readers found that by simply copying and pasting text from the PDF into a plain text editor, the supposedly redacted sections became visible.
This suggests the DOJ used superficial black boxes instead of permanent redaction that removes underlying data. In other words, the files appeared redacted on screen, but the underlying text remained intact in the file data. This type of error happens when tools like Adobe Acrobat are used to draw black bars over text without deleting the associated characters from the document.
These mistakes undermine the very purpose of redaction. When sensitive names, dates, or details can be uncovered with a basic copy-paste trick, the redaction is not secure.

2. Inconsistent and incomplete redaction
A second major issue was inconsistency in what was redacted in Epstein files, and what was left visible. Many files were released with heavy redaction, but lawmakers and advocates criticized the approach as incomplete because large swaths of materials were withheld entirely or released in a form that offered little usable information. Several hundred pages were fully redacted with no visible content at all, leaving public observers wondering what was being protected and why.
Additionally, the partial release raised legal concerns because the Transparency Act required explanation for every redaction applied. Critics said the DOJ was failing to meet both the letter and spirit of the law by releasing a limited set of documents and continuing to hold back others while applying inconsistent redaction criteria.
3. Metadata and unintended exposure
Another serious redaction failure was metadata left in the files. Metadata can reveal:
- Author names
- Edit history
- Internal comments
- File properties that contain original text
When metadata is not sanitized, a redacted document can still contain sensitive information that was never removed. Metadata redaction is a core part of secure redaction best practices, but evidence suggests that many Epstein files were not fully processed to remove this hidden data. This problem - unremoved metadata - contributed to public concern that the redaction process was rushed or incomplete.

4. Partial release and missing files
The effort also faced criticism for failing to deliver all required files by the statutory deadline. The DOJ acknowledged that more than a million potentially relevant documents still needed review and redaction and that the process would take additional weeks. Critics say this delay undermined public trust and suggested mismanagement of the redaction workflow.
Incomplete and delayed releases fuel perception problems that go beyond redaction quality. The public expects full compliance with transparency mandates, and partial delivery of documents with heavy redactions sends mixed signals about institutional accountability.
Why these redaction failures matter?
- Exposure of hidden personal data: Redaction is intended to protect private individuals, including survivors who are not public figures. When redaction can be undone easily, those protections fail.
- Undermining transparency: When redaction is applied incorrectly - with superficial black boxes and incomplete metadata removal - it becomes harder to trust the document release. Instead of clarifying what happened, flawed redaction raises new questions.
- Legal and compliance risk: Government agencies and private organizations alike can face legal exposure if they publish confidential data without proper redaction safeguards. Secure redaction is both a legal requirement in many jurisdictions and a best practice for compliance.
Read also: Most embarrassing redaction failures in history
What proper redaction must include?
To avoid the problems seen with the unredacted Epstein files, secure redaction must be done with appropriate tools and processes.
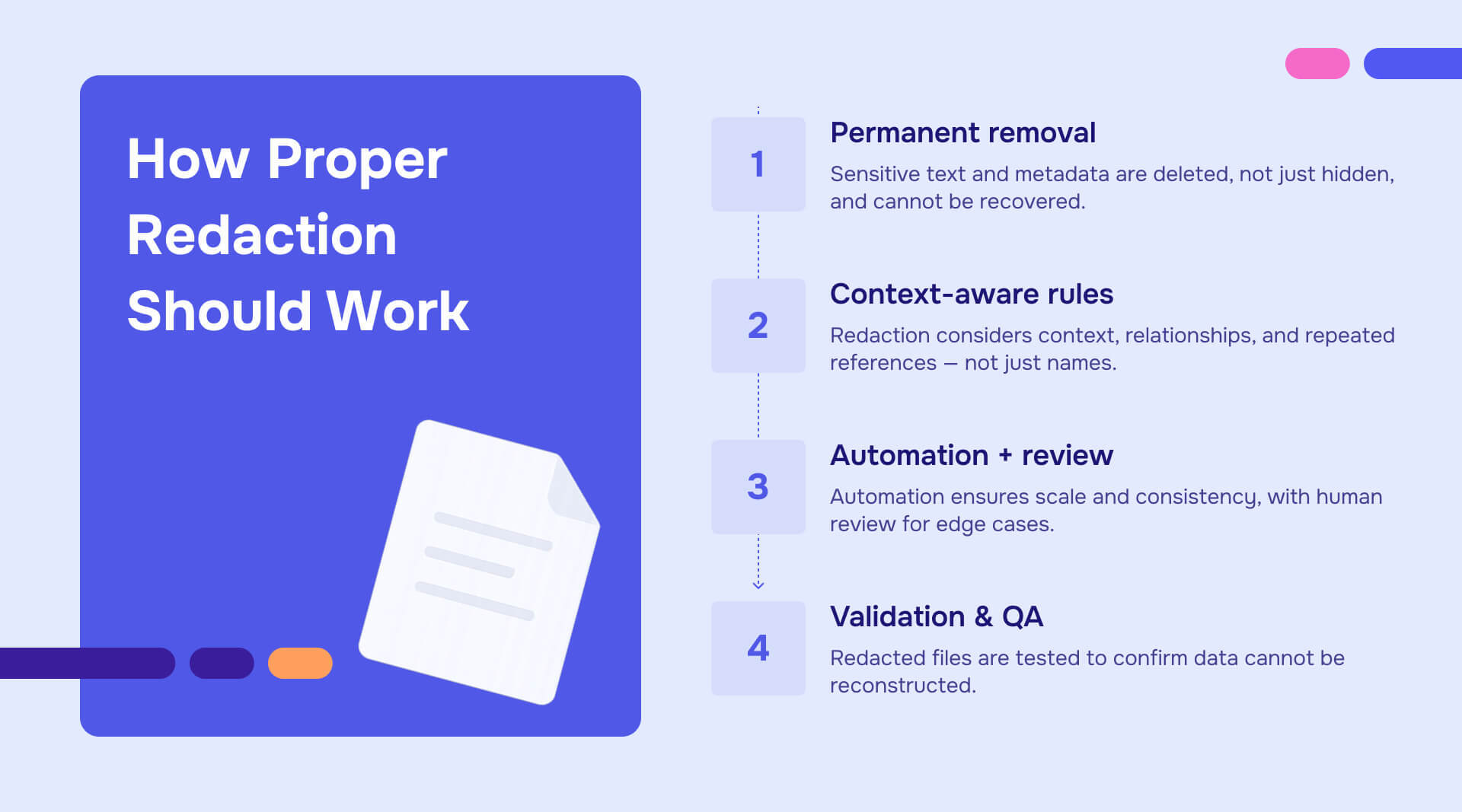
- Permanent removal of sensitive data: Strong redaction permanently deletes hidden text and metadata. The text should not be recoverable through copy-paste or file inspection.
- Context-sensitive redaction rules: Simple pattern matching for names is not enough. Proper redaction considers:
- Relationships
- Contextual identifiers
- Multiple occurrences of the same person
- Inferred data that could expose sensitive information
- Automation with human review: Large document sets require scalable automated redaction for speed and consistency, followed by expert human review to catch edge cases.
- Validation and QA: Final review and quality assurance are essential. This step ensures that redaction has been applied correctly and that underlying data cannot be reconstructed.
Read our complete guide on how to redact a PDF
What can organizations learn from the Epstein redaction failures?
Whether in government, legal practice, journalism, or corporate settings, redaction must balance transparency with protection of sensitive information. The Epstein redacted files show that failing to use secure redaction methods can lead to:
- Exposure of confidential data
- Loss of trust by stakeholders
- Legal challenges and compliance risk
- Harm to individuals the redaction was meant to protect
Secure redaction is not a surface-level edit. It is a deliberate process with clearly defined tools, rules, and validation steps.
Read also: Top 10 rules for redacting documents
Final thoughts
The Epstein files controversy is a reminder that redaction is a technical and ethical responsibility. Superficial techniques that overlay black boxes without removing data are insufficient. Redaction must be implemented with secure tools, strong policies, and careful quality controls.
Redactable’s approach to redaction is built on these principles. We help organizations move beyond cosmetic redactions to methods that truly protect sensitive information and support transparency.







